Month: June 2015
Muy poderoso HanJuan Exploit Kit
Según profesionales de seguridad informática en México, servicios de acortamiento de URL son a menudo empleados por los delincuentes cibernéticos para pasar enlaces maliciosos en México. La organización International Institute of Cyber Security que también proporciona servicios de hacking ético en México señaló que la campaña de publicidad (HanJuan) maliciosa está diseñado para no explotar el enlace corto pero un anuncio embebido dentro del servicio Ad.fly. Por lo tanto, la publicidad maliciosa ocurre y el usuario esta redirigido al kit de exploit.
El ataque comienza con la explotación del servicio Ad.fly. Básicamente, el acortador utiliza la publicidad intersticial. Intersticiales son páginas web que se muestran al usuario antes o después de que lo alcanza el contenido deseado. Por lo general, intersticiales son controladas por un servidor de anuncios.
Campaña maliciosa similares al HanJuan exploit kit también conocida como Troya Timba y Fobber indico experto de seguridad en la nube en México. El servicio de publicidad – Ad.fly ha sido comprometido y explotado para vincular a los usuarios a una pieza de software malicioso diseñado para la conseguir detalles de inicio de sesión. Puede considerar el ataque como ataque de man-in-the-middle ya que el navegador del usuario tiene mucha información de diversas credenciales.
Los investigadores de seguridad informática en México de iicybersecurity dicen que esta publicidad maliciosa se encuentra en algunos sitios web famosos, entre ellos algunos son:
dailymotion.com
theblaze.com
nydailynews.com
tagged.com
webmail.earthlink.net
mail.twc.com
my.juno.com
La amenaza es un ataque de drive-by download que ocurre en cuestión de segundos y no requiere la interacción del usuario, es decir, no se requiere un clic para infectarse. Normalmente, un drive-by download es muy sencillo a menos que se trata de Java o falle el navegador. En el caso de Flash, que es completamente transparente y el usuario no sabría nada de ese ataque.

El sistema de redirección maliciosa de exploit kit es bastante sofisticado, como se indica investigadores de seguridad en la nube. Las primeras sesiones cargan el anuncio intersticial a través de una nota publicitaria de JavaScript codificada: Una vez cargado el kit HanJuan, Flash Player e Internet Explorer son despedidos antes de cargar el payload en el disco duro. La vulnerabilidad explotada en Flash Player es CVE-2015-0359, y el de IE – CVE-2014-1776. Cada uno puede ser empleado, dependiendo del perfil del usuario. Además, la carga útil más probable contiene varias capas de cifrado – tanto en el propio binario y las comunicaciones C & C, por lo que toda la campaña malicioso es muy complejo.
Para estar protegido contra la explotación de los kits, los usuarios pueden seguir algunos consejos de seguridad de Mike Stevens profesional de hacking ético en México, tales como:
- Actualizar frecuentes Java, los productos de Adobe, Silverlight y Flash.
- Apague Java y Flash cuando no se necesita.
- Implementar un programa de aplicación de parches.
- Mantener una solución anti-malware.
Para las organizaciones la punta de seguridad importante es:
- Eliminar o restringir los derechos de nivel de administrador para los empleados no expertos.
Para asegurarse de que el equipo no se ha afectado por el HanJuan EK, realiza un análisis completo de los sistemas, se recomienda experto de iicybersecurity.
Dridex banking malware spreading through new spam campaign
A new spam campaign armed with the Dridexbanking malware is making its rounds and targeting company accountants with phony emails.
Attached to each spam email is a fake scanned document that, in reality, is a macros-enabled .doc, Heimdal Security wrote in its blog post on the attack. The email tries to pass as legitimate under the subject line “Scanned from a Xerox Multifunction Printer.” It tells the recipient that the document was scanned and then sent to them directly from the printer.

If opened, the document retrieves Dridex from various compromised webpages.
While this attack isn’t terribly different from any other spam campaign, Morten Kjaersgaard, CEO of Heimdal Security, told SCMagazine.com in an email that it’s much more “refined and stealthy” in its attack mechanisms.
“As users we need to constantly remind ourselves that hackers are getting better at what they do,” he said. “This is serious business [for them] and we should consider this a serious threat.”
When Heimdal scanned the impacted webpages on VirusTotal, only five out of more than 20 antivirus solutions detected the malicious payload.
Once on a victim’s system, Dridex “sleeps” until a user types in banking credentials that will be sent to the attackers.
Kjaersgaard recommends using a web filtering service on the endpoint, combined with other traditional security approaches, such as signature-based detection.
“I would strongly urge users and companies to be very careful in keeping their software up-to-date and not trusting unlikely inbox items,” he said. “This Dridex campaign is just the tip of a currently very big, and unfortunately increasing, iceberg.”
Source:http://www.scmagazine.com/
Blackhats using mystery Magento card stealers
Sucuri infosec researcher Peter Gramantik says carders are exploiting an unknown vulnerability to steal billing information from e-commerce sites that use eBay’s Magento platform.
Gramantik found an attack script that plunders POST data and identifies valuable payment data before storing it as an encrypted image file.
He says attackers appear to be exploiting a vulnerability in Magento core and demonstrate a strong understanding of the way the platform works.
A quarter of all Alexa top one million e-commerce sites are said to use Magento, making it a valuable target for attackers.
“It seems though that the attacker is exploiting a vulnerability in Magento core or some widely used module/extension,” Gramantik says .
“Using this vector, the attacker is able to inject malicious code into the Magento core file … the attacker gets the content of every POST request.

“The sad part is that you won’t know it’s affecting you until it’s too late, in the worst cases it won’t become apparent until they appear on your bank statements.”
Gramantik says the inclusion of a public key variable indicates the attacker is likely behind a family of credit card stealers.
The attack tool wipes trails clean and masks user agents in an attempt to avoid suspicion. It further modifies the creation timestamp of the image file in which billing information is stored and serves up a fake JPEG header.
“The attacker, however, is able to download the whole image file to decrypt the stolen contents using their public key, and now they have all the billing information processed by the Magento e-commerce website,” Gramantik says.
Variants have been found storing all POST data including login credentials to a gif image.
The security bod previously found a less surreptitious attack where billing information from the Magento billing module is exfiltrated over clear text.
Cisco warns of default SSH key in several products
Cisco security engineers have disclosed that there is a single default ‘maintenance’ SSH key hardcoded into several families of Cisco security appliances.
The default authorised SSH keys and SSH host keys are associated with remote access for maintenance, meaning that a successful attack would allow hackers to access the devices at will. Once obtained, the private keys would allow an attacker to decrypt traffic after collecting it during a man-in-the-middle attack, or impersonate one of the appliances and alter traffic.

