Month: January 2019
VULNERABILIDAD EN FACETIME PERMITE ESPIAR A USUARIOS DE APPLE

Se recomienda a los usuarios de Apple desactivar esta aplicación, al menos hasta que sea actualizada
Especialistas en seguridad en redes del Instituto Internacional de Seguridad Cibernética reportan el hallazgo de una vulnerabilidad sin parchear en FaceTime, la aplicación de Apple para realizar llamadas de audio y video. Según los reportes, este error permitiría que el receptor de una llamada sea visto o escuchado desde antes de contestar la llamada.
Este incidente se ha vuelto viral en Twitter y otras redes sociales, donde los usuarios han mostrado su malestar con esta falla de seguridad, pues cualquier dispositivo Apple podría convertirse en una máquina de espionaje sin que la víctima pueda darse cuenta.
Especialistas en seguridad en redes probaron un iPhone X (con iOS 12.1.2) para verificar la presencia de la vulnerabilidad, logrando comprobar que el error existe. La prueba también tuvo éxito en una MacBook con MacOS Mojave.
Esta falla, que algunos consideran más una falla de diseño que una vulnerabilidad, reside en la función Group FaceTime, lanzada recientemente por Apple. El proceso para reproducir el error es el siguiente:
- Inicie una videollamada de FaceTime con cualquier contacto
- Mientras se marca al contacto, deslice hacia arriba desde la parte inferior de la pantalla de su iPhone y seleccione “Agregar persona”
- En “Agregar persona”, agregue su propio número
- Esto iniciará una llamada grupal de FaceTime entre usted y la persona a la que llamó, con lo que podrá escuchar al receptor de la llamada, incluso si la persona aún no acepta la llamada
Los especialistas en seguridad en redes también mencionaron que si la persona que recibe la llamada presiona el botón de volumen o encendido (para silenciar o rechazar la llamada) la cámara del iPhone podría encenderse.
La empresa afirmó que tiene conocimiento del incidente y que ya se está trabajando en la corrección de este bug. Mientras llega la actualización de FaceTime, Apple decidió deshabilitar la función de llamada grupal, se espera que la falla sea corregida en el transcurso de esta semana.
Hasta que esto suceda, se recomienda a los usuarios deshabilitar la aplicación de FaceTime en sus dispositivos Apple.
- Deshabilitar en iPhone o iPad: Vaya a Configuración, desplácese hacia abajo para encontrar el ícono de ‘FaceTime’ y elija “Desactivar la función”
- Deshabilitar en Mac: Abra FaceTime en su Mac y haga clic en la esquina superior izquierda de la barra de menú y luego haga clic en “Desactivar FaceTime”
GERENTES DE SISTEMAS Y CEO SON DESPEDIDOS Y DEMANDADOS DESPUÉS DE ROBO MASIVO DE DATOS DE SALUD

Dos directivos fueron despedidos y un gerente general fue multado por el robo masivo de datos del sistema de salud de Singapur
Los Sistemas Integrados de Información de la Salud de Singapur (IHIS) despidieron a dos gerentes, además de multar a cinco empleados de alto nivel, entre ellos Bruce Liang, CEO de la compañía, por su responsabilidad en el robo masivo de datos del sistema SingHeatlh el año pasado, reportan especialistas en seguridad en redes del Instituto Internacional de Seguridad Cibernética.
Se calcula que el incidente afectó a cerca de un millón 500 mil personas, casi la tercera parte de la población total en Singapur. Acorde a especialistas en seguridad en redes, los atacantes accedieron a detalles personales como:
- Nombre de los pacientes
- Fechas de nacimiento
- Números de identificación personal NRIC (National Registration Identity Card)
- Detalles étnicos y raciales
Además, detalles referentes a la salud de más de 150 mil pacientes (como diagnósticos o tratamientos) también fueron robados; entre las personas afectadas por este incidente se encuentra Lee Hsien Loong, Primer Ministro de Singapur.
Los Ministerios de Salud y Comunicaciones de Singapur definieron este incidente como “una campaña de ciberataque deliberada, bien definida y planificada”, aunque posteriores investigaciones de expertos en seguridad en redes confirmaron que un error humano fue fundamental para que este incidente se concretara: “si bien SingHealth implementa los controles técnicos necesarios, dos empleados de alto nivel resultaron ser “negligentes en sus labores”.
Los investigadores criticaron la pobre configuración de servidor de Lum Yuan Woh, líder del equipo de Citriz, pues consideraron que “se introdujeron riesgos innecesarios para el sistema”. Por otra parte, Ernest Tan, gernete del equipo de Respuesta a Incidentes de SingHealth, fue criticado por “ignorar el debido proceso de notificación de incidentes”.
Otros cinco empleados superiores también fueron señalados como responsables por el robo de datos, pero sus errores no fueron considerados lo suficientemente serios como para ameritar el despido. Cuatro de estos empleados fueron multados, mientras el empleado restante fue transferido a un puesto con menores responsabilidades.
Acorde a los expertos, los empleados de SingHealth cometieron tres errores fundamentales:
- No fueron capaces de instalar los parches de software en sus sistemas, lo que permitió a los atacantes explotar una vulnerabilidad de Office y obtener acceso a la PC de uno de los empleados
- Al equipo de SingHealth le tomó al menos un año identificar la violación de datos. Los hackers accedieron al sistema por primera vez en agosto de 2017 y, a lo largo de un año, lograron distribuir malware e infectar otros equipos de la red sin ser detectados
- Los empleados utilizaban contraseñas débiles (p@ssw0rd, por ejemplo). Este es uno de los errores más graves que puede cometer un encargado de sistemas, pues la simple configuración de una contraseña fuerte puede prevenir múltiples ataques
Desafortunadamente estos problemas no son exclusivos del equipo de SingHealth; los errores humanos son una de las principales causas de robo de datos, y todas las organizaciones deben adoptar las políticas pertinentes para mitigar los riesgos derivados de estas fallas.
ACUSAN A HUAWEI DE ESPIONAJE TECNOLÓGICO E INCUMPLIMIENTO DE SANCIONES

Autoridades estadounidenses acusan a la empresa china de robo de tecnología
El Departamento de Justicia de los Estados Unidos (DOJ) acusa al gigante chino de telecomunicaciones Huawei en dos casos, incluido el que condujo al arresto de un alto ejecutivo de la empresa en Canadá, informan especialistas en seguridad en redes del Instituto Internacional de Seguridad Cibernética.
El DOJ mencionó que estos cargos son la respuesta del gobierno de Estados Unidos a la campaña persistente que la empresa ha desplegado para explotar organizaciones americanas.
Acorde a especialistas en seguridad en redes, el DOJ confirmó que se han presentado 13 cargos contra Meng Wanzhou, directora financiera de Huawei, además de otros tres colaboradores; los empleados de la empresa han sido acusados de violar las sanciones impuestas por el gobierno de E.U. a Irán.
Wanzhou es hija de Ren Zhengfei, fundador de Huawei, quien se encuentra en libertad bajo fianza en Canadá, a la espera de un posible proceso de extradición a E.U. Estas medidas han generado un alto nivel de tensión en las relaciones entre Estados Unidos, Canadá y China.
Además, se presentaron otros 10 cargos por espionaje tecnológico contra dos empresas subsidiarias de Huawei, mencionaron los especialistas en seguridad en redes.
Christopher Wray, director del Buró Federal de Investigaciones (FBI), declaró que “los cargos presentados contra estas empresas exponen las acciones arbitrarias y persistentes de Huawei en contra de empresas e instituciones financieras americanas, lo que atenta contra la competencia libre”. Por otra parte, Matthew Whitaker, fiscal general de E.U., mencionó que el proceso de extradición contra Ren Zhengfei comenzará a finales de este mes.
Según Whitaker, la acusación no está tratando de vincular al gobierno chino con las acciones maliciosas de Huawei, pero E.U. considera que China debe hacer que sus organizaciones cumplan con las leyes. “Como les dije a los funcionarios chinos en agosto pasado, China debe asegurarse de que sus ciudadanos y organizaciones cumplan la ley”, dijo Whitaker.
