Cloud Security
THIS OFFICE 365 PHISHING EMAIL CAN EASILY EVADE YOUR FIREWALL SECURITY
A cybercriminal group is deploying a phishing campaign that uses a fraudulent website to collect Microsoft Office 365 credentials by creating html snippets stored locally and remotely. This method involves integrating various hidden HTML pieces into JavaScript files to get the fake login interface in which the victim delivers their sensitive information.
Potential victims receive an attachment disguised as an Excel document that is actually an HTML document with a URL-encoded piece of text. A report prepared by Trustwave researchers notes that decoding this text makes it possible to find more coded content.
A subsequent analysis noted the presence of a couple of links redirecting to two JavaScript files hosted on “yourjavascript.com”, which has recently been associated with other phishing campaigns.
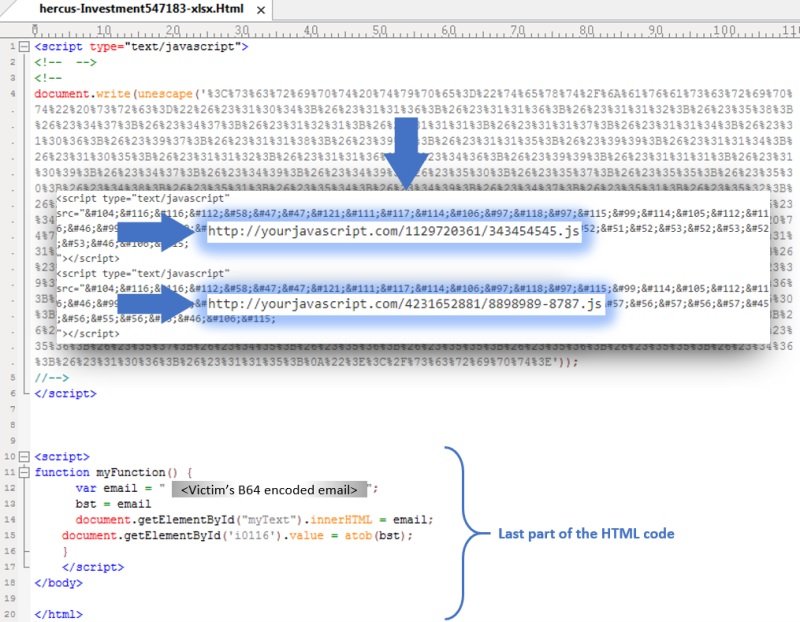
These JavaScript files contained two blocks of encoded text to hide HTML code, URL, and Base64 encoding. One of these files contains a section of the phishing website and the code to validate the victim’s email address and password. On the other hand, the second JavaScript file contains the “send” function, located through the form and the code to trigger a pop-up message informing victims that their connection had failed and they had to authenticate again.
Trustwave experts decoded nearly 400 lines of HTML code, grouped into five snippets in the two JavaScript files and one in the attachment sent to the victim, resulting in the Office 365 phishing website as if they were the pieces of a puzzle.
Specialists mention that the strangest thing about this campaign is that malicious code is downloaded in hidden fragments from a remote location and then assembled to a local location: “This allows threat actors to bypass protection mechanisms like Secure Email Gateways.”
Finally, Trustwave mentions that the URL that receives the stolen credentials in this campaign remains active, so office 365 account administrators need to stay on top of these security risks, ignoring any email sent by unknown users and trying not to visit potentially malicious websites.
To learn more about information security risks, malware variants, vulnerabilities and information technologies, feel free to access the International Institute of Cyber Security (IICS) website.
RED DEAD REDEMPTION 2 WAS FINALLY CRACKED. TORRENTS AVAILABLE IN FORUMS
Although many game users and hackers believed it was indecipherable due to its dual protection with Digital.AI and Social Club, it has finally been announced that Red Dead Redemption 2 (RDR2) has been hacked, making it available on various torrent forums. The information has been confirmed by CrackWatch, a platform dedicated to tracking the status of video games in terms of piracy.
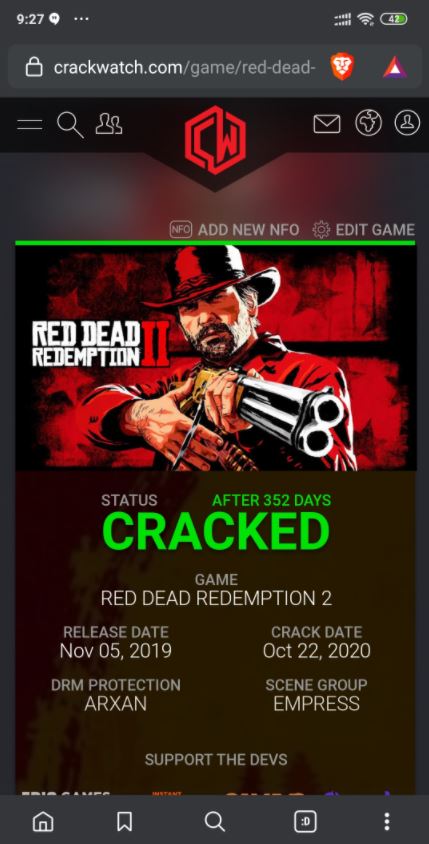
The creators of RDR2 tried to innovate in video game protection by creating a sophisticated combination of DRM, similar to the measures implemented in the latest Ubisoft releases. This mechanism allowed keeping the game safe from hackers for almost a full year, although hacking groups have finally achieved their goal.
This is a worrying fact not only because it has compromised the security of RDR2, since the industry believes that employing similar methods, piracy groups will be able to compromise other video games protected by the same mechanism. This attack, known as bypass crack, is one of the most important resources available to threat actors.
On Ubisoft, multiple games could be exposed by this attack method, including Watch Dogs Legion, Assassin’s Creed Valhalla, among others, which use Denuvo security technology and in some cases VMProtect. The number of games committed over the last few days could be updated as soon as possible.
HOW TO HACK NUCLEAR REACTOR ISOLATED NETWORK WITH A SIMPLE GPU & RADIO SIGNALS
ORIGINAL CONTENT: https://www.securitynewspaper.com/2020/04/23/how-to-hack-nuclear-reactor-isolated-network-with-a-simple-gpu-radio-signals/
Isolated systems and devices (known as “air-gapped” systems) have been the subject of analysis by researchers and threat actors for years, as network perimeter security specialists said, which has generated a large number of variants and attack scenarios to compromise these systems.
One such attack is the one known as Stuxnet, a computer worm used at a nuclear company’s facility in Iran nearly ten years ago. That was the first time a hacker group showed that it is not impossible to compromise an air-gapped system.