According to Cisco, Web Security Virtual Appliances, Email Security Virtual Appliances, and Content Security Management Virtual Appliances are affected by the security issue, reports theSecurityAffairs blog.
“Multiple Cisco products contain a vulnerability that could allow an unauthenticated, remote attacker to decrypt and impersonate secure communication between any virtual content security appliances. Updates are available”, said the company in a widely-quoted statement.
The vendor has pushed out a security patch to rectify the issue, (“cisco-sa-20150625-ironport SSH Keys Vulnerability Fix”), and says all versions prior to 25 June need the update.
The Register quotes the patch advisory as saying: “IP address connectivity to the management interface on the affected platform is the only requirement for the products to be exposed to this vulnerability. No additional configuration is required for this vulnerability to be exploited.
“This patch is not required for physical hardware appliances or for virtual appliance downloads or upgrades after June 25, 2015,” the advisory continues.
However, according to ComputerWorld, Cisco said it “is not aware of any public announcements or malicious use of the vulnerabilities that are described in this advisory.”
New Tinba variant delivered via HanJuan Exploit Kit in malvertising attack
Researchers with Malwarebytes have observed a new variant of Tinba banking malware being distributed via the HanJuan Exploit Kit as part of a malvertising attack that involves advertising and URL shortening service Adf.ly.
Jerome Segura, senior security researcher with Malwarebytes, told SCMagazine.com in a Thursday email correspondence that the majority of infections have been observed in the Netherlands, but he added that the campaign is still in its early stages and could expand.
The threat was made possible because the attackers were able to successfully submit a malicious advertisement to Adf.ly, which was then arbitrarily displayed to users who clicked on shortened Adf.ly links around the web.
“Adf.ly monetizes its service by displaying ads when people click on the shortened link,” Segura said. “Before the shortened link redirects to the actual URL, an ad is displayed for a few seconds. This is where the malvertising happened.”
Once the malvertisement was displayed, a redirection chain triggered without any user interaction, Segura explained. According to a Wednesday post, users were ultimately taken to a compromised Joomla website that pushed what is believed to be the HanJuan Exploit Kit.

Researchers observed the HanJuan Exploit Kit targeting two exploits in order to deliver the Tinba variant – an Adobe Flash Player vulnerability, CVE-2015-0359, and an Internet Explorer vulnerability, CVE-2014-1776, the post said.
The Tinba variant, which was initially identified by Malwarebytes as ‘Fobber,’ was observed going after sensitive information – including Google, Microsoft, Facebook and Twitter credentials – by hooking browsers and grabbing usernames and passwords before they were encrypted, the post said, adding the malware was not observed stealing banking credentials.
“This is an evolved version of Tinba v2, which was identified by security researchers at Fox-IT,” Segura said. “While the core of the program is more or less the same, the authors of this piece of banking malware have improved its encryption capabilities, making it harder for security researchers to properly identify and take down.”
To address these types of threats, Segura said that advertising networks must ensure they are delivering clean content, and end users must make certain their computers are fully patched and are protected with adequate security solutions.
Source:http://www.scmagazine.com/
Security researcher casually drops Adobe Reader, Windows critical vulnerability bomb
A security researcher has casually revealed 15 vulnerabilities which impact on Microsoft Windows and Adobe Reader.
On Tuesday, Google Project Zero hacker Mateusz Jurczyk outlined a total of 15 critical vulnerabilities discovered within font management systems.
The research, also presented at the REcon security conference in Montreal in a talk called “One font vulnerability to rule them all: A story of cross-software ownage, shared codebases and advanced exploitation,” (.PDF), reveals a set of nasty remote code execution and privilege escalation flaws which can be exploited through Adobe Reader or the Windows Kernel.
Jurczyk discovered a number of low to critical-severity security flaws, but the worst two, CVE-2015-3052 and CVE-2015-0093, which exist in both 32-bit and 64-bit systems, are found within the Adobe Type Manager Font Driver.

Speaking to The Register, Jurczyk said the most serious and interesting vulnerability, an “entirely reliable” BLEND instruction exploit, relates to how systems handle CharStrings which are responsible for shaping glyphs depending on point size. The exploit “defeats all modern user and kernel-mode exploit mitigations,” according to the researcher.
“The extremely powerful primitive provided by the vulnerability, together with the fact that it affected all supported versions of both Adobe Reader and Microsoft Windows (32-bit) — thus making it possible to create an exploit chain leading to a full system compromise with just a single bug — makes it one of the most interesting security issues I have discovered so far,” Jurczyk writes.
The researcher also devised a x64 way to exploit the flaw for the purpose of privilege escalation using another CharString vulnerability (CVE-2015-0090).
The video below demonstrates the exploitation of Adobe Reader 11.0.10 using the BLEND vulnerability (CVE-2015-3052), accompanied by sandboxes escapes via the Windows Kernel.
After being notified of the vulnerabilities, Microsoft and Adobe patched the flaws in their latest updates.
Source:http://www.zdnet.com/
THIS RADIO BUG CAN STEAL LAPTOP CRYPTO KEYS, FITS INSIDE A PITA
THE LIST OF paranoia-inducing threats to your computer’s security grows daily: Keyloggers, trojans, infected USB sticks, ransomware…and now the rogue falafel sandwich.
Researchers at Tel Aviv University and Israel’s Technion research institute have developed a new palm-sized device that can wirelessly steal data from a nearby laptop based on the radio waves leaked by its processor’s power use. Their spy bug, built for less than $300, is designed to allow anyone to “listen” to the accidental radio emanations of a computer’s electronics from 19 inches away and derive the user’s secret decryption keys, enabling the attacker to read their encrypted communications. And that device, described in a paper they’re presenting at the Workshop on Cryptographic Hardware and Embedded Systems in September, is both cheaper and more compact than similar attacks from the past—so small, in fact, that the Israeli researchers demonstrated it can fit inside a piece of pita bread.