FALLAS EN EL SERVICIO MICROSOFT 365 PROVOCAN INTERRUPCIÓN EN OUTLOOK Y EXCHANGE

Usuarios tuvieron problemas para acceder a sus buzones por casi dos días
El paquete de trabajo en línea Microsoft 365 experimentó problemas de interrupción de servicio en días recientes. Múltiples usuarios reportaron que no podían acceder a sus buzones a través de ninguna plataforma, informan especialistas en seguridad en redes del Instituto Internacional de Seguridad Cibernética.
Algunos usuarios también reportaron retrasos de hasta tres horas en el envío y recepción de sus emails, además de algunas otras fallas en el servicio (los usuarios recibieron múltiples veces el mismo correo).
Microsoft 365 es un servicio en línea que incluye Office 365, Windows 10 y Windows Enterprise Mobility and Security. Acorde a expertos en seguridad en redes, tratándose de una plataforma en línea, los inconvenientes que se presentan pueden ser serios. En este caso, todos los usuarios de Microsoft 365 fueron afectados por el mismo error de este producto en la nube.
A través de Twitter, el equipo de Microsoft 365 mencionó: “Hemos determinado que un subconjunto de la infraestructura del controlador de dominio no responde. Estamos aplicando algunas medidas para mitigar los inconvenientes. Se pueden encontrar más detalles en el centro de administración de Microsoft 365”.
Mientras Microsoft concluía su investigación sobre el incidente, usuarios alrededor del mundo continuaban reportando fallas en el servicio que impedían enviar y recibir sus mensajes personales y empresariales a lo largo de casi dos días.
Microsoft informó posteriormente que “una fila de espera mayor a la esperada en la infraestructura de autenticación de la plataforma podría ser la causa del incidente. Ahora estamos trabajando para identificar las causas de estas filas, así como en la mitigación del impacto”.
Algunas horas después, Microsoft informó vía Twitter: “Nuestros datos de telemetría indican fallas en el tiempo de espera de conexión dentro de la infraestructura de autenticación de Exchange, lo que generó este incidente”.
Después de dos días de inactividad, usuarios de Microsoft 365 comenzaron a reportar que el incidente (identificado como EX172491) había sido eliminado por completo, acorde a especialistas en seguridad en redes.
FACETIME VULNERABILITY ALLOWS SPYING ON APPLE USERS

It is recommended that Apple users disable this app, at least until it is updated
Network security and ethical hacking specialists from the International Institute of Cyber Security reported the discovery of an unpatched vulnerability in FaceTime, the Apple application for making audio and video calls. According to reports, this bug would allow the receiver of a call to be viewed or heard before answering the call.
This incident has become viral on Twitter and other social network platforms, where users have shown their discomfort with this security flaw, as any Apple device could become a spy machine without the victim being able to realize it.
Network security specialists tested an iPhone X (with iOS 12.1.2) to verify the presence of the vulnerability, making sure that the error exists. The test was also successful on a MacBook with the Mojave MacOS.
This flaw, which some experts consider more a design flaw than vulnerability, resides in the FaceTime group call feature, recently launched by Apple. The process to reproduce the error is as follows:
- Start a FaceTime video call with any contact
- While dialing the contact, slide up from the bottom of your iPhone screen and select “Add Person”
- In “Add Person”, add your own number
- This will initiate a FaceTime group call between you and the person you called, so you can listen to the caller’s receiver, even if the person still does not accept the call
Network security specialists also mentioned that if the person receiving the call presses the volume or the on/off button (to mute or reject the call) the iPhone camera could turn on.
The company said that it has knowledge of the incident and that it is already working on the correction of this bug. As the FaceTime update arrives, Apple decided to temporarily disable the group call feature, the flaw is expected to be corrected over the course of this week.
- Disable on iPhone or iPad: Go to Settings, scroll down to find the ‘FaceTime’ icon and choose ‘Disable function’
- Disable on Mac: Open FaceTime on your Mac and click on the upper left corner of the menu bar and then click “Disable FaceTime”
SYSTEMS MANAGERS AND CEO ARE DISMISSED AND SUED AFTER MASSIVE HEALTH DATA BREACH

Two officials were dismissed and a general manager was fined for massive data theft on the health system in Singapore
The Integrated Health Information Systems of Singapore (IHIS) fired two managers, in addition to fine five high-level employees, including Bruce Liang, CEO of the company, for their responsibility in the SingHealth system massive data breach the last year, as reported by network security specialists from the International Institute of Cyber Security.
It is estimated that the incident affected about 1.5 million people, nearly one-third of the total population in Singapore. According to specialists in network security, the attackers accessed to personal details such as:
- Patients’ full names
- Dates of birth
- NRIC (National Registration Identity Card) personal identification numbers
- Ethnic and racial details
In addition, details concerning the health of over 150k patients (such as diagnoses or treatments) were also stolen; the people affected by this incident include Lee Hsien Loong, Prime Minister of Singapore.
The Singapore Ministries of Health and Communications defined this incident as “a deliberate, well-defined and planned cyberattack campaign”, although subsequent investigations by network security experts confirmed that a human error was fundamental for this incident to materialize: “while SingHealth implements the necessary technical controls, two high-level employees turned out to be negligent in their work”.
The researchers criticized the poor server configuration of Lum Yuan Woh, the leader of the Citrix team, as they considered that “unnecessary risks were introduced to the system”. On the other hand, Ernest Tan, SingHealth Incident Response Team Manager, was criticized for “ignoring the due process of security incident notification”.
Another five senior employees were also reported as responsible for data theft, but their mistakes were not considered serious enough to warrant dismissal. Four of these employees were fined, while the remaining employee was transferred to a position with lower responsibilities.
According to the experts, SingHealth employees committed three fundamental errors:
- They were unable to install software patches on their systems, allowing attackers to exploit an Office vulnerability and gain access to one of the employees’ PC
- The SingHealth team took at least a year to identify the data breach. Hackers accessed the system for the first time in August 2017 and, over a year, managed to distribute malware and infect other computers on the network without being detected
- Employees used weak passwords (p@ssw0rd, for example). This is one of the most serious errors that a sysadmin can commit, because the simple configuration of a strong password can prevent multiple attacks
Unfortunately these problems are not unique to the SingHealth team; human errors are one of the main causes of data breaches, and all organizations must adopt the relevant policies to mitigate the risks arising from these flaws.
HUAWEI ACCUSED OF TECHNOLOGICAL ESPIONAGE AND SANCTIONS VIOLATION

American authorities accuse Chinese company of technology theft
The United States Department of Justice (DOJ) accuses the Chinese telecommunications giant Huawei in two cases, including the one that led to the arrest of a senior executive of the company in Canada, as report by network security and ethical hacking specialists from the International Institute of Cyber Security.
The DOJ mentioned that these charges are the U.S. government’s response to the persistent campaign that the company has deployed to exploit American organizations.
According to network security specialists, the DOJ confirmed that 13 charges were filed against Meng Wanzhou, chief financial officer of Huawei, as well as three other collaborators; the company employees have been accused of violating the sanctions imposed by the U.S. government on Iran.
Wanzhou is the daughter of Ren Zhengfei, founder of Huawei, who is on bail in Canada, pending a possible process of extradition to the U.S. These measures have generated a high level of tension in relations between the United States, Canada and China.
In addition, another 10 charges for technological espionage were filed against two Huawei subsidiary companies, the network security specialists mentioned.
Christopher Wray, director of the Federal Bureau of Investigation (FBI), stated that “the charges against these companies expose Huawei arbitrary and persistent actions against American companies and financial institutions, which is attentive against free competition”. On the other hand, Matthew Whitaker, U.S. Attorney General, mentioned that the extradition process against Ren Zhengfei will begin later this month.
According to Whitaker, the prosecution is not trying to link the Chinese government with Huawei’s malicious actions, but the U.S. believes China must make its organizations comply with the laws. “As I told Chinese officials last August, China must ensure that its citizens and organizations comply with their law”, said Whitaker.