Network perimeter security specialists mention that, on that occasion, threat actors (the attack was attributed to Israeli intelligence agencies) could have employed a malware variant that compromised centrifuges at a uranium enrichment plant. In this regard, ethical hacking specialist Mikhail Davidov asked a question: while it is possible to inject malicious code into an air-gapped system, is it possible to extract data from these networks?
The answer to this question could be on the radio spectrum. Using a radio, antenna, and script from his own development, the hacker figured out how to use a signal emitted by a graphics processing unit (GPU) from a computer connected to an air-gapped network and extract sensitive data. The expert posted his findings on a blog shared exclusively with the firm CyberScoop.
The attack was launched from behind a wall and more than 15 meters away from the target computer. The expert used an antenna to scan the radio frequency spectrum for variations that could be used to extract data. Realizing that the GPU emits a type of signal that can be manipulated, the ethical hacker developed a script to perform this action. By controlling the duration of each GPU radio transmission, and using a radio capable of capturing this signal, it was able to complete the extraction of data from the page.
“When I thought about extracting data from air-gapped networks, I came to this conclusion. Many times we have to think about any possible scenario of usefulness for threat actors and discard or confirm those possibilities in a controlled environment,” the network perimeter security expert says.
According to Davidov, this research is also an invitation to the cybersecurity community to take a more proactive approach to signals emitted by computer systems and the possibility of them being compromised. The International Institute of Cyber Security (IICS) mentions that national intelligence agencies should also consider this attack vector.
Grandpa Turned Hacker Tried to Send Malware to US DOE Employees
Former US NRC employee sent spear-phishing emails to 80 other US DOE employees containing an inert virus.
Charles Harvey Eccleston, 62, has pleaded guilty to sending spear-phishing emails to US Department of Energy (DOE) and the US Nuclear Regulatory Commission (NRC) employees in an attempt to infect them with malware that could be leveraged by foreign intelligence agencies to hack into US government computers.
The whole story starts in 2010 when Eccleston was laid off from the US NRC, and moved to Davao City, Philippines, one year later, in 2011.
According to the US Department of Justice, three years later, in 2013, Eccleston entered the embassy of an unnamed country in the Manila, Philippines, and offered to sell 5,000 email accounts belonging to employees of the US DOE.

Eccleston tried to sell a list of government email addresses to a foreign state
Eccleston said he wanted $18,800 (€17,200) for the emails accounts, which he said were “top secret,” and if the embassy would not buy them, he would go to the embassies of China, Iran or Venezuela instead.
Embassy officials tipped off the FBI, who sent an undercover agent to negotiate a deal with Eccleston.
During subsequent meetings, Eccleston sold a thumb drive containing 1,200 email addresses to the undercover FBI agent for $5,000 (€4,600). This happened on November 7, 2013, and the FBI agent confirmed that most of the email addresses were publicly available.
In the same meeting when this transaction took place, Eccleston also highlighted the fact that the email list would allow attackers to infect computers with a virus that would allow a foreign country to access sensitive government information, or even shut down NRC servers.
Eccleston tries his hand at running a spear-phishing campaign
On June 24, 2014, Eccleston had a second meeting, with a different undercover agent. Eccleston said he had another 30,000 email addresses belonging to DOE employees, and even offered to craft a spear-phishing campaign to target some of the individuals on the list.
The former DOE employee selected a few individuals from his list and crafted a spear-phishing email that advertised a conference which he knew DOE employees would be interested in.
On Jan. 15, 2015, Eccleston sent 80 spear-phishing emails to his former colleagues containing an inert virus he received from the FBI agent. The emails reached individuals across the US and even laboratories associated with nuclear materials.
Philippine authorities arrested Eccleston on March 27, 2015, when he was meeting with the undercover agent to receive an $80,000 payment for his endeavor. He was later deported to the US and has now admitted his crimes.
Eccleston faces a maximum of ten years in prison and financial penalties, but because of his age and previous records, according to the advisory federal sentencing guidelines, he’s likely to receive a prison term of 24 to 30 months and a fine of up to $95,000.
The grandpa turned hacker will receive his sentence in Washington on April 18, 2016.
Source:http://news.softpedia.com/
HOW TO IMPLEMENT ENTERPRISE DATA PROTECTION SERVICES AND SOLUTIONS ?
There is an increase in people who have been victims of identity theft and unauthorized use of credit cards because of many companies that handle data irresponsibly. According to many studies done by a personal data protection company in countries such as Mexico, Brazil, United States, Colombia, Argentina, India, the personal data protection & privacy is a primary concern of the people, thus failure to comply with the regulatory framework can be an obstacle and can cause loss of business opportunities.
The personal data represents all the information of a person which affirms his/her identification. Personal data includes place of birth, place of residence, academic, employment, professional career, marital status, age, health, sex life, physical characteristics, political ideology, and other aspects. The personal data can help a person to interact with business and/or organizations for their services. This exchange of information causes economic growth and improvement of services.
To resolve this problem privacy & personal data protection law was adopted in countries such as Mexico, Argentina, India and others some years ago with the purpose of protecting citizens from personal data misuses and abuses that happen every day by companies and/or organizations. The personal data protection law recognizes and protects the rights that people have to access, update and correct their personal data that has been collected as well as the right to oppose personal data processing by public or private entities. The personal data that’s involved in national security, national defense, intelligence and population censuses – housing information are not considered part of personal data protection law.
According to a personal data protection company, now all entities that handle personal data will be forced to consider the right to privacy and will need to adapt to regulations which will ensure safe treatment of personal data. The privacy & personal data protection act also gives people the right to request for all their personal data that a company has. Thus generating the need to implement personal data protection solutions, policies for cancellation and removal of personal data. Companies and/or organizations that do not comply with this law will face sanctions & fines.
There are many advantages of implementing personal data protection solutions. For instance the European privacy & personal data protection law approves the transfer of personal data of European citizens to a third country that has an adequate level of data protection system established for such information, depending upon the nature of the data, the purpose, duration of processing and safety standards. If a country adapts to the international privacy & personal data protection regulations, there are possibilities of exponential increase in foreign investments in that country.
IMPLEMENTING PRIVACY & PERSONAL DATA PROTECTION LAW
Companies and/or organizations must comply with the statutory obligation of implementing personal data protection system. According to various enterprise data protection services consultants, compliance with legal obligations in the field of data protection is essential. Data protection agencies have big teams of inspectors to make an audit of personal data protection system and apply fines along with sanctions, through a complaint of any affected person. Points to consider while implementing privacy & personal data protection law:
• All the personal data processing systems belonging to companies and/or organizations must be registered with the data protection agency. The registration must submit information such as name and title of the person responsible, purpose of the system, the type of the personal data processed, process of acquiring, process of updating data, methods of interrelating data, duration of holding data and personal data security solutions implemented.