“The result is that a computer that holds secrets can be readily tapped with such cheap and compact items without the user even knowing he or she is being monitored,” says Eran Tomer, a senior lecturer in computer science at Tel Aviv University. “We showed it’s not just possible, it’s easy to do with components you can find on eBay or even in your kitchen.”
Their key-stealing device, which they call the Portable Instrument for Trace Acquisition (yes, that spells PITA) consists of a loop of wire to act as an antenna, a Rikomagic controller chip, a Funcube software defined radio, and batteries. It can be configured to either collect its cache of stolen data on an SD storage card or to transmit it via Wifi to a remote eavesdropper. The idea to actually cloak the device in a pita—and name it as such—was a last minute addition, Tomer says. The researchers found a piece of the bread in their lab on the night before their deadline and discovered that all their electronics could fit inside it.
The Tel Aviv researchers focused their attack on extracting the keys stored by GnuPG, an open source and widely used version of the encryption software PGP. They alerted GnuPG to their work in February, and an update to the software released at the same time as their paper is designed to protect against the attack. But they say their key-stealing method could be applied to other crypto systems that use RSA and ElGamal, the cryptographic algorithms integrated into GnuPG. Tromer says the group is also exploring whether the technique could be adapted and made more widely applicable, too, even allowing the theft of bitcoins by stealing the private keys created by users’ “wallet” programs. Their paper includes recommendations for how cryptographers can alter software to better foil their radio key thieving mechanism.
The Israeli researchers’ ability to steal data from unwitting computers’ radio waves isn’t exactly new: Computer scientists have known for decades that computers leak sensitive data in the form of radio emissions from their electromagnetic components. The Dutch security researcher Wim van Eckdemonstrated back in 1985 that he could pick up the radio emissions of CRT monitors and reconstruct on-screen images. In 2008, German and Iranian researchers used a similar radio analysis trick to “listen” to the computations inside wireless key fobs and clone them to unlock cars and open garage doors.
But the Tel Aviv researchers’ technique uses that same form of radio spying to target a laptop—a far more electromagnetically complicated target than a key fob or a monitor—and also to do it on the cheap. The team cleverly reduced the resources necessary for their attack by sampling the radio emanations from the processor only intermittently, while the chip does its decryption work of reading those emissions at a much faster frequency. PITA takes its samples at 100 kiloherz compared with the processor’s 20,000-times-faster computation rate of two gigaherz. But by tricking the target into decrypting a carefully chosen message, they were able to “twist the algorithm’s arm” into leaking more sensitive information, creating more clues in the leaked emanations for their PITA radio to pick up.1
“It’s like someone’s reciting secrets in a room, and you only get to hear a syllable a day to try to reconstruct what they’re saying,” says Tromer. “You can force that person in the room to always say one syllable over and over if the secret is ‘zero,’ and another syllable over and over if the secret is ‘one’…That allows us to take a very low frequency sample and still extract information.”
The notion of someone planting an eavesdropping device less than two feet away from a target computer may seem farfetched as an espionage technique—even if that spy device is concealed in a pita (a potentially conspicuous object in certain contexts) or a stealthier disguise like a book or trashcan. But the PITA attack represents a significant advancement from less than a year ago, when the same researchers released an attack that required the attacker to actually touch a laptop’s metal components to pick up their charge.
Tromer says the team is now working on another upgrade that would allow much longer-distance snooping, though he declined to say more before the research’s publication. If that more remote attack becomes practical, it could introduce the threat of radio-based crypto key theft through walls or floors—without even a telltale sandwich to warn the user their secrets are being stolen.
Source:http://www.wired.com/
Ubuntu Patches Privilege-Escalation Bug
There is a privilege-escalation vulnerability in several versions of Ubuntu that results from the fact that the operating system fails to check permissions when users are creating files in some specific circumstances.
Security researcher Philip Pettersson discovered the vulnerability and reported it to Canonical, which maintains Ubuntu. The company has patched the bug, which is present in versions 12.04, 14.04, 14.10, and 15.04. If a local attacker is able to exploit the vulnerability he could get a root shell on a target machine. The vulnerability itself lies in the overlayfs component of Ubuntu, a file system that is designed to be a writeable filesystem in cases where an underlying one is read-only.

“The overlayfs filesystem does not correctly check file permissions when creating new files in the upper filesystem directory. This can be exploited by an unprivileged process in kernels with CONFIG_USER_NS=y and where overlayfs has the FS_USERNS_MOUNT flag, which allows the mounting of overlayfs inside unprivileged mount namespaces. This is the default configuration of Ubuntu 12.04, 14.04, 14.10, and 15.04,” the advisory from Pettersson says.
Pettersson has developed and published a proof-of-concept exploit for the Ubuntu vulnerability that gives the user a root shell. He said an attacker also would have the ability to list the contents of any directory on the machine, regardless of the permissions.
“The ovl_copy_up_* functions do not correctly check that the user has permission to write files to the upperdir directory. The only permissions that are checked is if the owner of the file that is being modified has permission to write to the upperdir. Furthermore, when a file is copied from the lowerdir the file metadata is carbon copied, instead of attributes such as owner being changed to the user that triggered the copy_up_* procedures,” the advisory says.
The patch for this vulnerability, CVE-2015-1328, caused a problem with version 12.04 of Ubuntu.
“The Fix for CVE-2015-1328 introduced a regression into the Linux kernel’s overlayfs file system. The removal of a directory that only exists on the lower layer results in a kernel panic,” a separate Ubuntu advisory says.
Source:https://threatpost.com
Report: Vulnerability Risk Correlates to Exposure on Social Media
The type of coverage a vulnerability receives on social media often correlates to that threat’s level of risk, reveals a recent report.
This is just one of the findings of the 2015 State of Vulnerability Risk Management, a study issued earlier this month by NopSec Labs, a data science and research company that specializes in analyzing malware, exploit, vulnerability and other cyber threat risk patterns.

NopSec Labs published the report, which analyzes some 65,000 vulnerabilities stored in the National Vulnerability Database over the past 20 years, as well as a subset of more than 21,000 of those vulnerabilities identified across customers in all industries in order to evaluate the current state of vulnerability risk management across multiple industries.
Three notable takeways of the report included:
- SaaS providers have the highest number of vulnerabilities per asset.
- Cloud/IT companies have the lowest average remediation time.
- The exposure a vulnerability receives on social media often corresponds to its level of risk and severity rating.
These observations reflect Gemalto’s finding that over a billion records were compromised by data breaches in 2014. NopSec explains that many of these breaches were caused by unmitigated vulnerabilities. Despite advances in detection technologies, these types of risks continue to proliferate due to a host of challenges, including a lack of data and labor-intensive tasks.
It is worth exploring each takeaway in greater detail:
SAAS PROVIDERS HAVE THE HIGHEST NUMBER OF VULNERABILITIES PER ASSET
NopSec’s report reveals that Security-as-a-Service (SaaS) providers have the highest number of vulnerabilities per asset at 18 unique risks. This is followed by six in the financial sector, three in healthcare, and two in education.
When it comes to top vendors, Microsoft outranks all others in vulnerability count across all industries. This is no surprise in the financial sector given its widespread implementation on workstations and servers. Oracle, Sun, Adobe, and Red Hat are also represented in this particular industry.
Regarding the healthcare, education, and cloud/IT industries, open-source technologies, including OpenBSD, Apache, and Red Hat, are among the most vulnerable platforms.
CLOUD/IT COMPANIES HAVE THE LOWEST AVERAGE REMEDIATION TIME
Another finding of the 2015 State of Vulnerability Risk Management report is the significant variability in industry remediation time, here defined as the time that elapses between opening and closing a vulnerability ticket. Cloud providers have the lowest average remediation rate at 50 days, with healthcare companies taking nearly twice as long (an average of 97 days) to remediate its vulnerabilities. Meanwhile, the financial and education sectors have the highest remediation times at both 176 days.
Further analysis reveals even more striking differences. For example, it takes between one and six months to remediate more than a third (36%) of the financial industry’s vulnerabilities, with close to another third (32%) of that same sector’s risks remaining active for more than a year. In the healthcare industry, nearly all (96%) of vulnerabilities are remediated within six months, whereas the education sector takes between one and 12 months to address the sum total of its network risks. Meanwhile, 95% of risks uncovered by the cloud/IT industry receive attention within one month. This is important given NopSec’s finding that cloud and IT companies discover the greatest number of vulnerabilities per asset.
A VULNERABILITY’S EXPOSURE ON SOCIAL MEDIA OFTEN CORRESPONDS TO ITS LEVEL OF RISK AND SEVERITY RATING
Finally, NopSec’s study suggests that there is a correlation between a vulnerability’s security risk and the number of mentions it receives on social media. On average, vulnerabilities used in a targeted malware campaign received 115 tweets. This is significantly higher than the social media coverage witnessed by exploitable (15 tweets) and other (5 tweets) vulnerabilities.
The report also reveals a relationship between social media and a vulnerability’s Common Vulnerability Scoring System (CVSS) score. A direct correlation was not observed, but a clear trend was nonetheless evident, especially with regards to bugs like Heartbleed and Shellshock.
This is in contrast to the direct correlation observed between a vulnerability’s severity rating and its social media exposure. “Critical” vulnerabilities received an average of 748 tweets, which dwarfed the coverage received by vulnerabilities labeled “high” (89 tweets), “medium” (8 tweets), and “low” (3 tweets).
CONCLUSION
As 2015 State of Vulnerability Risk Management illustrates, while the cloud/IT sector is able to quickly remediate the vast majority of its risks, the same cannot be said about the financial, healthcare, and education industries. Companies in these sectors would therefore benefit from investing in technologies that provide data context if and when the appropriate resources become available. These solutions would assist IT teams in prioritizing security risks and in ultimately lowering their organizations’ average remediation time.
Source: http://www.tripwire.com/
Trio of Vulnerabilities Patched in Magneto Web App
A trio of vulnerabilities were recently patched in eBay’s Magento e-commerce web application that could have let attackers carry out a handful of exploits, including phishing, session hijacking, and data interception.
Hadji Samir, a researcher at the firm Vulnerability Lab dug up the problems earlier this year but it wasn’t until this week that they were disclosed, along with proof of concept logs and videos.
Perhaps the most troublesome issue fixed in the platform was a persistent filename vulnerability. A remote attacker could have injected their own script code into the application-side of the affected service module. This could have resulted in session hijacking, persistent phishing, persistent external redirects, along with “persistent manipulation of affected or connected module context,” according to the vulnerability disclosure.