MICROSOFT 365 SERVICE ERROR CAUSES OUTLOOK AND EXCHANGE DISRUPTION

Users had trouble accessing their mailboxes for almost two days
The Microsoft 365 online work suite experienced service outage issues in recent days. Multiple users reported that they were not able to access their mailboxes through any platform, reported network security and ethical hacking experts from the International Institute of Cyber Security.
Some users also reported delays of up to three hours in the sending and receiving of their emails; in addition to some other failures in the service (users received multiple times the same message).
Microsoft 365 is an online service that includes Office 365, Windows 10, and Windows Enterprise Mobility and Security. According to experts in network security, in the case of an online platform, the drawbacks that are presented can be serious. In this case, all users of Microsoft 365 were affected by the same error of this product in the cloud.
Through Twitter, the Microsoft 365 team mentioned: “We have determined that a subset of the domain controller infrastructure is not responding. We are implementing some measures to mitigate the drawbacks. More details can be found in the Microsoft 365 Administration Center”.
As Microsoft concluded its investigation into the incident, users around the world continued to report service failures that prevented them from sending and receiving their personal and business messages for almost two days.
Microsoft later reported that “a higher-than-expected queuing in the platform’s authentication infrastructure could be the cause of the incident. We are now working to identify the causes of these queuing as well as impact mitigation”.
A few hours later, Microsoft reported via Twitter: “Our telemetry data indicate flaws in the connection timeout within the Exchange authentication infrastructure, which generated this incident”.
After two days of inactivity, Microsoft 365 users began reporting that the incident (identified as EX172491) had been completely eliminated, according to network security experts.
JOK3R – UNA HERRAMIENTA DE HACKING MULTIFUNCIONAL
En la mayoría de los casos, las pruebas de penetración se realizan manualmente, es aquí donde el pentester utiliza todas las herramientas disponibles en Internet para encontrar errores o vulnerabilidades en las aplicaciones web. Hoy en día, el pentesting se realiza en herramientas automatizadas. Estas herramientas están recibiendo tanta atención, pues ahorran mucho tiempo, los pentesters puede hacer otras tareas desafiantes en su labor de hacking. Hoy estamos hablando de la herramienta JOK3R.
Expertos en seguridad en redes del Instituto Internacional de Seguridad Cibernética afirman que JOK3R es muy útil en la fase inicial de pruebas de penetración.
JOK3R es un marco de pentesting muy popular que se construye utilizando muchas herramientas populares. El objetivo principal de esta herramienta es ahorrar tiempo en el análisis del sistema objetivo. Entonces el pentester puede disfrutar la mayor parte del tiempo en otras labores de hacking. Esta herramienta ha sido probada en Kali Linux 2017.3.
INSTALACIÓN DE DVWA PARA EL OBJETIVO
- En el lado del atacante estamos utilizando DVWA para probar la herramienta. Para descargar DVWA iso vaya a: https://www.vulnhub.com/entry/damn-vulnerable-web-application-dvwa-107,43/
- Después de descargar iso, abra iso en virtual box o vmware workstation. Entonces empieza iso
- Para obtener DVWA ip escriba ifconfig
INSTALACIÓN DE JOK3R PARA EL ATACANTE
- Para la clonación, escriba git clone https://github.com/koutto/jok3r.git
- Luego escriba cd jok3r
- Escriba pip install -r requirements.txt
- El permiso install-all.sh y install-dependencies.sh necesita ser cambiado. Para eso, teclee chmod u + x install-dependencies.sh y luego escriba chmod u + x install-all.sh
- Para verificar si el permiso ha cambiado, escriba ls -ltr
root@kali:/home/iicybersecurity/Downloads/jok3r# ls -ltr total 176 -rw-r--r-- 1 root root 35149 Jan 24 00:02 LICENSE -rw-r--r-- 1 root root 348 Jan 24 00:02 Dockerfile -rw-r--r-- 1 root root 461 Jan 24 00:02 CHANGELOG.rst -rw-r--r-- 1 root root 2519 Jan 24 00:02 TODO.rst -rw-r--r-- 1 root root 41498 Jan 24 00:02 README.rst -rw-r--r-- 1 root root 1934 Jan 24 00:02 jok3r.py -rwxr-xr-x 1 root root 3126 Jan 24 00:02 install-dependencies.sh -rwxr-xr-x 1 root root 129 Jan 24 00:02 install-all.sh drwxr-xr-x 2 root root 4096 Jan 24 00:02 docker drwxr-xr-x 3 root root 4096 Jan 24 00:02 doc -rw-r--r-- 1 root root 249 Jan 24 00:02 requirements.txt drwxr-xr-x 2 root root 4096 Jan 24 00:02 pictures drwxr-xr-x 3 root root 4096 Jan 24 00:02 webshells drwxr-xr-x 5 root root 4096 Jan 24 00:02 wordlists drwxr-xr-x 10 root root 4096 Jan 24 00:24 lib drwxr-xr-x 2 root root 4096 Jan 24 00:25 settings -rw-r--r-- 1 root root 32768 Jan 24 00:25 local.db drwxr-xr-x 5 root root 4096 Jan 24 00:25 toolbox
- Ahora escriba ./install-all.sh
- Escriba ./install-dependencies.sh
- Esta herramienta puede tardar en instalar dependencias, ya que algunos de los archivos tardan en ser descargados
- Si install-all.sh y install-dependencies.sh no funcionan correctamente o muestran un error al instalar las dependencias, considere el uso de la ventana acoplable para instalar todas las dependencias
- Durante la instalación se muestra la actualización de pip para eso, teclee sudo apt-get install python3-pip. Luego escriba pip –upgrade install pip
- Si la ventana acoplable no está instalada, escriba sudo apt-get update y luego escriba sudo apt-get install docker-ce o escriba sudo apt-get docker.io
- Escriba docker – version
root@kali:/home/iicybersecurity/Downloads/jok3r# docker --version Docker version 18.06.1-ce, build e68fc7a
- Después de instalar el docker escriba cd docker
- Escriba sudo docker pull koutto / jok3r. Este comando instalará todas las dependencias o herramientas que necesita JOK3R
- Una vez instaladas las herramientas de JOK3R, escriba python3 jok3r.py –help
Atacante
vroot@kali:/home/iicybersecurity/Downloads/jok3r# python3 jok3r.py --help
____. __ ________ `Combine the best of...
| | ____ | | __\_____ \______ ...open-source Hacking Tools`
| |/ _ \| |/ / _(__ <_ __ \
/\__| ( (_) ) < / \ | \/
\________|\____/|__|_ \/______ /__| v2.0
\/ \/
~ Network & Web Pentest Framework ~[ Manage Toolbox | Automate Attacks | Chain Hacking Tools ]
usage:
python3 jok3r.py []
Supported commands:
toolbox Manage the toolbox
info View supported services/options/checks
db Define missions scopes, keep tracks of targets & view attacks results
attack Run checks against targets
optional arguments:
-h, --help show this help message and exit
- Escriba python3 jok3r.py toolbox –show-all
- toolbox es la lista de herramientas que se han instalado
- –Show-all mostrará todas las herramientas instaladas
root@kali:/home/iicybersecurity/Downloads/jok3r# python3 jok3r.py toolbox --show-all