• When the companies and/or organizations get personal data, all the interested parties must be advised prior about the existence of a personal data protection system, data treatment process, the purpose of collecting data, the recipients of data, the rights of access, rectification, cancellation and opposition to data processing.
• Companies and/or organizations will designate a person responsible for personal data processing systems.
• Comply with the personal data protection policies and regulations as well as standards for enterprise personal data protection services.
• Process personal data only when they relate to the purpose for which they were collected.
• Implement appropriate enterprise data protection solutions to manage all the requests for access, rectification, cancellation of personal data; also enterprises must provide data protection training course to all public servants.
• Implement security measures for via enterprise data protection services and inform about the changes to the data protection agency.
• Modify personal data when appropriate, correcting the incorrect data and completing the partial data. All these changes must be logged in a security document.
• The client has the right to request the correction or deletion of his personal data.
• Coordinate and review the implementation of data protection solutions by enterprise data protection company and make sure it’s done as per the data protection norms.
• Implement specific set of policies for the management and maintenance of the personal data processing system.
• Develop a personal data protection training course plan. All the professionals of data protection department must take data protection training.
• Conduct or regularize the execution of the operations of data processing systems implemented by any personal data protection company.
• Inform the client when obtaining their personal data about personal data processing systems and data protection solutions implemented by personal data protection companies.
SECURITY MEASURES FOR DATA PROTECTION
As per experts from personal data protection company, businesses and/or organizations should establish technical and organizational security measures to ensure the confidentiality and integrity of personal data with the objective of preserving the data protection rights, against modification, loss, transmission and unauthorized access. All the data security measures should be implemented with respect to the highest degree of protection of personal data. The security measures should be according to following types of security:
Physical Security: This includes the protection of facilities, equipment to prevent accidental incidents cases or force majeure.
Logical Security: This includes measures for identification and authentication of people or users authorized to access and modify personal data.
Applications: It represent the permissions which personal data processing system should manage, to ensure proper use of data, preventing the participation of non-authorized users, separation of environments and penetration testing controls.
Encryption: This includes implementation and use of encryption algorithms, keys, passwords, and specific protection measures to ensure the integrity and confidentiality of the sensitive personal data.
Network Communications: This refers use of enterprise data protection services that includes use of network monitoring system that constantly monitors network communications and blocks any kind of suspicious activity or security breach.
According to experts from enterprise data protection company, following are the security checks which are mandatory for all personal data processing system to ensure compliance with the privacy & personal data protection law:
• Implementation of the security policies.
• Maintaining documentation of roles and responsibilities of personnel responsible for the processing of personal data.
• Access and incidents logging.
• Identification and authentication system.
• Support management, physical and logical access.
• System backup and recovery.
• Manage audit policies.
• Vulnerability and penetration testing.
• Support Distribution.
• Telecommunications Records.
The data security measures mentioned above constitute minimum requirements, so the companies and/or organizations should take additional inevitable measures to provide greater protection of personal data. Companies and/or organizations should take help of personal data protection company or personal data protection service consultants to implement personal data protection services & solutions.
To make sure that your company is covered with regards to privacy & data protection law, organizations like International Institute for cyber security offers tools through enterprise data protection services and personal data protection training course, which will allow you to implement data protection law and keep your business updated at all times according to requirements of the legislation. The enterprise data protection services and personal data protection solutions help customers with:
• During the implementation of privacy & data protection law they do detailed analysis of the company’s processes for management and processing of personal data. They get detailed information about the company, the personal data files, established procedures, flow of information and the degree of compliance with the regulation.
• They coordinate analysis of personal data processing systems along with development of procedures and documentation required according to the standards, as a part of our enterprise data protection services.
• In the personal data protection training they teach the development of data protection policies and best information security practices for general and technical users.
• During our personal data protection audit services they delivery data protection policies document, evaluation of the security measures implemented and data protection law certification. In addition they teach how to do all this during our personal data protection training, so that you can be an enterprise data protection services expert.
The personal data protection course is aimed at managers, legal and IT department professionals and all the people who wish to understand the privacy & data protection law. The personal data protection training is very practical course and covers the following topics:
• Introduction to data protection & privacy law.
• Implementation of environment for data protection & privacy law.
• Types of personal data and rights of access, rectification, cancellation and opposition.
• Data protection agencies and regulations.
• Detailed dataflow analysis.
• Enterprise architecture and audit procedures.
• Implementation of data protection solutions and enterprise data protection services with a methodology defined by our experience and recommended by international standards.
• Incident management procedures for handling personal data breach, sanctions and privacy complaints.
Source:http://www.iicybersecurity.com/enterprise-data_protection-services.html
Microsoft extends olive branch after OneDrive cloud storage storm
One month after cutting OneDrive storage limits for customers and completely axing ‘unlimited’ cloud storage, Microsoft has apologised and is offering to give something back. But users will still need to opt-in, and the bonuses won’t last forever.
Microsoft has back-pedalled on cuts it made to OneDrive cloud storage limits last month, giving back some of the data allowances it was set to take away and apologising for putting the blame on users for excessive use. But customers will still need to opt-in to keep their bonus storage, and the changes will expire after a year.
The company confirmed the changes in a post on its OneDrive user forum, offering users “impacted” by the changes the opportunity to get additional storage for a limited time, and the chance to opt-in to keep free storage bonuses when OneDrive plans are overhauled early next year.

The mea culpa comes a month after Microsoft announced major changes to its cloud storage, halving storage limits for paid plans (whilst keeping the price unchanged), reducing limits on free plans from 15GB to 5GB, ditching its 15GB camera roll storage bonus and completely scrapping ‘unlimited’ storage for all users.
The company is hoping the move will appease customers and curry some favour in an already competitive cloud storage market.
Microsoft is up against rivals such as Dropbox, Google Drive and the Apple-centric iCloud, all hoping to be the one place that users can store all their files to get cloud-based access from anywhere. While each provider offers free storage, these companies generate their revenue through paid plans, and storage limits are king in deciding where customers are willing to hang their hat (and their files).
But Microsoft’s group program manager Douglas Pearce came hat in hand to customers, apologising for recent changes to OneDrive plans and the way they were communicated. In his post on the OneDrive user forum, Pearce said “the announcement came across as blaming customers for using our product” and Microsoft was “genuinely sorry for the frustration this decision has caused.”
That blame referred to Microsoft calling out “a small number of users” on unlimited plans for “extreme backup scenarios,” in some cases, storing up to 75TB of data in the cloud.
While Microsoft initially set about curtailing use, Pearce said paying Office 365 Home, Personal, and University customers would continue to receive 1TB of storage, and users who received additional storage as part of Microsoft’s unlimited offer would keep this limit for at least 12 months.