A video that demonstrates the bug shows an attacker logging into Magento, creating a new message, and starting a session tamper to intercept session data. From there they can change the filename to a malicious payload of their choosing.
Samir also found a cross-site scripting (XSS) bug in the platform that could have made it easy for an attacker to remotely inject their own script code into the application-side of the vulnerable online-service module. This could have opened client side accounts up to theft by hijacking, client-side phishing, client-side external redirects and like the other bug, non-persistent manipulation of affected or connected service modules.
The last bug, a cross site request forgery (CSRF) vulnerability, could have allowed “unauthorized client-side application functions without secure validation or session token protection mechanism.” Basically an attacker could have intercepted user sessions and deleted their internal Magento messages without authorization.
Samir found the XSS bug in February and the other two March but Magento’s Developer Team held off until May to patch the issues. They were then publicly disclosed by Vulnerability Lab on Monday, Tuesday, and Wednesday, this week.
Earlier this year developers fixed a remote code execution bug in the platform dug up by Check Point that could have exposed customers’ credit card information, along with other personal data.
Web stores running on Magento, purchased from eBay in 2011, make up about 30 percent of the eCommerce market.
Source:https://threatpost.com
US National Vulnerability Database contained … yup, an XSS vuln
The US National Vulnerability Database was itself left vulnerable to cross-site scripting last week.
The NVD serves as a definitive source of information on CVE security flaws. The XSS vulnerability meant that a skilled hacker could present surfers with content from arbitrary third-party sites as if it came from the NVD itself.
Security consultant Paul Moore, who brought the issue to our attention, told El Reg that the issue presented “minimal risk depending on how payload reaches the site, but could damage reputation/financial wellbeing of firms with fake CVEs”.
Moore put together a proof-of-concept YouTube video, demonstrating the flaw. XSS and SQL Injection regularly top the charts as the most common classes of web development security slip-ups.

In response to a request for comment from El Reg, a representative from NIST (National Institute of Standards and Technology – the organisation that runs the NVD site) said that the problem has been fixed:
The National Vulnerability Database (NVD) had an issue where it did not properly sanitise input received from NVD and partner systems. The issue has since been resolved and the Common Vulnerabilities and Exposures (CVEs) now display correctly.
Microsoft’s site dedicated to fighting US surveillance just got hacked
Microsoft’s website dedicated to fighting the US government on matters of policy and surveillance has been hacked.
The site, which was launched in mid-2013 months after the Edward Snowden revelations were first published, soon became a platform for Microsoft’s corporate views on government surveillance and a new case dedicated to fighting an international search warrant.
But the site appears to have been modified around 9:15pm ET on Wednesday, and remains affected at the time of publication.

It’s not clear who is behind the attack.
At the very top of the site appears to be injected text with keywords, typically used to garner greater search engine hits, including keywords like “casino”, “blackjack”, and “roulette.” Some new pages have beeninjected to show content that embeds content from other casino-related websites. The rest of the site’s content appears to be intact.
The site’s code suggests it is running WordPress 4.0.5, an older version of the popular blogging software released in early May. The latest WordPress version is currently at 4.2.2.
Based on the kind of content injected into the site, it does not appear to be a cyberattack claimed by any particular group or hacker — more likely a scammer who’s able to exploit a weakness in an older version of the site’s software.
Within an hour of the attack, some of the content had been removed, but some buried pages remained.
We reached out to Microsoft but did not immediately hear back. We’ll update the piece once we hear back.
Source:http://www.zdnet.com/
Apple CORED: Boffins reveal password-killer 0days for iOS and OS X
Six university researchers have revealed deadly zero-day flaws in Apple’s iOS and OS X, claiming it is possible to crack Apple’s keychain, break app sandboxes and bypass its App Store security checks so that attackers can steal passwords from any installed app including the native email client without being detected.
The team was able to upload malware to the Apple app store, passing the vetting process without triggering alerts that could raid the keychain to steal passwords for services including iCloud and the Mail app, and all those store within Google Chrome.