____. __ ________ `Combine the best of...
| | ____ | | __\_____ \______ ...open-source Hacking Tools`
| |/ _ \| |/ / _(__ <_ __ \
/\__| ( (_) ) < / \ | \/
\________|\____/|__|_ \/______ /__| v2.0
\/ \/
~ Network & Web Pentest Framework ~[ Manage Toolbox | Automate Attacks | Chain Hacking Tools ] Toolbox content - all services +--------------------------------+----------+-----------------+-------------------------------------------------------------------------------------------------------------+ | Name | Service | Status/Update | Description | +--------------------------------+----------+-----------------+-------------------------------------------------------------------------------------------------------------+ | ajpy | ajp | OK | 2019-01-24 | AJP requests crafter in order to communicate with AJP connectors | | ftpmap | ftp | OK | 2019-01-24 | FTP Scanner detecting vulns based on softs/versions | | halberd | http | OK | 2019-01-24 | HTTP load balancer detector | | wafw00f | http | OK | 2019-01-24 | Identify and fingerprint WAF products protecting a website | | whatweb | http | OK | 2019-01-24 | Identify CMS, blogging platforms, JS libraries, Web servers | | optionsbleed | http | OK | 2019-01-24 | Test for the Optionsbleed bug in Apache httpd (CVE-2017-9798) | | clusterd | http | OK | 2019-01-24 | Application server attack toolkit (JBoss, ColdFusion, Weblogic, Tomcat, Railo, Axis2, Glassfish) | | wig | http | OK | 2019-01-24 | Identify several CMS and other administrative applications | | fingerprinter | http | OK | 2019-01-24 | CMS/LMS/Library versions fingerprinter | | cmsexplorer | http | OK | 2019-01-24 | Find plugins and themes installed in a CMS (WordPress, Drupal, Joomla, Mambo) | | nikto | http | OK | 2019-01-24 | Web server scanner | | iis-shortname-scanner | http | OK | 2019-01-24 | Scanner for IIS short filename (8.3) disclosure vulnerability | | davscan | http | OK | 2019-01-24 | Fingerprint servers, finds exploits, scans WebDAV | | shocker | http | OK | 2019-01-24 | Detect and exploit web servers vulnerable to Shellshock (CVE-2014-6271) | | loubia | http | OK | 2019-01-24 | Exploitation tool for Java deserialize on t3(s) (Weblogic) | | exploit-tomcat-cve2017-12617 | http | OK | 2019-01-24 | Exploit for Apache Tomcat (<9.0.1 (Beta), <8.5.23, <8.0.47, <7.0.8) JSP Upload Bypass RCE (CVE-2017-12617) | | exploit-weblogic-cve2017-3248 | http | OK | 2019-01-24 | Exploit for Weblogic RMI Registry UnicastRef Object Java Deserialization RCE (CVE-2017-3248) | | exploit-weblogic-cve2017-10271 | http | OK | 2019-01-24 | Exploit for Weblogic WLS-WSAT RCE (CVE-2017-10271) | | exploit-weblogic-cve2018-2893 | http | OK | 2019-01-24 | Exploit for Weblogic Java Deserialization RCE (CVE-2018-2893) | | struts-pwn-cve2017-9805 | http | OK | 2019-01-24 | Exploit for Apache Struts2 REST Plugin XStream RCE (CVE-2017-9805) | | struts-pwn-cve2018-11776 | http | OK | 2019-01-24 | Exploit for Apache Struts2 CVE-2018-11776 | | domiowned | http | OK | 2019-01-24 | Fingerprint/Exploit IBM/Lotus Domino servers | | cmsmap | http | OK | 2019-01-24 | Vulnerability scanner for CMS WordPress, Drupal, Joomla | | cmseek | http | OK | 2019-01-24 | Detect and bruteforce CMS | | drupwn | http | OK | 2019-01-24 | Fingerprint Drupal 7/8 and exploit CVE | | dirhunt | http | OK | 2019-01-24 | Find web directories without bruteforce | | photon | http | OK | 2019-01-24 | Fast we crawler that extracts urls, emails, files, website accounts, etc. | | angularjs-csti-scanner | http | OK | 2019-01-24 | Angular Client-Side Template Injection scanner | | wpforce | http | OK | 2019-01-24 | WordPress attack suite | | wpscan | http | OK | 2019-01-24 | WordPress vulnerability scanner | | wpseku | http | OK | 2019-01-24 | WordPress vulnerability scanner | | joomscan | http | OK | 2019-01-24 | Joomla vulnerability scanner by OWASP | | joomlascan | http | OK | 2019-01-24 | Joomla vulnerability scanner | | joomlavs | http | OK | 2019-01-24 | Joomla vulnerability scanner | | droopescan | http | OK | 2019-01-24 | Drupal & Silverstripe plugin-based vulnerability scanner | | magescan | http | OK | 2019-01-24 | Magento CMS scanner for information and misconfigurations | | vbscan | http | OK | 2019-01-24 | vBulletin vulnerability scanner by OWASP | | liferayscan | http | OK | 2019-01-24 | Liferay vulnerability scanner | | xbruteforcer | http | OK | 2019-01-24 | CMS bruteforce tool | | dirsearch | http | OK | 2019-01-24 | Web path scanner | | wfuzz | http | OK | 2019-01-24 | Web application fuzzer | | barmie | java-rmi | OK | 2019-01-24 | Java RMI enumeration and attack tool | | jmxbf | java-rmi | OK | 2019-01-24 | Bruteforce program to test weak accounts configured to access a JMX Registry | | jmxploit | java-rmi | OK | 2019-01-24 | JMX (post-)exploitation tool in Tomcat environment | | sjet | java-rmi | OK | 2019-01-24 | JMX exploitation tool for insecure configured JMX services | | twiddle | java-rmi | OK | 2019-01-24 | CLI-based JMX client | | jdwp-shellifier | jdwp | OK | 2019-01-24 | Exploitation tool to gain RCE on JDWP | | msdat | mssql | OK | 2019-01-24 | Microsoft SQL Database Attacking Tool | | changeme | multi | OK | 2019-01-24 | Default credentials scanner | | impacket | multi | OK | 2019-01-24 | Collection of Python classes for working with network protocols | | jexboss | multi | OK | 2019-01-24 | Exploitation tool for JBoss, Jenkins, Struts2, JMX (Tomcat) | | jok3r-scripts | multi | OK | 2019-01-24 | Various small stand-alone scripts and dependencies for other tools | | metasploit | multi | OK | 2019-01-24 | Metasploit framework | | nmap | multi | OK | 2019-01-24 | Nmap port scanner | | patator | multi | OK | 2019-01-24 | Multi-purpose brute-forcer, with a modular design and a flexible usage | | testssl | multi | OK | 2019-01-24 | TLS/SSL encryption checker | | tls-prober | multi | OK | 2019-01-24 | Tool to fingerprint SSL/TLS servers | | vuln-databases | multi | OK | 2019-01-24 | Vulnerabilities databases from Vulners.com, vuldb.com (NSE scripts) and exploit-db.com | | ysoserial | multi | OK | 2019-01-24 | Tool for generating payloads that exploit unsafe Java object deserialization | | odat | oracle | OK | 2019-01-24 | Oracle database attacking tool | | nullinux | smb | OK | 2019-01-24 | Enumeration tool for SMB on Windows | | smbmap | smb | OK | 2019-01-24 | SMB Shares enumeration tool | | smtp-user-enum | smtp | OK | 2019-01-24 | Enumerate valid users on SMTP via EXPN, VRFY or RCPT TO | | snmpwn | snmp | OK | 2019-01-24 | SNMPv3 User enumerator and Attack tool | | snmp-check | snmp | OK | 2019-01-24 | SNMP enumerator | | ssh-audit | ssh | OK | 2019-01-24 | SSH server auditing tool (banner, key exchange, encryption, mac, compression, compatibility, security, etc) | | osueta | ssh | OK | 2019-01-24 | Exploit for OpenSSH (versions <= 7.2 and >= 5.*) user enumeration timing attack | | libssh-scanner | ssh | OK | 2019-01-24 | Exploit for authentication bypass (CVE-2018-10933) in libssh 0.6+ (fixed in 0.7.6 and 0.8.4) | +--------------------------------+----------+-----------------+-------------------------------------------------------------------------------------------------------------+
- Esta herramienta ofrece opciones donde puede guardar todos los servicios escaneados en el destino. También puede ver qué servicio se ha ejecutado en el destino
- Para guardar primero tienes que crear la base de datos. Para eso escriba python3 jok3r.py db
- Para guardar primero tiene que crear la base de datos. Para eso teclee python3 jok3r.py db
- Para abrir más opciones en db, teclee help
root@kali:/home/iicybersecurity/Downloads/jok3r# python3 jok3r.py db
____. __ ________ `Combine the best of...
| | ____ | | __\_____ \______ ...open-source Hacking Tools`
| |/ _ \| |/ / _(__ <_ __ \
/\__| ( (_) ) < / \ | \/
\________|\____/|__|_ \/______ /__| v2.0
\/ \/
~ Network & Web Pentest Framework ~[ Manage Toolbox | Automate Attacks | Chain Hacking Tools ] The local database stores the missions, targets info & attacks results. This shell allows for easy access to this database. New missions can be added and scopes can be defined by importing new targets. ok3rdb[default]> help Documented commands (type help ): Attacks results results Attacks results Import nmap Import Nmap results Missions data creds Credentials in the current mission scope hosts Hosts in the current mission scope mission Manage missions services Services in the current mission scope Other alias Manage aliases help Display this help message history View, run, edit, save, or clear previously entered commands macro Manage macros quit Exit this application set Set a settable parameter or show current settings of parameters shell Execute a command as if at the OS prompt
- Luego escriba missionproproject
- Después de crear la misión, presione ctrl + c
- Luego escriba python3 jok3r.py attack -t http://192.168.1.105/ –add testproject
- attack se usa para comprobar el objetivo
- -t se utiliza para entrar en destino.