To make good with disgruntled customers of the free service, anyone with more than 5GB of content stored in the cloud (under the former 15GB free storage limit) will receive a free Office 365 Personal subscription for one year. The offer will come via email early next year and will bring with it 1TB of storage.
Finally, Microsoft is offering an opt-in for its “biggest fans” to keep their 15GB of free storage after storage limits are cut early next year (and to keep their 15GB camera roll bonus, if they currently have that in place). And what constitutes being a fan? Going to the OneDrive website before the end of January 2016 and logging in to get the bonus.
While the changes may go some of the way to pacifying customers upset about the storage cuts, they still only go part of the way to clawing back the cuts made in November. What’s more, customers will need to be existing heavy users to take advantage of the bonuses, or opt in for an increase. There’s also no word on whether or not the changes will last longer than the single year.
Source:http://www.cnet.com/
iOS Jailbreak Backdoor Tweak Compromised 220,000 iCloud Accounts
The recent security breach on iOS platform left 220,000 iCloud user accounts vulnerable due to a backdoor privacy attack caused by the installation of a malicious jailbreak tweak, according to an online Chinese vulnerability-reporting platform WooYun.
Yes, 220,000 is a huge number considering it happened to iOS, one of the most popular mobile operating system that is designed by Apple. But don’t get too frightened because this security flaw has nothing to do with Apple’s security and happened after a jailbreak attempt.

WooYun is a Chinese platform that reports on user submitted security flaws discovered by the researchers in an attempt to provide feedbacks to relevant vendors. So it is, in fact, a reliable website.
According to the post on their website, they have outlined the details about this backdoor attack that breached 220,000 iCloud accounts because of the installation of a malicious jailbreak tweak. In the page, they have also mentioned that the notification about the security flaw has already been issued to the appropriate vendors –apparently Apple.
Below is the (slightly broken) translated version of the report.
What should make the iCloud users worried is that if your account credentials are breached then it is surely going to have a negative impact as the leaked credentials grant an easy access to your personal information stored in the iCloud including all your photos and contacts.
Now you must be wondering that what the reason behind the flaw is. One of a Reddit user, self.jailbreak created a dedicated post about the issue where he outlined that the security breach affected the users in a specific region only and had abounded reach.
“THIS WAS ANNOUNCED BY A CHINA SECURITY WEBSITE WOOYUN (IT MEANS BLACK CLOUD IN CHINESE BASED ON SOUND) EARLIER ON THEIR WEIBO, AND IT IS BASICALLY TELLING THAT THERE ARE SOME SHADY TWEAKS THAT HAVE BACK-DOORS IS STEALING JAILBREAK USER’S ICLOUD ACCOUNT AND PASSWORD TO A REMOTE SERVER, WHICH SO FAR THERE ARE ROUGHLY 220 THOUSAND ACCOUNTS HAS BEEN LEAKED. THEY HAVEN’T ANNOUNCE THAT WHO STOLE IT AND WHAT FOR, BUT AS FAR AS WE KNOW THAT, IF THEY HACK INTO OUR ICLOUD ACCOUNTS, THEY CAN HAVE ACCESS TO OUR MAILS, PHOTOS OR EVEN PRIVATE STUFF.”
So considering how privacy conscious the iOS jailbreak community is and the tweaks and plug-ins released by them is secure, which makes it highly unlikely that a malicious jailbreak tweak would affect such a huge number of users, and that too by the installation of a single tweak or plug-in.
Here is the proof of the leaked iCloud account data, but apart from this picture, there is nothing else has been surfaced on the Internet yet!
One of the related Reddit users posted a valuable comment on the post that says:
“IN ASIAN COUNTRIES, IT IS VERY COMMON FOR PEOPLE TO BUY PHONES, NEW OR USED, FROM TECHNOLOGY MARKETS. AT THOSE MARKETS ARE LOTS OF COMPETING STALLS SELLING PHONES, AND JAILBREAKING YOUR PHONE AND SELLING IT TO YOU PREINSTALLED WITH LOTS OF JAILBROKEN / PIRATED APPS IS PART OF THEIR SERVICE.
THAT IS PART OF WHY JAILBREAKING / PANGU IS SO POPULAR IN ASIA / CHINA. THERE ARE ENTIRE MARKETS OF CHINESE-ONLY PROGRAMS AND APPS THAT WE ARE NOT REALLY EXPOSED TO HERE ON THIS ENGLISH- / WESTERN-DOMINATED SUBREDDIT.
ANYWAY, MY POINT IS THAT IF ONE OF THESE “SHADY” APPS IS SOMETHING THAT WAS SOMEWHAT COMMON FOR THESE 3RD-PARTY SELLERS TO INSTALL, THEN THIS STAT WOULDN’T BE THAT SURPRISING. IT DOESN’T TAKE 220,000 PEOPLE WITH PERSONAL TECH KNOW-HOW TO JAILBREAK AND DOWNLOAD A TWEAK: IT JUST TAKES 220,000 PEOPLE BUYING FROM A FEW HUNDRED / THOUSAND TECHNOLOGY BOUTIQUE SHOPS THAT PRELOAD THE SOFTWARE.”
He did raise a valuable point here that it seems like this attack is caused by the installation of malicious tweaks and plug-ins by the third-party sellers, and then the users used those infected devices resulting in a breach of their accounts.
HOW CAN YOU PROTECT YOUR ICLOUD ACCOUNT?
We all know that jailbreaking your iOS device makes it vulnerable to malicious attacks resulting in an increased risk. To protect yourself from these malicious attacks, it is recommended you to take the following precautionary steps:
Tip #1 – Enable two-factor authentication on your iCloud account.
Tip #2 – Don’t download tweaks from any untrusted or third party repository.
Tip #3 – Stay away from pirated apps or tweaks.
But still, even after following the above-mentioned tips you might be vulnerable to security threats because a jailbroken device is never secure!
Source:https://www.hackread.com
Get Ready for Official IKEA Furniture Hacking Kits
The idea of hacking IKEA products is not new, but it’s still great. It’s such a great idea that the flatpack furniture giant is developing an official IKEA Hack product. This is almost exactly a year after IKEA enlisted lawyers to shut down a down fan-made IKEA hack website, pissing off reasonable customers all over the world.
IKEA clearly doesn’t want a good idea to go to waste. The company recently announced the plan for an official Hack kit during the second annual IKEA Democratic Design Day at its headquarters in Sweden. I was there (on IKEA’s dime) to peer through the company’s utopian vision for the future. By the time two young designer types presented the hack idea and a compelling furniture swapping program, everyone in the room full of jet-lagged journalists and PR teams was at least one drink deep into the evening’s festivities. The buzz made the whole plan sound especially terrific.