Lead researcher Luyi Xing told El Reg he and his team complied with Apple’s request to withhold publication of the research for six months, but had not heard back as of the time of writing.
They say the holes are still present in the Apple platforms meaning their work will likely be consumed by attackers looking to weaponise the work.
Apple was not immediately available for comment.
The Indiana University boffins Xing; Xiaolong Bai; XiaoFeng Wang, and Kai Chen, joined Tongxin Li of Peking University and Xiaojing Liao of Georgia Institute of Technology to develop the research detailed in the paper Unauthorized Cross-App Resource Access on MAC OS X and iOS.
“Recently we discovered a set of surprising security vulnerabilities in Apple’s Mac OS and iOS that allows a malicious app to gain unauthorised access to other apps’ sensitive data such as passwords and tokens for iCloud, Mail app and all web passwords stored by Google Chrome,” Xing told The Register’s security desk.
“Our malicious apps successfully went through Apple’s vetting process and was published on Apple’s Mac app store and iOS app store.
“We completely cracked the keychain service – used to store passwords and other credentials for different Apple apps – and sandbox containers on OS X, and also identified new weaknesses within the inter-app communication mechanisms on OS X and iOS which can be used to steal confidential data from Evernote, Facebook and other high-profile apps.”
The team was able to raid banking credentials from Google Chrome on the latest Mac OS X 10.10.3, using a sandboxed app to steal the system’s keychain and secret iCloud tokens, and passwords from password vaults.
Photos were stolen from WeChat and the token for popular cloud service Evernote nabbed allowing it to be fully compromised.
“The consequences are dire,” the team wrote in the paper.
Some 88.6 percent of 1612 Mac and 200 iOS apps were found “completely exposed” to unauthorised cross-app resource access (XARA) attacks allowing malicious apps to steal otherwise secure data.
Xing says he reported the flaws to Apple in October 2014.
Apple security officers responded in emails seen by El Reg expressing understanding for the gravity of the attacks and asking for a six month extension and in February requesting an advanced copy of the research paper before it was made public.
Google’s Chromium security team was more responsive and removed Keychain integration for Chrome noting that it could likely not be solved at the application level.
AgileBits, owner of popular software 1Password, said it could not find a way to ward off the attacks or make the malware “work harder” some four months after disclosure.
The team’s work into XARA attacks is the first of its kind for Apple’s app isolation mechanisms designed to stop malicious apps from raiding each other. They found “security-critical vulnerabilities” including cross-app resource-sharing mechanisms and communications channels such as keychain, WebSocket and Scheme.
“Note that not only does our attack code circumvent the OS-level protection but it can also get through the restrictive app vetting process of the Apple Stores, completely defeating its multi-layer defense,” the researchers wrote in the paper.
They say almost all XARA flaws arise from Apple’s cross-app resource sharing and communication mechanisms such as keychain for sharing passwords, BID based separation, and URL scheme for app invocation, which is different from how the Android system works.
Their research, previously restricted to Android, would lead to a new line of work for the security community studying how the vulnerabilities affect Apple and other platforms.
Here’s the boffins’ description of their work:
“Our study brings to light a series of unexpected, security-critical aws that can be exploited to circumvent Apple’s isolation protection and its App Store’s security vetting. The consequences of such attacks are devastating, leading to complete disclosure of the most sensitive user information (e.g., passwords) to a malicious app even when it is sandboxed.
Such findings, which we believe are just a tip of the iceberg, will certainly inspire the follow-up research on other XARA hazards across platforms. Most importantly, the new understanding about the fundamental cause of the problem is invaluable to the development of better app isolation protection for future OSes.”
LastPass hacked, password reset system bogged down by heavy traffic
If you use LastPass to store all your passwords, you may want to change your master password. Users’ vaults containing their passwords for myriad accounts across the web are safe, but email addresses, password reminders and the code that could reveal master passwords may have been taken, according to a post from LastPass.
All users logging in from a new device or IP address will be asked verify their accounts via email unless they have multifactor authentication enabled. Those with multifactor authentication are likely safe from any breach into their password vault. LastPass will also require all users to change their password.

While the company asked users to wait to change passwords until asked, it appears the password reset system is currently overwhelmed.
This might not be the first time LastPass has been breached. In 2011, the site noticed an anomaly in data traffic that may have been the result of leaked passwords. Venture Beat also points out a Google security alert page posted to Imgur three weeks ago that may be related to the hack.
This should serve as a reminder that multifactor authentication should always be used. It’s available for most sites, including Facebook, Twitter and many banks and email accounts.
LastPass was also vulnerable because it provided storage for all passwords in the cloud. Some other password vault programs don’t store any password information on their servers, allowing users to sync data through other services and requiring hackers to access both the cloud-storage account and the master password for the vault. We’ve recommended 1Password before, but KeePass also provides a more secure (if less convenient) option.
Source:http://www.geekwire.com/
DD4BC Group Targets Companies with Ransom-Driven DDoS Attacks
According to the 2015 Information Security Breaches Survey, a PwC study that I recently analyzed in an article for The State of Security, the number of denial of service (DoS) attacks has either dropped or remained stagnant for most UK corporations over the past year.
Apparently, this decline has not stopped certain malicious actors from getting creative with their distributed denial of service (DDoS) attacks, however.
Among those groups that have embraced DDoS attack campaigns this past year is Lizard Squad, a hacking group that set up a DDoS stresser serviceearlier in 2015 after successfully overloading the networks of both Playstation Network and Xbox Live on December 25th, 2014. These attacks may have ultimately contributed to Akamai’s finding that the world saw a 90 percent increase in DDoS attacks in 2014’s final quarter as compared to Q3. DDoS attacks are also not exclusive to amateur hacking groups.
Earlier this spring, China targeted GitHub with a large DDoS attack, which caused service interruptions for some users.

Now in the middle of 2015, yet another group has put its own spin on this tried and true method of network disruption. As analyzed by Heimdal Security Software, a group of computer criminals known as ‘DD4BC’ is threatening targets with massive DDoS attacks unless they pay a ransom using Bitcoins. These attacks generally bring down vital business services and cause disruption and financial loss.
Each campaign launched by DD4BC begins with an email that informs the victim of a low-level DDoS attack currently underway against the victim’s website. The email, as revealed by Akamai in a profile of the group, then goes on to demand a ransom paid in Bitcoins in return for DD4BC abstaining from launching a larger DDoS attack against the target.
According to research published by the Swiss Government Computer Emergency Response Team, DD4BC is theoretically capable of launching attacks consuming a bandwidth of up to 500 Gbit/s, which is about 1,000 times the capacity of a DSL/cable line, by taking advantage of amplification attacks that abuse the NTP, SSDP or DNS protocol. In reality, Incapsula, a cloud-based application delivery platform, has noted in a blog post that the group generally launches small application-layer attacks that peak at 150 requests per second.
This does not stop security personnel and law enforcement officials from taking DD4BC seriously, however.
“We are working closely with law enforcement in various jurisdictions to make sure they have a clear picture of what we see and face,” Troels Oerting, group chief information security officer at Barclays and former head of Europol’s European Cybercrime Centre (EC3), told to Computer Weekly. “We take the necessary steps to prevent, detect, react and mitigate all kinds of cyber crime we face, and that is simply the way we work. We take our customers and employees’ privacy and security very.”
The exploits of DD4BC go back at least a year. In November of 2014,reports emerged of the group having sent a note to the Bitalo Bitcoin exchange demanding 1 Bitcoin in return for helping the site enhance its protection against DDoS attacks. At the same time, DD4BC executed a small-scale attack to demonstrate the exchange’s vulnerability to this method of disruption. Bitalo ultimately refused to pay the ransom, however. Instead, the site publically accused the group of blackmail and extortion as well as created a bounty of more than USD $25,000 for information regarding the identities of those behind DD4BC.
Since then, the group has begun demanding Bitcion ransom payments in exchange for refraining from launching large-scale DDoS campaigns. In March of this year, for example, DD4BC targeted Bitmain, one of the largest Bitcoin mining equipment manufacturing companies in the world, and demanded a ransom payment of 10 BTC to prevent an attack. Like Bitalo, Bitmain refused to pay the ransom. In fact, it ultimately added 10 Bitcoins to Bitalo’s existing bounty.
DD4BC is still active as of this writing and is demanding as many as 25 Bitcoins from affected parties in exchange for assurance against a large DDoS attack.
To protect against the attacks launched by DD4BC and other groups, it is recommended that companies invest in anti-DDoS technology and create an emergency computer response team (as well as an organization-wide security policy) that outlines a plan of action if an attack ever arises.
Source:http://www.tripwire.com/
Pop-Under Malvertising Spreads CryptoWall Via Magnitude Exploit Kit
A malvertising campaign discovered by researchers at Malwarebytes leverages pop-under advertisements distributed through Popcash ad network to infect computers with CryptoWall and possibly other types of malware.
Unlike regular pop-ups or ads embedded in web pages, pop-unders are more difficult to notice as they load in a separate browser tab. This particularity, however, is not relevant for infections occurring via the so called drive-by download attacks leveraged by malvertising.