- –add se utiliza para guardar los resultados en la base de datos de JOK3R
root@kali:/home/iicybersecurity/Downloads/jok3r# python3 jok3r.py attack -t http://192.168.1.105/ --add testproject
____. __ ________ `Combine the best of...
| | ____ | | __\_____ \______ ...open-source Hacking Tools`
| |/ _ \| |/ / _(__ <_ __ \
/\__| ( (_) ) < / \ | \/
\________|\____/|__|_ \/______ /__| v2.0
\/ \/
~ Network & Web Pentest Framework ~[ Manage Toolbox | Automate Attacks | Chain Hacking Tools ]
[] URL given as target, targeted service is HTTP [] Check if target is reachable and grab banner using Nmap…
[+] Target URL http://192.168.1.105/ is reachable
[] Results from this attack will be saved under mission "testproject" in database [] A matching service has been found in the database
[+] Updated: host 192.168.1.105 | port 80/tcp | service http
+----+---------------+----------+------+-------+---------+-------------------------------------------------------------------+-----------------------+
| id | IP | Hostname | Port | Proto | Service | Banner | URL |
+----+---------------+----------+------+-------+---------+-------------------------------------------------------------------+-----------------------+
| >1 | 192.168.1.105 | dvwa | 80 | tcp | http | product: Apache httpd version: 2.2.14 extrainfo: (Unix) DAV/2 | http://192.168.1.105/ |
| | | | | | | mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 | |
| | | | | | | mod_perl/2.0.4 Perl/v5.10.1 | |
+----+---------------+----------+------+-------+---------+-------------------------------------------------------------------+-----------------------+
[?] Start attack ? [Y/n] Y
[*] HTTP Response headers:
Date: Thu, 24 Jan 2019 09:55:41 GMT
Server: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1
X-Powered-By: PHP/5.3.1
Set-Cookie: PHPSESSID=c03n54d2gciu1rh9niscqmij67; path=/
Set-Cookie: security=high
Expires: Tue, 23 Jun 2009 12:00:00 GMT
Cache-Control: no-cache, must-revalidate
Pragma: no-cache
Content-Length: 1224
Content-Type: text/html;charset=utf-8
[] Context-specific options set for this target: +----------+-------+ | option | value | +----------+-------+ | language | php | +----------+-------+ [] [SMART] Running initialization method…
{'Perl', 'Apache'}
[] [SMART] Wappalyzer fingerprinting returns: ['apache', 'mod_ssl', 'mod_perl', 'unix', 'php', 'perl', 'openssl'] [] [SMART] Detected option (no update): language = php
- Después de ejecutar la consulta anterior, JOCK3R ha iniciado el escaneo de nmap en todos los servicios. Esta herramienta escaneará todos los servicios
- El servicio anterior ha detectado el idioma y el servidor del sitio web de destino
- La información anterior se puede utilizar en otras actividades de hacking
- Para escanear todos los servicios, simplemente escriba Y cuando se le solicite escanear otro servicio. Hacer específico al escanear
[>] [Recon][Check 13/14] crawling-fast > Crawl website quickly, analyze interesting files/directories
[?] Run command #01 ? [Y/n/t/w/q] Y
cmd> dirhunt http://192.168.1.105/
Welcome to Dirhunt v0.6.0 using Python 2.7.15+
Starting…
[302] http://192.168.1.105/ (Redirect)
Redirect to: http://192.168.1.105/
[200] http://192.168.1.105/login.php (HTML document)
Index file found: index.php
[200] http://192.168.1.105/dvwa/css/ (Index Of) (Nothing interesting)
[200] http://192.168.1.105/dvwa/ (Index Of) (Nothing interesting)
[200] http://192.168.1.105/dvwa/images/ (Index Of) (Nothing interesting)
[200] http://192.168.1.105/dvwa/js/ (Index Of) (Nothing interesting)
[200] http://192.168.1.105/dvwa/includes/ (Index Of)
Interesting extension files: dvwaPage.inc.php (13K), dvwaPhpIds.inc.php (2.5K)
[200] http://192.168.1.105/dvwa/includes/DBMS/ (Index Of)
Interesting extension files: DBMS.php (2.4K), MySQL.php (2.9K), PGSQL.php (3.4K)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━
Starting…
http://192.168.1.105/login.php
(200) ( 154B) http://192.168.1.105/dvwa/includes/dvwaPage.inc.php [13K ]
Warning: define() expects at least 2 parameters,
(200) ( 156B) http://192.168.1.105/dvwa/includes/dvwaPhpIds.inc.php [2.5K]
Warning: define() expects at least 2 parameters,
(200) ( 154B) http://192.168.1.105/dvwa/includes/DBMS/MySQL.php [2.9K]
Fatal error: Call to undefined function dvwaMessa
(200) ( 626B) http://192.168.1.105/dvwa/includes/DBMS/DBMS.php [2.4K]
Notice: Undefined variable: DBMS in /opt/lampp (200) ( 154B) http://192.168.1.105/dvwa/includes/DBMS/PGSQL.php [3.4K]
Fatal error: Call to undefined function dvwaMessa
[>] [Recon][Check 14/14] crawling-fast2 > Crawl website and extract URLs, files, intel & endpoints
- El servicio anterior utilizado es el rastreo donde esta herramienta intenta analizar archivos y directorios que se pueden usar en futuros ataques de hacking
- Mientras se rastrean algunas de las páginas, el directorio dvwa denominado como incluye tiene páginas como mysql.php, dbms.php, pgsql que se pueden usar en otras actividades de hacking
- El escaneo muestra las vulnerabilidades mencionadas en CVE
[>] [Vulnscan][Check 01/29] vuln-lookup > Vulnerability lookup in Vulners.com (NSE scripts) and exploit-db.com (lots of false positive !) [?] Run command #01 ? [Y/n/t/w/q] Y cmd> sudo nmap -sT -sV -T5 -Pn -p 80 --script nmap-vulners/vulners.nse --script-args vulscandb=scipvuldb.csv 192.168.1.105 -oX /tmp/nmaptmp.xml; ./exploit-database/searchsploit --nmap /tmp/nmaptmp.xml; sudo rm -f /tmp/nmaptmp.xml Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-24 06:02 EST Nmap scan report for dvwa (192.168.1.105) Host is up (0.00046s latency). PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.2.14 ((Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1) |http-server-header: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 | vulners: | cpe:/a:apache:http_server:2.2.14: | CVE-2010-0425 10.0 https://vulners.com/cve/CVE-2010-0425 | CVE-2011-3192 7.8 https://vulners.com/cve/CVE-2011-3192 | CVE-2013-2249 7.5 https://vulners.com/cve/CVE-2013-2249 | CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679 | CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668 | CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167 | CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169 | CVE-2012-0883 6.9 https://vulners.com/cve/CVE-2012-0883 | CVE-2009-3555 5.8 https://vulners.com/cve/CVE-2009-3555 | CVE-2013-1862 5.1 https://vulners.com/cve/CVE-2013-1862 | CVE-2014-0098 5.0 https://vulners.com/cve/CVE-2014-0098 | CVE-2007-6750 5.0 https://vulners.com/cve/CVE-2007-6750 | CVE-2013-6438 5.0 https://vulners.com/cve/CVE-2013-6438 | CVE-2011-3368 5.0 https://vulners.com/cve/CVE-2011-3368 | CVE-2012-4557 5.0 https://vulners.com/cve/CVE-2012-4557 | CVE-2014-0231 5.0 https://vulners.com/cve/CVE-2014-0231 | CVE-2010-0408 5.0 https://vulners.com/cve/CVE-2010-0408 | CVE-2010-1452 5.0 https://vulners.com/cve/CVE-2010-1452 | CVE-2010-2068 5.0 