Note: So that I could attend this year’s Democractic Design Day, IKEA paid for my transportation, meals, and drinks over the course of four days. The company also gave me a free poster and a free tote bag—both of which I immediately gave away.
The Hack idea is based on an interesting question. “What if you could browse a site and see hacks for all the available products?” one of the young designer types asked the crowed. “Doesn’t that already exist?” I asked my neighbor. (More on that in a second.) But what if IKEA built and curated it? You could even know when you were buying a hackable product in the store.
That’s it. IKEA would build a website that hosted a number of hack ideas for all hackable products. You’d pick a hack kit that worked with your furniture and buy it from IKEA. The prototype shown at the event involved the iconic Frosta stool. Thanks to the Frosta Hack kit, the stool became a chair.
The finished product looked a little bit janky. That’s it to the left:
But again, this is just a program that IKEA is considering. And it would be silly for IKEA to make its hacked furniture look as polished and well designed as the highly designed pieces of furniture it sells at the store. However, IKEA hacking is something that the company knows people like.
IKEA knows that its customers are already modifying furniture they buy at the stores. In some cases, sellers on Etsy and so forth are selling custom-built parts for IKEA furniture. (I know this because I just bought some.) IKEA tried to take a swipe at this burgeoning market last year by shutting down IKEAhackers.net, however the company relented after a massive backlash from fans. Now, it appears that IKEA is taking a more aggressive grab at the market.
The company is also considering taking on Craigslist and the IKEA furniture re-sale market. They’re calling it IKEA Swap. It’s exactly what it sounds like. Once IKEA launches the program, it would offer a “buy back guarantee” on certain items. There would be a little Swap logo on the tag.
Then, when you move or redecorate, you take your old furniture items to an IKEA store and exchange them for points that you can use on—you guessed it—more IKEA furniture. What’s extra cool about this idea, however, is that IKEA is also thinking of creating a second-hand furniture marketplace that would mean people could buy even cheaper IKEA furniture. The designer types called this a “Second Life” market, though I think something got lost in translation there.

The official IKEA Hack and IKEA Swap programs might not happen. Everything IKEA does is highly deliberate and well thought out, so if the numbers don’t make sense, you can be sure that IKEA will continue its inevitably symbiotic relationship with the IKEA hacker community and leave the second-hand market alone. Unsurprisingly, IKEA didn’t mention the unofficial hacking sites or the legal action in its presentation.
In the coming days, I’ll be writing about a number of IKEA products that are supposed to happen in the next couple of years. Some of them are truly exciting—especially the ones that delve into the world of home electronics. Some of them are fascinating—especially the ones that turn trash into furniture. All of them are very IKEA. You’ll see what I mean by that—if you stay tuned.
Source:http://gizmodo.com/
Implementar nube en la empresa o no?
Cambia el modelo de negocio. La computación en nube cambia la forma de servicios de TI se entregan. Ya no entregan desde un lugar en el sitio, los servidores, el almacenamiento y las aplicaciones son proporcionados por proveedores de servicios externos. Las organizaciones necesitan evaluar los riesgos asociados con la pérdida de control de la infraestructura y Seguridad Informatica.
El registro inicial con un servicio de computación en nube es un proceso bastante simple. En muchos casos, el proveedor de servicios, incluso ofrece un periodo de prueba gratuito. Las organizaciones deben considerar sus riesgos de seguridad de la nube debido al registro en el anonimato, la falta de validación, el fraude de servicios, y los servicios ad-hoc como seguridad en redes.
Interfaces de programación de aplicaciones (API) se utilizan para establecer, gestionar y supervisar los servicios. Estas interfaces pueden estar sujetos a las vulnerabilidades de seguridad Informatica que ponen los usuarios en situación de riesgo.
Uno de los beneficios de la computación en la nube es que su organización no tiene por qué conocer los detalles técnicos de cómo se prestan los servicios. Procedimientos del proveedor, el acceso físico a los sistemas, monitoreo de los empleados, y las cuestiones relacionadas con el cumplimiento son transparentes para el cliente. Sin el conocimiento y el control total, su organización puede estar en riesgo y seguridad de la nube debe estar en la nube.
La computación en nube permite que múltiples organizaciones para compartir y almacenar datos en los servidores. Sin embargo, los sistemas operativos y el hardware del servidor originales fueron muy probablemente diseñados para su uso por un solo inquilino.Las organizaciones deben garantizar los controles adecuados están en su lugar para mantener sus datos seguros con seguridad en redes.
Con los recursos de infraestructura compartidos, las organizaciones deberían estar preocupados por los sistemas de autenticación del proveedor de servicios que otorgan acceso a los datos para seguridad Informatica. Las organizaciones también deben preguntar sobre el cifrado, los procedimientos de eliminación de datos, y la continuidad del negocio. Las organizaciones deben ser conscientes de que puede ocurrir el robo de cuentas. Para muchos proveedores de servicios, la atención se centra en la funcionalidad y beneficios, no la seguridad de la nube. Sin
actualizaciones de software adecuadas, prevención de intrusiones y cortafuegos, su organización puede estar en riesgo. Al utilizar los servicios de nube, las actividades de los usuarios, tales como hacer clic en los enlaces en mensajes de correo electrónico, mensajería instantánea, visitando sitios web falsos, etc puede descargar malware en una estación de trabajo local en caso que no hay seguridad en redes. Servicios de computación en la nube de Internet proporcionan tanto beneficios empresariales y técnicos.
4.93 million Gmail accounts hacked.
A Russian hacker has posted the usernames and passwords of 4.93 million Google accounts, leading to a lot of anxiety among users whether or not their accounts are safe.
If you want to check if your Google account, which is the gateway to your Gmail, Plus, Drive, Hangout, YouTube accounts as well, has been compromised, then simply click this link and provide your Gmail ID.
In case you do not want to provide your email ID on this website, you can hide the last three characters of the username, for example abc***@gmail.com instead of abcdef@gmail.com. The website will then display all the Google usernames that start with ‘abc’.
In case your password has been hacked, then immediately change it by answering the security questions that you set while signing up. Also, enable two-step verification for your account in Settings.
Even if your account has not been compromised, it is advisable to enable two-step verification
Hackers attack iCloud users
Cyber-thieves are exploiting the furore around iCloud by launching a phishing campaign that seeks to steal Apple IDs. The BBC reports:
ICloud was at the centre of the stolen celebrity photo scandal last week as many of the images were grabbed by hackers that targeted the service. Apple has responded by beefing up the security that notifies people when their iCloud account is accessed.
Attackers are now sending out bogus notification messages to trick people in to handing over login details. The criminal gang behind the phishing email messages runs the Kelihos/Waledac botnet, said Symantec in a blogpost about the cyber-attack.