Magnitude EK exploits Flash, delivers CryptoWall via Necurs dropper
According to Jerome Segura from Malwarebytes, the cybercriminals use Magnitude web-based attack tool to deliver exploits for Internet Explorer and Flash Player (CVE-2015-3090) that funnel in a malware downloader.
Segura says that the dropper is Necurs, and it adds a variant of the infamous CryptoWall crypto-malware to the compromised system. The researcher points out that the exploit kit operator is not limited to distributing these pieces of malware and other threats can be sent to vulnerable computers.
Once again, it falls on the shoulders of the user to ensure the safety of the system, by installing the latest updates for Flash Player and Internet Explorer.
It is worth noting that Chrome and Internet Explorer (on Windows 8 and up) receive patches for Adobe’s plugin automatically. New builds of the runtime version of the software need to be updated manually, if the automatic update mechanism is not enabled.
A joint effort is necessary to prevent malvertising incidents
With CryptoWall installed on the computer, users without file backups do not stand a chance of getting their data back without paying the ransom imposed by the crooks. Segura says that the fee is set to $500 / €440, a price not many are able to pay.
“Paying the ransom as a desperate measure to get those important files can be understood but it also keeps this underground economy flourishing,” the researcher warns, echoing the long time recommendation from security experts not to pay.
Combating malvertising requires a collective effort from publishers, ad networks and visitors. Publishers carefully selecting partners, networks making sure that the code served is clean and users keeping their software products up-to-date, is the recipe for protecting against this type of risk.
Source:http://news.softpedia.com/
OpenSSL Patches Five Flaws, Adds Protection Against Logjam Attack
The OpenSSL project has patched several moderate- and low-severity security vulnerabilities and also has added protection against the Logjam attack in new releases of the software.
Most of the vulnerabilities fixed in the new releases are denial-of-service bugs, but one of them can potentially cause memory corruption. That vulnerability only affected older versions of OpenSSL.
“If a DTLS peer receives application data between the ChangeCipherSpec and Finished messages, buffering of such data may cause an invalid free, resulting in a segmentation fault or potentially, memory corruption. This issue affected older OpenSSL versions 1.0.1, 1.0.0 and 0.9.8,” the OpenSSL advisory says.
In addition to the patches, the new versions of OpenSSL also include protection against the Logjam attack, which was disclosed in May. That attack involves the way that servers handle the Diffie-Hellman key exchange.

“Millions of HTTPS, SSH, and VPN servers all use the same prime numbers for Diffie-Hellman key exchange. Practitioners believed this was safe as long as new key exchange messages were generated for every connection. However, the first step in the number field sieve—the most efficient algorithm for breaking a Diffie-Hellman connection—is dependent only on this prime. After this first step, an attacker can quickly break individual connections,” says an explanation of the vulnerability and attack, which was researched by a group of academic and industry experts from Johns Hopkins University, Microsoft, the University of Michigan and elsewhere.
OpenSSL has added protection against the attack in version 1.0.2b and 1.0.1n.
“A vulnerability in the TLS protocol allows a man-in-the-middle attacker to downgrade vulnerable TLS connections using ephemeral Diffie-Hellman key exchange to 512-bit export-grade cryptography. This vulnerability is known as Logjam (CVE-2015-4000). OpenSSL has added protection for TLS clients by rejecting handshakes with DH parameters shorter than 768 bits. This limit will be increased to 1024 bits in a future release,” the advisory says.
The new releases also fix an exploitable issue that could allow an attacker to create malformed certificates and CRLs.
“X509_cmp_time does not properly check the length of the ASN1_TIME string and can read a few bytes out of bounds. In addition, X509_cmp_time accepts an arbitrary number of fractional seconds in the time string. An attacker can use this to craft malformed certificates and CRLs of various sizes and potentially cause a segmentation fault, resulting in a DoS on applications that verify certificates or CRLs. TLS clients that verify CRLs are affected. TLS clients and servers with client authentication enabled may be affected if they use custom verification callbacks,” the advisory says.
Source:https://threatpost.com
Poweliks Trojan goes fileless to evade detection and removal
A recently-discovered Trojan in the wild does not exist as a detectable files on compromised PCs to stay hidden under the radar as it generates ad-click revenue for hackers.
The Poweliks Trojan has been in a constant state of evolution to avoid detection by today’s antivirus systems. First discovered in 2014, the Trojan now uses interesting techniques to infect and stay undetected on victim systems — such as staying fileless.
Explored by Symantec researchers and explained in a blog post Tuesday, the malware, used to generate revenue for cyberattacks through ad-click fraud, is now a registry-based threat which resides only in Windows registries — and with no files to speak of and persistence mechanisms which allow the malware to stay on a PC even after a restart.
Poweliks is considered a “fileless” threat which uses a variety of techniques in order to exist only in a Windows registry. Security researchers from Symantec say Poweliks “stands out from crowd” due to a persistence mechanism which involves the use of a legitimate Windowsrundll32.exe file to execute Javascript code embedded within the registry subkey itself. The code reads additional data from the registry, acting as a payload before execution. Some of this data is encoded, and after execution what is called a “Watchdog process” is installed.
A Watchdog process is used to make sure the malware is still operating. If Poweliks is no longer running and the malware’s registry subkeys have been deleted, the process reinstates the subkeys.
In order to keep Poweliks running, Watchdog changes access rights to prevent access and uses unprintable characters so the keys can be hidden, according to the firm.