https://vulners.com/cve/CVE-2010-2068 | CVE-2012-0031 4.6 https://vulners.com/cve/CVE-2012-0031 | CVE-2011-3607 4.4 https://vulners.com/cve/CVE-2011-3607 | CVE-2012-0053 4.3 https://vulners.com/cve/CVE-2012-0053 | CVE-2011-3348 4.3 https://vulners.com/cve/CVE-2011-3348 | CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975 | CVE-2010-0434 4.3 https://vulners.com/cve/CVE-2010-0434 | CVE-2011-4317 4.3 https://vulners.com/cve/CVE-2011-4317 | CVE-2013-1896 4.3 https://vulners.com/cve/CVE-2013-1896 | CVE-2011-0419 4.3 https://vulners.com/cve/CVE-2011-0419 | CVE-2012-4558 4.3 https://vulners.com/cve/CVE-2012-4558 | CVE-2012-3499 4.3 https://vulners.com/cve/CVE-2012-3499 | CVE-2011-3639 4.3 https://vulners.com/cve/CVE-2011-3639 | CVE-2016-8612 3.3 https://vulners.com/cve/CVE-2016-8612 | CVE-2012-2687 2.6 https://vulners.com/cve/CVE-2012-2687 | CVE-2011-4415 1.2 https://vulners.com/cve/CVE-2011-4415 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 7.72 seconds [i] SearchSploit's XML mode (without verbose enabled). To enable: searchsploit -v --xml… [i] Reading: '/tmp/nmaptmp.xml' [i] ./exploit-database/searchsploit -t apache httpd 2 2 14
- Después de ejecutar la consulta anterior, se muestran las vulnerabilidades CVE que se pueden usar en futuros ataques de hacking
- Se muestran muchas vulnerabilidades en las que figuran CVE los últimos años
- Más escaneo utiliza nikto para escanear en busca de vulnerabilidades web
[>] [Vulnscan][Check 03/29] vulnscan-multi-nikto > Check for multiple web vulnerabilities/misconfigurations [?] Run command #01 ? [Y/n/t/w/q] Y cmd> cd program; perl ./nikto.pl -host dvwa -port 80 - Nikto v2.1.6 Target IP: 192.168.1.105 Target Hostname: dvwa Target Port: 80 + Start Time: 2019-01-24 06:14:56 (GMT-5) Server: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 Retrieved x-powered-by header: PHP/5.3.1 The anti-clickjacking X-Frame-Options header is not present. The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type Cookie PHPSESSID created without the httponly flag Cookie security created without the httponly flag Root page / redirects to: login.php Server leaks inodes via ETags, header found with file /robots.txt, inode: 9210, size: 26, mtime: Tue Aug 24 15:45:32 2010 Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var Perl/v5.10.1 appears to be outdated (current is at least v5.14.2) mod_ssl/2.2.14 appears to be outdated (current is at least 2.8.31) (may depend on server version) Apache/2.2.14 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current. PHP/5.3.1 appears to be outdated (current is at least 5.6.9). PHP 5.5.25 and 5.4.41 are also current. mod_perl/2.0.4 appears to be outdated (current is at least 2.0.7) OpenSSL/0.9.8l appears to be outdated (current is at least 1.0.1j). OpenSSL 1.0.0o and 0.9.8zc are also current. mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756. OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST OSVDB-112004: /cgi-bin/printenv: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271). OSVDB-112004: /cgi-bin/printenv: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6278). OSVDB-3268: /config/: Directory indexing found. /config/: Configuration information may be available remotely. OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. OSVDB-561: /server-status: This reveals Apache information. Comment out appropriate line in the Apache conf file or restrict access to allowed sources. OSVDB-3092: /phpmyadmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts. OSVDB-3092: /phpmyadmin/ChangeLog: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts. OSVDB-3233: /cgi-bin/printenv: Apache 2.0 default script is executable and gives server environment variables. All default scripts should be removed. It may also allow XSS types of attacks. http://www.securityfocus.com/bid/4431. OSVDB-3233: /cgi-bin/test-cgi: Apache 2.0 default script is executable and reveals system information. All default scripts should be removed. OSVDB-3268: /icons/: Directory indexing found. OSVDB-3268: /docs/: Directory indexing found. OSVDB-3092: /CHANGELOG.txt: A changelog was found. OSVDB-3233: /icons/README: Apache default file found. /login.php: Admin login page/section found. /phpmyadmin/: phpMyAdmin directory found OSVDB-3092: /.svn/entries: Subversion Entries file may contain directory listing information. OSVDB-3092: /phpmyadmin/Documentation.html: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts. /CHANGELOG.txt: Version number implies that there is a SQL Injection in Drupal 7, can be used for authentication bypass (Drupageddon: see https://www.sektioneins.de/advisories/advisory-012014-drupal-pre-auth-sql-injection-vulnerability.html). /server-status: Apache server-status interface found (pass protected) 8167 requests: 0 error(s) and 39 item(s) reported on remote host + End Time: 2019-01-24 06:15:35 (GMT-5) (39 seconds) 1 host(s) tested
- La herramienta anterior muestra que muchas de las configuraciones no se realizan correctamente, por eso los ataques de fuerza bruta se pueden hacer fácilmente
- Algunas de las versiones de apache, perl están desactualizadas. Hay ciertas solicitudes HTTP que pueden generar información confidencial
- Esta información puede ser utilizada en otras actividades de hacking
- También ejecuta herramienta como changme
cmd> python3 changeme.py -v --protocols http 192.168.1.105:80
#####################################################
_
| |_ _ _ _ _ _ _ _ _ _
/ _| ' \ / | '_ \ / _ |/ \ '_ ` _ \ / _ \
| (| | | | (| | | | | (| | / | | | | | __/
___|| ||__,|| ||_, |___|| || ||__|
|_/
v1.1
Default Credential Scanner by @ztgrace
#####################################################
Loaded 113 default credential profiles
Loaded 324 default credentials
[06:28:15] Configured protocols: http
[06:28:15] Loading creds into queue
[06:28:15] Fingerprinting completed
[06:28:15] Scanning Completed
No default credentials found
[*] [SMART] Running post-check method "changeme_valid_creds" …
[*] [Vulnscan][Check 05/29] webdav-scan-davscan > Skipped because target's context is not matching
[*] [Vulnscan][Check 06/29] webdav-scan-msf > Skipped because target's context is not matching
[*] [Vulnscan][Check 07/29] webdav-internal-ip-disclosure > Skipped because target's context is not matching
[*] [Vulnscan][Check 08/29] webdav-website-content > Skipped because target's context is not matching
- Después de explorar más el destino, muestra que el contexto de destino no coincide porque esta herramienta detecta las credenciales de puerta trasera predeterminadas
- Ahora está escaneando con otra herramienta de choque de shell que muestra si el objetivo es vulnerable a la explotación
[>] [Vulnscan][Check 11/29] shellshock-scan > Detect if web server is vulnerable to Shellshock (CVE-2014-6271)
[?] Run command #01 ? [Y/n/t/w/q] Y
cmd> python2.7 shocker.py --Host 192.168.1.105 --port 80
.-. . .