A botnet is a large network of compromised computers used for a wide variety of cybercrimes, including sending out spam or mining victims’ machines for saleable data.
Source:http://blouinnews.com/80758/story/hackers-take-aim-icloud-users
Information security training
Information Security age
In many organizations confusion when assigning or distinguish the functions expected of a Computer Security area versus the area of Information Security. Some of them do not even exist as separate areas. Because most have an installed technology infrastructure security, whether tools or perimeter defense or any other device.
What is the difference between them?
We can say that Information Security is the set of procedures, supported by technological tools provide mechanisms “Security” for information residing, stored or transmitted.
But what happens to the “Information” which is not transmitted by such means?
What to do with threats to the business as terrorist attacks, social engineering or defamation affecting a Brand or people in the organization?
As an example, remember the value of the action of Apple Computers was affected when the news that Steve Jobs (founder) was suffering from pancreatic cancer was disclosed. It was true, but it created an immediate devaluation.
To address anything related to “INFORMATION SECURITY” of the company, without necessarily being technological tools should have Information Security awareness. Additionally there are other roles that can not be covered by the Department of IT, because their engineers have the highest privilege level on Infrastructure. They could delete logs, removing evidence, scaled permits, install, uninstall and more.
For this reason the Technology Department needed someone else to “monitor” and check that the mechanisms of protection are met, even by themselves. This is where information security course play an important role to train organizations in the IT security areas.
Likewise, the normal operation of the IT department does not include management and control of information on paper, such as documents, contracts that are in charge of other areas of the company. This vital business information cannot be unprotected just because it is not in digital media. With this complex and comprehensive picture, it is clear that there must be a separate area, detached from IT, to monitor the effective implementation of the necessary controls to safeguard the most important asset of Business: INFORMATION.
Finally, the ISO / IEC 27001 standards in the category of segregation of duties require a separate area monitor and audit all controls Standard Information Security. It is clear that to accomplish this, information security is impaired as it would judge and party. International institute of cyber security is pioneer in providing information security course to individuals and organizations to understand importance to security in information age. Posted by Webimprints.
Seguridad en Windows con FEK
Según expertos de curso de seguridad en redes, con todos los fallos de seguridad de datos que han ocurrido durante los últimos cinco años y también con la llegada de los requisitos de protección de datos, tales como el estándar PCI-DSS, incluso la mayoría de las organizaciones de seguridad resistentes han visto obligados a evaluar y por lo menos hasta cierto grado mucho con los riesgos relacionados con la extrusión de datos y tomar curso seguridad informatica. En consecuencia, los proveedores de productos de seguridad y curso de Hacking en México
así como algunos proveedores de sistemas operativos, Microsoft incluyó, han incorporado controles de prevención de extrusión de datos en sus productos.
Según maestros de curso seguridad informatica, a partir de Windows 2000, Microsoft ha proporcionado el Sistema de cifrado de archivos (EFS) en sus sistemas operativos. EFS, que sólo funciona con el sistema de archivos NTFS-5, cifra los archivos y directorios de una manera que sea transparente para los usuarios.
En EFS tanto el cifrado de clave secreta y pública se utilizan. Codificación secreta se utiliza para cifrar y descifrar los archivos usando un archivo cifrado de clave (FEK). En Windows 2000 y Windows XP el algoritmo extendido de cifrado de datos (DES-X) con una longitud de clave de 128 bits se utiliza para el cifrado de datos. En Vista, Windows Server 2003/8 y Windows 7, el algoritmo de cifrado avanzado mucho más fuerte (AES) con una longitud de clave de 128 bits se utiliza pueden aprender eso todo durante curso de seguridad en redes de iicybersecurity.
Si destruido o dañado, la FEK es recuperable a través de la encriptación de clave pública. Uno de los pares de clave pública se utiliza para cifrar la FEK; el otro se utiliza para descifrar la FEK si la recuperación de claves se hace necesario según curso de Hacking en México.
Microsoft no es el primer proveedor del sistema operativo para ofrecer cifrado de datos, pero la SSC es en muchos aspectos mejor que la competencia, ya que es tan fácil de usar. Aún así, EFS tiene algunas desventajas importantes según curso seguridad informatica, uno de los más notables de las cuales es que si ambos las copias originales y en custodia de las FEKs están en el mismo disco duro y los accidentes del disco duro, los datos cifrados se pierden a menos que las copias de seguridad en otros medios disponibles. Además, no conozco a los usuarios que han activado el cifrado EFS para sus archivos sin ninguna conciencia del administrador local o de dominio acuerdo con expertos de curso de seguridad en redes. Para aprender mas pueden tomar curso de Hacking en México. Publicado por Webimprints.
Los procedimientos de buscar evidencias digitales
seguir las pautas de flujo de trabajo específicos creados para reducir el tiempo, aumentar la cantidad de datos relevantes y producir los resultados más altos de calidad es esencial. Con Informatica forense, puede trabajar con los investigadores y personal de seguridad para identificar y fuentes de pruebas, obtener una comprensión del caso y aplicar los procedimientos de Aprender Hacking en forenses informáticos
Adquirir : El proceso de adquisición se extiende de imágenes de disco forense completa a la recopilación de información de fuentes (como servidores) de una manera consistente con las mejores prácticas de las Directrices de Informatica forense, garantizando así la adecuada cadena de custodia y la admisibilidad.
Extracto : Expertos de iicybersecurity, tienen años de experiencia en recuperación de datos y adquisición. La capacidad de ir más allá de las capacidades de las herramientas de software de Forense Digital y procesos de diseño que producen resultados excepcionales, mientras que mantener la solidez forense es fundamental para hacer casos. Entender dónde buscar en los complejos entornos de redes corporativas y para trabajar la manera más discreta posible, ya que no se interrumpa el flujo de negocios o crear una carga es donde la experiencia pone aparte de otras personas.
Estudiantes de iicybersecurity que toman cursos de Aprender Hacking y forense, sabe dónde mirar, qué preguntar y cómo extraer datos de escritorio y PC portátil de correo electrónico a complicados y los sistemas financieros. Incluso las más pequeñas unidades de disco duro contienen decenas de miles de archivos.
IIcybersecurity, utiliza el estado de las técnicas más avanzadas y herramientas para minimizar la cantidad de datos a la vez dando resultados ejemplares. Nuestros clientes están de acuerdo, los resultados son de la mejor valor relevante y manejados en el menor tiempo posible. Los expertos de Forense Digital, tiene la capacidad de manejar grandes cantidades de datos y girar en torno a resultados rápidos. Una vez que el análisis de Informatica forense se completa presentando un informe comprensible, defendible y completa es la clave. Nuestros clientes encuentran los paquetes de prueba producidas como de Aprender Hacking por expertos de seguridad, completado, fácil de entender y se explican en detalle preciso. La adición de las cartas de relación, explicaciones entidad, líneas de tiempo, historias y análisis de hilo electrónico ofrece a nuestros clientes una clara comprensión del problema y de sus jugadores. Publicado por Webimprints.