In addition, Symantec says the Microsoft Windows Remote Privilege Escalation Vulnerability (CVE-2015-0016) may be exploited by the Trojan in order to wrestle control of a compromised computer. The vulnerability has been patched on up-to-date systems, but those who have not patched their systems are vulnerable.
The security team says:
“Trojan.Bedep also used this zero-day exploit to take control of compromised computers and it did this around the same time that Poweliks was exploiting the vulnerability. This led us to recognize that there could be a connection between Poweliks and Bedep.
Bedep is a downloader and one of the threats it often downloads onto compromised computers is Poweliks.”
Despite the sophisticated techniques Poweliks uses to stay lurking undetected on computer systems, the malware is ultimately still just a click-fraud Trojan used to generate money through fraud. The Trojan requests adverts based on keywords, manipulates searches to make them seem like legitimate user requests, and browses to the URL returned by the ad network by the search. This, in turn, allows the threat actor to earn money based on click rates.
However, these adverts are not shown to victims, so they remain unaware of the infection for longer. The adverts themselves are not such a problem in comparison to the vast amount of adverts Poweliks sends to victims, which can reach up to 3,000 per day according to the security team.
As a result, this high influx of ads can end up clogging up victim machines, hogging memory and can also provide a tunnel for additional malware to be downloaded.
For example, Poweliks can provide a conduit for ransomware to be downloaded, which can end up with a computer being locked, its files encrypted and the victim receiving a demand for money to unlock their PC.
Source:http://www.zdnet.com/
Famous Dark Net Marketplaces to buy Exploits – 0 day Vulnerabilities- Malwares for Research
The best way to access deep web is through a service called Tor (or TOR), also known as ‘The Onion Router’. Installing TOR like installing a new browser as TOR comes with its own browser. The TOR browser itself is built upon Firefox browser’s platform, so if you have ever used Firefox you will find it extremely easy to use TOR browser.
You can use Tor to surf the Internet anonymously. Thus it’s very difficult for private companies and governments to spy on you, if you set up TOR with some precautions like not allowing DNS leakage mentions malware reverse engineer and exploit programming training professor Chris Havens from International institute of cyber security. With Tor you can visit anonymous websites on the Tor network. The anonymous marketplace is one of the largest and most popular sections of the Darknet.
The URL of Dark web websites are different from ordinary URLs. The URLs are composed of random-looking strings of characters followed by. onion. The other networks like Tor are The Freenet Project, which is similar to Tor but also allows the creation of private networks, which only specific people can access.
Another Darknet system is called I2P (the Invisible Internet Project), which is similar to Tor, and it offers secure email, file storage, file sharing, blogging and chat.
Many users who use Tor like network uses an extra layer of protection by connecting using a virtual private network, or VPN and this make very difficult for somebody to track them mentions malware reverse engineer and exploit programming trainer.
Most of the trading is done in TOR network using virtual Crypto currency like Bitcoin, Darkcoin etc. Crypto currency and privacy networks are distributed computing projects, in which network of computers nodes operate the powerful web server.
Crypto currencies monetize people’s involvement with providing darknet services by integrating them in the system. Bitcoins are mathematically generated as the computers in this network execute difficult number-crunching tasks, a procedure known as Bitcoin “mining”. The mathematics of the Bitcoin system were set up so that it becomes progressively more difficult to “mine” Bitcoins over time, and the total number that can ever be mined is limited to around 21m. The entire network is used to monitor and verify both the creation of new Bitcoins through mining, and the transfer of Bitcoins between users. A log is collectively maintained of all transactions, with every new transaction broadcast across the Bitcoin network. Bitcoins can be bought and sold in return for traditional currency on several exchanges, and can also be directly transferred across the internet from one user to another by using appropriate software. This makes Bitcoin a potentially attractive currency in which to settle international transactions, without messing around with bank charges or exchange rates.
There are lot of websites that can be use to buy and sell stuff in deep web, these are normally called marketplaces. We are going to cover some of the marketplace where you can buy and sell exploits, vulnerabilities, 0day stuff, malware, virus etc. While communicating in these market place make you use an escrow system provided by the website or third party to make sure of whatever you buy or sell.
Below are list of some websites/market places for technology related stuff like zero day vulnerabilities, exploits, malwares and hackers etc. In no way we are promoting trade of malware, exploits and vulnerabilities; this information is just for research and educational purposes. Hacking somebody or spreading malware is a criminal offense and these websites should be used to find new vulnerabilities and exploits in the market so that you can secure your networks against them.
The RealDeal Market
A Multisig marketplace originally for private exploits, source code, hardware, hacking services and more. The market is focused on exploits and vulnerabilities. This site is famous for programming related stuff.
http://trdealmgn4uvm42g.onion.city/

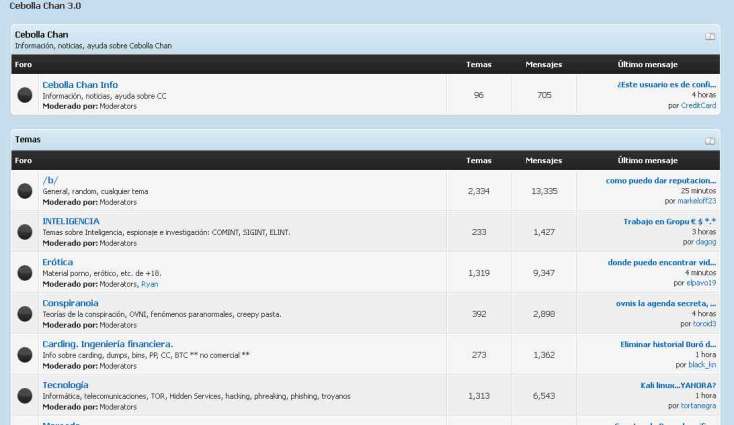
Cebolla Chan
It is a forum based in Spanish. You can find lot of people promoting different types of exploits and hacks. You can contact the seller and trade them through third party escrow system. It is more famous in Mexico, Brazil and Argentina.
http://s6cco2jylmxqcdeh.onion.city/w/index.php
Slamspeech
It is a forum and marketplace for trading hacking related stuff and other things. You can find lot of people promoting different types of exploits and hack. This websites provide its own escrow system. You can use Bitcoins and other virtual currencies to trade here.
https://slamspeechicukxu.onion.city/thread-f77a00df59.html

Crime network
It is a big network of people involved in criminal world and hacking. The majority of people on Crime Network are criminals or group of black hat hackers. Here you can hire hacker or buy vulnerabilities, exploits, malware and hackers etc. This websites provide its own escrow system and also supports third party escrow system.
http://crimenc5wxi63f4r.onion.city/