( )| |
-. |--. .-. .-.|.-. .-. .--. ( )| |( )( |-.'(.-' | -' ' --' -''-`--'' v1.1
Tom Watson, tom.watson@nccgroup.trust
https://www.github.com/nccgroup/shocker
Released under the GNU Affero General Public License
(https://www.gnu.org/licenses/agpl-3.0.html)
[+] 402 potential targets imported from ./shocker-cgi_list
[+] Checking connectivity with target…
[+] Target was reachable
[+] Looking for vulnerabilities on 192.168.1.105:80
>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
[+] 3 potential targets found, attempting exploits
[+] The following URLs appear to be exploitable:
[1] http://192.168.1.105:80/cgi-bin/printenv
[2] http://192.168.1.105:80/cgi-bin/test-cgi
- La herramienta Shell Shocker muestra que el objetivo puede ser explotado usando los 2 enlaces anteriores. Esta información puede ser utilizada en otras actividades de hacking
- Algunas veces, si la herramienta se bloquea durante el funcionamiento, presione ctrl + c para iniciar un nuevo escaneo
- El escaneo muestra que algunas de las herramientas no son compatibles como se muestra a continuación
Category > Exploit [*] [Exploit][Check 01/11] jboss-deploy-shell > Skipped because target's context is not matching [*] [Exploit][Check 02/11] struts2-rce-cve2017-5638 > Skipped because target's context is not matching [*] [Exploit][Check 03/11] struts2-rce-cve2017-9805 > Skipped because target's context is not matching [*] [Exploit][Check 04/11] struts2-rce-cve2018-11776 > Skipped because target's context is not matching [*] [Exploit][Check 05/11] tomcat-rce-cve2017-12617 > Skipped because target's context is not matching [*] [Exploit][Check 06/11] jenkins-cliport-deserialize > Skipped because target's context is not matching [*] [Exploit][Check 07/11] weblogic-t3-deserialize-cve2015-4852 > Skipped because target's context is not matching [*] [Exploit][Check 08/11] weblogic-t3-deserialize-cve2017-3248 > Skipped because target's context is not matching [*] [Exploit][Check 09/11] weblogic-t3-deserialize-cve2018-2893 > Skipped because target's context is not matching [*] [Exploit][Check 10/11] weblogic-wls-wsat-cve2017-10271 > Skipped because target's context is not matching [*] [Exploit][Check 11/11] drupal-cve-exploit > Skipped because target's context is not matching
- Las herramientas anteriores no son compatibles ya que las herramientas son de contexto diferente y el objetivo tiene diferentes funcionalidades
- Usando otra herramienta wfuzz. Wfuzz es una aplicación web de fuerza bruta
cmd> ./wfuzz -c -u http://192.168.1.105//FUZZ -w /home/iicybersecurity/Downloads/jok3r/wordlists/services/http/discovery/opendoor-paths.txt --hc 400,404,500,000 Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information. Wfuzz 2.3.4 - The Web Fuzzer * Target: http://192.168.1.105//FUZZ Total requests: 36942 ================================================================== ID Response Lines Word Chars Payload 000431: C=200 101 L 135 W 1480 Ch ".svn/all-wcprops" 000432: C=200 572 L 151 W 2726 Ch ".svn/entries" 000434: C=200 12 L 61 W 803 Ch ".svn/prop-base/" 000435: C=200 11 L 52 W 667 Ch ".svn/props/" 000436: C=200 25 L 175 W 2455 Ch ".svn/text-base/" 000437: C=200 4 L 39 W 538 Ch ".svn/text-base/index.php.svn-base" 000438: C=200 14 L 76 W 1010 Ch ".svn/tmp/" 001959: C=200 129 L 594 W 5066 Ch "CHANGELOG.txt" 001973: C=200 622 L 5214 W 33107 Ch "COPYING.txt" 002936: C=200 119 L 706 W 4934 Ch "README.txt" 004298: C=302 0 L 0 W 0 Ch "about.php" 004948: C=404 46 L 113 W 1118 Ch "admin/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector005061: C=404 46 L 113 W 1118 Ch "admin/fckeditor/editor/filemanager/browser/default/connectors/asp/connector005062: C=404 46 L 113 W 1118 Ch "admin/fckeditor/editor/filemanager/browser/default/connectors/aspx/connecto005063: C=404 46 L 113 W 1118 Ch "admin/fckeditor/editor/filemanager/browser/default/connectors/php/connector006673: C=404 46 L 113 W 1118 Ch "all/modules/ogdi_field/plugins/dataTables/extras/TableTools/media/swf/ZeroC007150: C=404 46 L 113 W 1118 Ch "apps/trac/pragyan/browser/trunk/cms/modules/article/fckEditor/editor/filema010085: C=403 44 L 109 W 1122 Ch "cgi-bin/" 010087: C=403 44 L 108 W 1108 Ch "cgi-bin/awstats.pl" 011523: C=200 12 L 61 W 776 Ch "config/" 013659: C=200 11 L 52 W 650 Ch "docs/" 013930: C=404 46 L 113 W 1118 Ch "dreamedit/includes/FCKEditor_/editor/filemanager/browser/mcpuk/browser.html014071: C=200 15 L 84 W 1101 Ch "dvwa/" 015076: C=403 44 L 109 W 1122 Ch "error/" 015477: C=200 12 L 60 W 772 Ch "external/" 015653: C=200 1 L 6 W 1549 Ch "favicon.ico" 015697: C=404 46 L 113 W 1118 Ch "fckeditor/editor/filemanager/browser/default/connectors/aspx/connector.aspx016920: C=404 46 L 113 W 1118 Ch "galeria/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folder016925: C=404 46 L 113 W 1118 Ch "galerie/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folder016955: C=404 46 L 113 W 1118 Ch "gallery/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folder018593: C=200 167 L 1300 W 18876 Ch "icons/" 018642: C=302 0 L 0 W 0 Ch "ids_log.php" 019087: C=404 46 L 113 W 1118 Ch "includes/fckeditor/editor/filemanager/browser/default/connectors/asp/connec019088: C=404 46 L 113 W 1118 Ch "includes/fckeditor/editor/filemanager/browser/default/connectors/aspx/conne019089: C=404 46 L 113 W 1118 Ch "includes/fckeditor/editor/filemanager/browser/default/connectors/php/connec019142: C=302 0 L 0 W 0 Ch "index.php" 019762: C=404 46 L 113 W 1118 Ch "ispcp/browser/trunk/gui/tools/filemanager/plugins/fckeditor/editor/filemana020212: C=404 46 L 113 W 1118 Ch "js/fckeditor/editor/filemanager/browser/default/connectors/php/connector.ph021551: C=200 65 L 108 W 1224 Ch "login.php" 021667: C=302 0 L 0 W 0 Ch "logout.php" 025961: C=404 46 L 113 W 1118 Ch "photo/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folder.p026010: C=404 46 L 113 W 1118 Ch "photos/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folder.026053: C=200 4 L 20 W 148 Ch "php.ini" 026339: C=302 0 L 0 W 0 Ch "phpinfo.php" 026390: C=200 0 L 0 W 0 Ch "phpmyadmin/phpinfo.php" 026389: C=200 72 L 206 W 2726 Ch "phpmyadmin/" 026673: C=404 46 L 113 W 1118 Ch "plugins/fckeditor/fckeditor/editor/filemanager/browser/default/browser.html026675: C=404 46 L 113 W 1118 Ch "plugins/p_fckeditor/fckeditor/editor/filemanager/browser/default/browser.ht026676: C=404 46 L 113 W 1118 Ch "plugins/p_fckeditor/fckeditor/editor/filemanager/connectors/uploadtest.html028932: C=200 1 L 4 W 26 Ch "robots.txt" 029580: C=404 46 L 113 W 1118 Ch "script/jqueryplugins/dataTables/extras/TableTools/media/swf/ZeroClipboard.s029817: C=302 0 L 0 W 0 Ch "security.php" 029987: C=200 51 L 292 W 2787 Ch "server-status/" 029986: C=200 1253 L 8719 W 120232 Ch "server-info/" 030080: C=404 46 L 113 W 1118 Ch "servlet/Oracle.xml.xsql.XSQLServlet/soapdocs/webapps/soap/WEB-INF/config/so030101: C=404 46 L 113 W 1118 Ch "servlet/oracle.xml.xsql.XSQLServlet/soapdocs/webapps/soap/WEB-INF/config/so030182: C=200 80 L 227 W 3549 Ch "setup.php" 036787: C=404 46 L 113 W 1118 Ch "zenphoto/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folde Total time: 110.2424 Processed Requests: 36942 Filtered Requests: 36874 Requests/sec.: 335.0979
- La consulta anterior intenta encontrar directorios, archivos que no están vinculados directamente. Después de ejecutar la consulta anterior, wfuzz ha encontrado ajax, servlets y algunos complementos
- Estos datos pueden ser utilizados en otros ataques de hacking
Como puede ver, esta herramienta comprende muchas herramientas pequeñas que muestran mucha información vital. Para seguir escaneando puedes seguir otros tutoriales.