Malware de android se llama ‘dendroid’
Expertos de de Seguridad de móviles han alertado a los usuarios de teléfonos inteligentes Android sobre las actividades maliciosas de un virus complicado llamado ‘dendroid’ cuya infección podría “completo compromiso” de su dispositivo de teléfono personal y podría resultar en Hackear Celulares. El virus de la familia mortal ‘Troya’, una vez activado, puede cambiar el servidor de comando y control del teléfono Android personal de un usuario e interceptar mensajes SMS privados.
Expertos de Seguridad de celulares se han informado de que un conjunto de herramientas malicioso llamado dendroid se utiliza para crear aplicaciones con virus que infecta a los teléfonos inteligentes basados en Android.
El malware es creado mediante la modificación de los permisos requeridos por cualquier APK limpia (Android Application Package) con funcionalidad RAT dendroid que permite detallada la gestión de los dispositivos infectados “, dijo el experto en Hackear Celulares .
Los expertos en Seguridad de móviles dicen que el virus es muy listos, ya que tiene un parecido sorprendente con el nombre de Android. La agencia dijo que tras la instalación de esta aplicación maliciosa, un atacante remoto podría “comprometer completamente el teléfono inteligente basado en Android afectada y podría controlar de forma remota”.
El virus se puede realizar una serie de actividades maliciosas. “Se puede cambiar el servidor de comando y control, eliminar los registros de llamadas, abrir páginas web, marcar ningún número, grabar llamadas y audio, intercepción de SMS, subir imágenes y vídeo a la ubicación remota y abrir una aplicación”, dijo el asesor de Seguridad de celulares. Se dijo que el malware infectado “es controlado por el atacante a través dendroidToolkit. Dendroid es una RATA HTTP, que tiene un panel de administración PHP sofisticado y un paquete de ligante APK de la aplicación.”
Los expertos han sugerido algunas medidas de lucha contra para Hackear Celulares, incluyendo mantener un control sobre el uso general y cualquier aumento insatisfactorio en la factura del teléfono móvil del usuario.
“No descargar e instalar aplicaciones de fuentes no confiables, instalar aplicaciones descargadas desde el mercado de aplicaciones de renombre sólo, ejecute un análisis completo del sistema en el dispositivo con una solución de Seguridad de celulares o solución antivirus móvil, verifique los permisos requeridos por una aplicación antes de instalar. Tomar la precaución durante su visita a sitios de confianza / no confiables para hacer clic en enlaces, instalar actualizaciones y parches como Android y cuando esté disponible de los proveedores de dispositivos Android, se recomienda a los usuarios utilizar el cifrado del dispositivo o cifrar función de tarjeta SD externa disponible con la mayor parte del sistema operativo Android,” el dijo el experto de Seguridad de móviles. Publicado por Webimprints.
Apple icloud hacked. Celebrity nude pics leaked
The issue of legal responsibility for cloud storage providers has come to the fore in the last couple of days following a rash of unauthorized nude selfies from a number of celebrities started showing up on website over the Labor Day weekend. Nude and provocative selfies (obviously not designed for public viewing) taken by well-known actresses such as Jennifer Lawrence and Victoria Justice began appearing on various celebrity websites on Friday night, and the social media universe was soon abuzz with discussion over the hack and the responsible parties.
The bad news for Apple Inc. (NASDAQ:AAPL) is that the hackers who stole the nude selfies apparently accessed the accounts through an obvious vulnerability in the Find My iPhone feature: a lack of “brute force” protection. Almost all websites today don’t allow a user to enter wrong passwords thousands of times, and the account locks after 3-5 failed tries in most cases. The Find My iPhone feature somehow did not include this basic protection, so passwords could be picked by “brute force” — trying every possible alphanumeric combination.
Apple reports it has now patched the vulnerability and hackers can no longer gain access to accounts via that method.
Information security training is MUST
Security researchers have discovered a new version of the Stuxnet malware, known as “Havex” which was used in a series of cyber attacks against the above organizations in the energy sector. As you will see in most cases, the affected sector is the energy sector. The famous Stuxnet worm was designed to sabotage the Iranian nuclear plants, now, the new version is scheduled to affect software systems for industrial control SCADA and ICS capabilities disable devices in hydroelectric dams, as well nuclear power plants and even disable power grids using these types of devices.
The so-called Backdoor: W32 / Havex.A and variants of names depending on the antivirus vendor is a remote access Trojan generic and has recently been detected in a series of European companies that develop software applications for SCADA and ICS. Havex is equipped with a new component, whose purpose is to collect information from the network and connected devices by leveraging the OPC (Open Platform Communications) standard. OPC is a communication standard that allows interaction between Windows-based SCADA applications and process control hardware. The malware scans the local network for devices that respond to requests from OPC to collect information about industrial control devices and then sends that information to its command and control server (C & C). Intelligence on development, has prepared the Havex in a function to collect information and send it to a server for developers of this worm, can enhance the Havex more precise functions make efficient and achieve the attack. One of the issues which are companies that own these types of devices is still using SCADA with very tight versions of Windows that do not support or upgrades that may mitigate some of these safety issues and lack of Information Security Training emphasis on staff adds another level of threats. What we recommend is that the production line or that have SCADA network that has the following protections:
1) Where the SCADA LAN not have Internet access,
2) The teams are not accessible from the LAN to the users working in the company network.
3) If you must transfer files, do another VLAN or a segmented network and use services such as FTP or similar.
4) Do not allow the use of SCADA pendrive in those devices that support it. Transferring files to the same should be through a secure channel.
International institute of cyber security enables organizations to fight against the devastating cyber security threats by providing Information Security Course to employees and individuals. Posted by Webimprints.
Diferencia entre bot y back door
En un Curso seguridad informática la discusión de una back door que era primero un punto de entrada secreto escrito por los programadores que crea el código para el programa. A menudo sólo se conoce por el programador y se utiliza para obtener acceso a los programas de depuración y de prueba. Según experto de curso de seguridad en redes el código de back door se reconoce generalmente desencadena ser dirigido por un determinado ID de usuario o por una secuencia probable de los acontecimientos.
En caso de que alguna vez se utilizó para el mantenimiento se ha convertido en la vulnerabilidad a los atacantes explotar. En términos simples unback door a veces conocido como una trampilla es una pieza de software que permite el acceso al sistema de ordenador sin pasar por los procedimientos normales de autenticación acuerdo con temarios de Curso de Hacking en México.