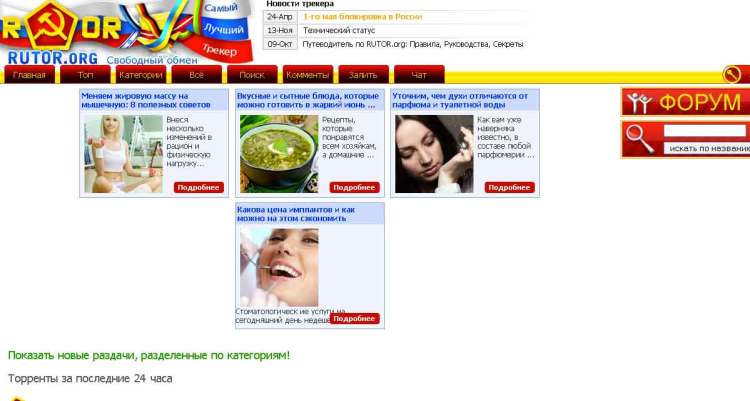
RUTOR.ORG
It is Russian forum and marketplace for trading hacking stuff and other illegal stuff. You can find lot of sellers selling different malwares and new exploits. Also you can find satellite related stuff. The site is based in Russian language. This websites provide its own escrow system. You can use Bitcoins, and other virtual currencies to trade here.
http://rutorc6mqdinc4cz.onion.city/
GitLab
It is an online community where different people can share their programs and codes. In this community you can meet with hacking experts to trade with them or work with them.
http://haklab4ulibiyeix.onion.city/users/sign_in
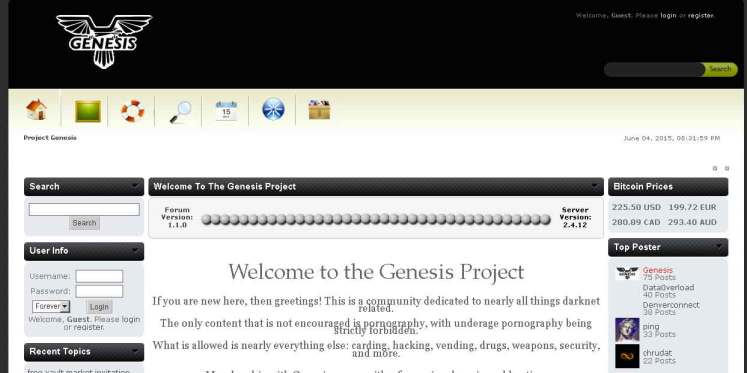
Genesis
It is a forum and marketplace for trading codes, software’s and databases. Lot of people sell databases and exploits. You can use Bitcoins and other virtual currencies to trade here.
http://genesisktrk2q3ud.onion.city/
0Day.in
It is a forum and marketplace and is focused only for trading 0day vulnerabilities, exploits, malwares, source codes, software’s and databases. Lots of hacking experts sell databases and exploits here. You can use Bitcoins and other virtual currencies to trade here.
http://qzbkwswfv5k2oj5d.onion/

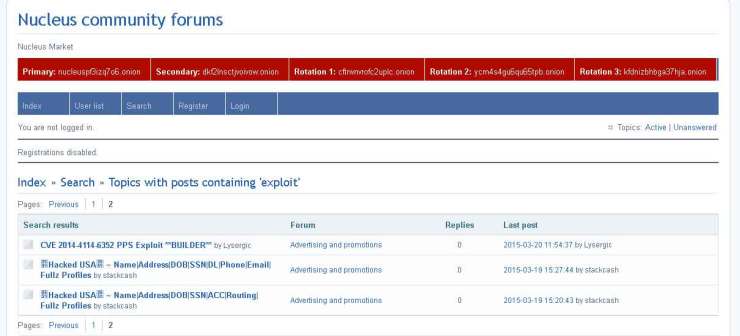
Nucleus Community forums
It is an online community where different people can share their programs and codes. In this community you can meet with hacking experts to trade with them or work with them. You can meet hackers and buy exploits from them.
http://z34uj4opd3tejafn.onion/
scan4You.net
It is forum and marketplace for trading technology related stuff like software’s. You can use Bitcoins and other virtual currencies to trade here.
http://hybedxst6ulae4oh.onion.city/
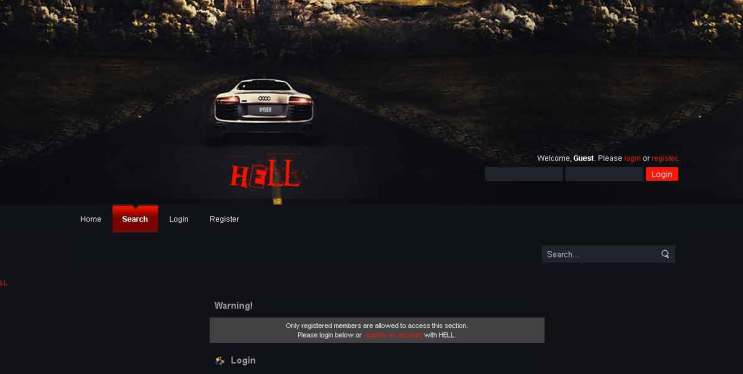
Hell
It is forum and marketplace for trading technology related stuff like hacking software’s. You can use Bitcoins and other virtual currencies to trade here. You can use escrow system for trading here.
http://hell2bjhfxm77htq.onion.city/
As per malware reverse engineer and exploit programming training professor Chris Havens above are some of the marketplaces for beginners. For advance users you will have to go into more deep layers of Deep web and know the industry experts and dealers. However to be anonymous you can use bitcoin mixing services like
Shared Coin: https://sharedcoin.com/
Coinmixer.io: https://bitmixer.io/
This provides privacy for your transactions by combining your transaction with other people’s. Also you can use open Source Multisig solution while trading and use PGP verification services like mentioned below.
Vendor PGP key Search: http://lbnugoq5na3mzkgv.onion
Vawtrak Banking Malware Hides Its Servers in Tor
Some variants of Vawtrak banking Trojan, also known as Neverquest, have been found to hide their command and control (C&C) servers in Tor anonymity network, making the cybercriminal operation more difficult to disrupt.
Most versions of the malware rely on hard-coded IP addresses for the C&C, but this approach makes the domains used to deliver commands to the infected machine easy to discover via threat analysis techniques.
DGA is not foolproof
A different mechanism for making Vawtrak more resilient to takedown efforts involves a domain generation algorithm, which creates a set of domain names the malware contacts to receive commands.
Cybercriminals register only a small number of them because Vawtrak will check each of them until the appropriate response is received.
Raul Alvarez from Fortinet explains how the process works for this piece of malware, saying that Vawtrak’s code includes multiple DWORD values matching different domain names.

“Each DWORD value is a seed used to generate the domain name. These seeds are stored as fixed values within the malware code, thereby producing the same pseudo-randomized domain names. To generate the corresponding domain name, Vawtrak uses the seed to generate the pseudo-randomized characters of the domain name,” he says in a blog post.
However, this technique is not infallible because researchers can break the algorithm and find the strings generated.
Tor2Web proxy used to access hidden services
More recent variants of the threat rely on Tor2Web, a proxy that establishes a direct connection to a server in Tor network without the need for additional tools.
The strings generated by the DGA are for locations in Tor, and the author implemented a function that passes them through the Tor2Web proxy service.
Although a user connecting to the proxy service can be traced, the connection beyond it is not. Traffic in Tor is encrypted and routed through multiple machines that do not keep records of the origin and destination. The result is access to a server whose location is shrouded in anonymity.
Vawtrak includes multiple protection mechanisms (such as disabling antivirus solutions) that allow it to evade detection and analysis. After compromising a machine, it can pilfer credentials and record user activity (keystrokes, screenshots and video).
Its operator can access the system remotely through a VNC channel and alter web sessions by injecting fake content in order to collect passwords for online banking accounts and the additional codes needed to access them.
Source:http://news.softpedia.com/