Sobre la base de su funcionamiento y la propagación, hay dos grupos de back door que enseñan durante el Curso seguridad informatica. El primer grupo funciona como un troyano que se inserta manualmente en otra pieza de software, ejecutado a través de su software de host y se extendió por su software de host está instalado. El segundo grupo trabaja más como un gusano en que se ejecutan como parte del proceso de arranque y por lo general se transmiten por los gusanos que llevan ellos como su carga útil.
Un bot es un programa de malware ha controlado de forma remota que se instala en un ordenador sin el conocimiento o consentimiento del propietario del ordenador en secreto que se hagan cargo. Según Curso de Hacking en México, este tipo de programa puede tener un control completo sobre el funcionamiento de ese equipo y sus funciones de Internet, pero por lo general no revela su presencia al propietario del ordenador o usuarios.
En el curso de seguridad en redes muestran que cuando un Bot se instala en un equipo que no sólo va a ser controlado remotamente la computadora, pero se convertirá en un miembro involuntario de una red de bots similares, conocidas como botnets.
También ensenan sobre keylogger en Curso seguridad informatica, lo que son un tipo de software de vigilancia a veces se considera un tipo de spyware que tiene la capacidad de grabar cada tecla que realice en un archivo de registro, por lo general cifrado. Para saber más sobre bot etc pueden tomar Curso de Hacking en México. Experto de iicybersecurity dan curso de seguridad en redes que les ayudaría en entender todo sobre seguridad empresarial. Publicado por Webimprints.
ZESUS y ransomware CryptoLocker
México fue el tercer país más afectado en 2013 por el famoso Zeus malware ataque que se utiliza para robar datos confidenciales de industrias como finanzas, gobierno, manufactura y servicios, según empresa de servicios de Hacking Ético.
Zeus es un malware que se ejecuta en PCs con versiones del sistema operativo Microsoft Windows. Si bien se puede llevar a cabo muchas tareas maliciosos y criminales, a menudo se utiliza para robar información bancaria y pueden detectar con pentesting según maestro de curso seguridad informatica online.
También se utiliza para instalar ransomware CryptoLocker, que bloquea el acceso a la computadora a menos que se pague una tasa a los hackers por el usuario dijo experto de servicios de Hacking Ético.Mientras que uno de los primeros avistamientos generalizadas fue en el otoño de 2013, el virus CryptoLocker está evolucionando y sigue infectando ordenadores en todo el mundo.
La idea detrás de esta actividad delictiva es un archivo ejecutable que encripta el disco duro del ordenador de una manera que requiere una clave de descifrado de obtenerse mediante el pago de una “multa” para los criminales. Los archivos son mantenidos como rehenes por un rescate de US $ 300 a $ 500, que está conectado a un sitio anónimo. La falta de pago de la multa se traducirá en la destrucción de la clave de descifrado. Con los servicios de pentesting pueden detectar eso.
Una de las formas en que el virus está activado es a través de un correo electrónico que aparenta ser enviado por una compañía naviera que indica que su paquete se puede seguir a través de este enlace. Cuando el usuario hace clic en este enlace el virus empieza a infectar el ordenador rápido y eso enseñan durante el curso seguridad informatica online. A veces es capaz de cifrar todo el disco duro, y otras veces es sólo encripta ciertos tipos de archivos.
Las estimaciones especulan que sólo el 3% de los individuos afectados por este virus decide pagar la “multa”. Estas mismas aproximaciones producen una proyección de $ 27 millones en ingresos para estos ladrones a partir de diciembre de 2013 Todos los expertos prevén que la gente debe dejar de pagar a estos criminales ahora dijo empresa de pentesting !Mientras que los servicios fueron los más atacados, los sectores de manufactura, finanzas y gobierno seguidos de cerca en la lista. Un solución contra esa es los servicios de Hacking Ético o también pueden tomar curso seguridad informatica online para aprender más sobre Zesus y CryptoLocker. Publicado por Webimprints.
Como asegurar protección de datos personales en base de datos
Mediante la implementación de forma proactiva para protección de datos, los siguientes estos 10 pasos, una organización puede reducir su exposición al riesgo y asegurarse de que están en la vía rápida al éxito de seguridad de base de datos.
Evaluar el nivel actual de seguridad de la información de base de datos y establecer una línea de base para futuras comparaciones.Este simple esfuerzo pagará grandes dividendos al permitir que una organización de referencia y demostrar el progreso hacia adelante.
Reconocer Vulnerabilidades, Metodologías de Explotación y como asegurar seguridad de base de datos. Las vulnerabilidades se dividen en varias clases – algunos simples y otros complejos. La siguiente lista describe algunos de los ejemplos más comunes de vulnerabilidad:
a. Errores vendedor. Errores de proveedores, incluyendo los errores de programación, tales como desbordamientos de búfer, pueden llevar a los usuarios que tienen la capacidad de ejecutar órdenes impropias y peligrosas en la base de datos. Medida que se descubren estos errores críticos, vendedores lanzan parches para eliminar las vulnerabilidades asociadas para asegurar protección de datos.
b. Arquitectura pobre. Si la seguridad de la información no sea un factor adecuadamente en el diseño de cómo funciona una aplicación, las vulnerabilidades resultantes suelen ser muy difíciles de solucionar. Ejemplos de mala arquitectura incluyen formas débiles de cifrado o clave de almacenamiento inadecuado.
Los intrusos buscan vulnerabilidades conocidas y explotarán siempre que sea posible. Un elemento crucial de garantizar la base de datos es garantizar que los parches se aplican de una manera oportuna y vulnerabilidades conocidas son monitoreados en tiempo real.
c. Errores de configuración. Muchas opciones de configuración de seguridad de base de datos se pueden configurar de manera bien. De hecho, en algunos casos, de forma predeterminada, los parámetros se establecen de forma insegura. En otros casos, estas cuestiones no son problemáticos a menos que cambie la configuración predeterminada. Una vez que una organización ha establecido una línea de base de su postura de seguridad de la información y entiende la gravedad de las vulnerabilidades identificadas, puede comenzar el proceso de priorización de soluciones y mitigar el riesgo. Seguridad de base de datos es un proceso continuo. Los profesionales de seguridad deben monitorear continuamente los sistemas para garantizar protección de datos, mientras que evaluar y responder al entorno cambiante amenaza. Donde gran parte de la seguridad implica valoraciones regulares y validación, el trabajo del día a día puede disminuir rápidamente en tedio y se pasan por alto. A través de la automatización de los procesos de seguridad, profesionales de la seguridad pueden programar tareas y los informes de rutina. Publicado por Webimprints.

