VULNERABILIDADES CRÍTICAS EN ENRUTADORES CISCO AFECTAN MILES DE EMPRESAS EN LATINOAMÉRICA

La firma ya ha lanzado parches de actualización para diversos productos empleados por PYMES
La firma tecnológica Cisco lanzó recientemente parches de actualización para abordar dos vulnerabilidades críticas presentes en los enrutadores RV320 y RV325, productos ampliamente utilizados en pequeñas empresas. Acorde a especialistas en seguridad en redes, la primera de estas fallas (CVE-2019-1653) podría ser explotada por atacantes remotos para acceder a información confidencial, mientras que la segunda (CVE-2019-1652) es una falla para inyección de comandos.
El verdadero problema para Cisco es que algunos hackers han estado atacando los enrutadores RV320 y RV325 usando nuevos exploits. Después de la divulgación de la prueba de concepto del exploit inicial, los hackers comenzaron la búsqueda de dispositivos vulnerables en Internet para tratar de comprometerlos.
Ambas vulnerabilidades se encuentran en la interfaz de administración web de los enrutadores comprometidos, reportan especialistas en seguridad en redes del Instituto Internacional de Seguridad Cibernética. Encadenando las dos fallas, un hacker puede tomar el control de estos dispositivos, los atacantes explotan las vulnerabilidades para obtener contraseñas de cunetas privilegiadas y ejecutar comando arbitrario.
Especialistas de una firma de ciberseguridad fueron los encargados de reportar estas fallas a Cisco, las pruebas de código para la explotación fueron reveladas al público algunos días después de que la empresa lanzara los parches de actualización. Los expertos publicaron la prueba de concepto para vulnerabilidades de inyección de comandos, de divulgación de información y de fuga de datos.
Al buscar en Shodan alguno de los modelos de enrutadores comprometidos es posible encontrar decenas de miles de estos dispositivos funcionando en línea.
Troy Mursch, especialista en seguridad en redes realizó su propio escaneo buscando los sistemas vulnerables, descubriendo alrededor de 9 mil 600 enrutadores expuestos en línea (6 mil 247 enrutadores Cisco RV320 y 3 mil 410 enrutadores Cisco RV325).
Mursch describió en un mapa la distribución geográfica de los enrutadores comprometidos, demostrando que la mayoría de estos dispositivos se encuentran en Estados Unidos.
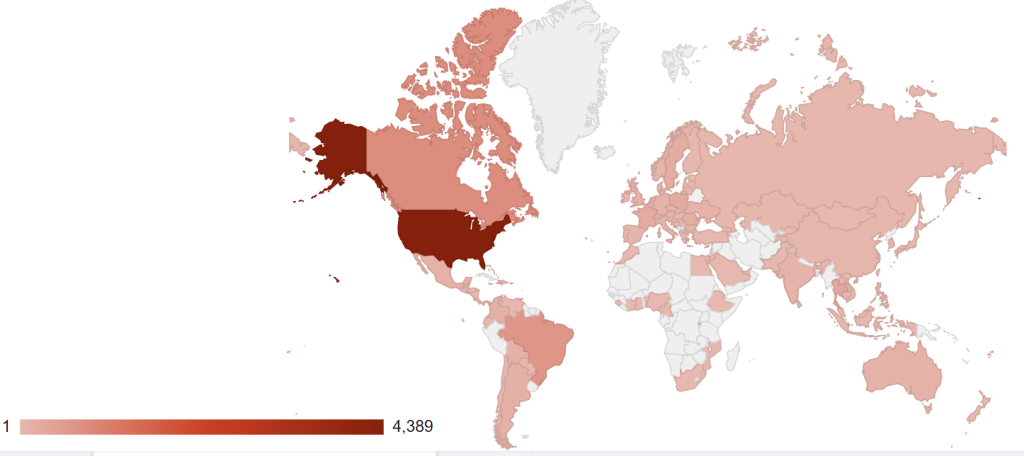
“Aunque la investigación que realizamos será publicada en breve, las direcciones IP de los enrutadores de Cisco afectados por estas fallas no serán reveladas, ya que se trata de información sensible”, comentó Troy Mursch en su blog.
JAPÓN PLANEA HACKING MASIVO DE EQUIPOS IOT DE SUS CIUDADANOS

El gobierno japonés intentará proteger los dispositivos IoT antes de las olimpiadas de Tokio 2020 para prevenir ciberataques
El pasado viernes el gobierno de Japón aprobó una enmienda que otorga a sus empleados públicos la facultad para hackear cualquier dispositivo de Internet de las Cosas (IoT) de sus ciudadanos, acorde a especialistas en seguridad en redes del Instituto Internacional de Seguridad Cibernética, esta medida forma parte de una inusual y muy invasiva investigación sobre equipos IoT vulnerables.
Esta investigación será realizada por empleados del Instituto Nacional de Tecnología de la Información y Comunicaciones de Japón (NICT), con la supervisión del Ministerio de Asuntos Internos, informó el gobierno japonés.
La legislación establece que los empleados del NICT podrán utilizar diccionarios de contraseñas predeterminados para intentar acceder a los dispositivos IoT de los consumidores. Con esto se pretende reunir una lista de equipos IoT poco seguros (con contraseñas predeterminadas o fáciles de adivinar) para que el gobierno, en colaboración con importantes empresas de telecomunicaciones, puedan tomar decisiones y alertar a los propietarios de estos equipos para lograr reforzar la seguridad en redes.
La investigación comenzará en los próximos días, enfocándose principalmente en enrutadores y cámaras web. El gobierno japonés espera analizar alrededor de 200 millones de dispositivos IoT en hogares y organizaciones.
Informes de especialistas en seguridad en redes afirman que los ciberataques dirigidos a dispositivos IoT en Japón equivalen a la tercera parte de todos los ciberataques reportados al año en el país, lo que podría incrementar durante los próximos Juegos Olímpicos de Tokio 2020, pues el gobierno japonés sabe que grupos de hackers están siempre a la expectativa de esta clase de eventos para atacar importantes infraestructuras de TI.
Durante los Juegos Olímpicos de Invierno de 2018 en PyeongChang, Corea del Sur, grupos de hackers auspiciados por el gobierno ruso desplegaron el malware “Olympic Destroyer” contra la infraestructura informática sudcoreana, todo como represalia por la decisión del Comité Olímpico Internacional (COI) de expulsar a cientos de atletas rusos de la competencia.
Además, los mismos hackers construyeron VPNFilter, una gigantesca botnet, usando equipos IoT domésticos con la que planeaban cortar la transmisión de la final de la Liga de Campeones de la UEFA de 2018 en Kiev, acorde a informes de las agencias de inteligencia de Ucrania.
Tal como se anticipaba, la decisión del gobierno japonés ha provocado indignación entre los ciudadanos y grupos de activistas de la privacidad. Los inconformes argumentan que esta es una medida innecesaria, pues basta con que el gobierno japonés implemente una campaña de concientización sobre la seguridad de estos dispositivos.
Por su parte, el gobierno de Japón considera que esta es una medida legítima, debido a que la mayoría de las botnets IoT son creadas por los hackers gracias a la poca seguridad con la que cuentan esta clase de dispositivos. Además, aunque una botnet también puede ser creada explotando vulnerabilidades en los enrutadores, la forma más utilizada es corrompiendo los equipos sin medidas de seguridad.
DEPARTAMENTOS DE POLICÍA ENCRIPTAN SUS RADIOCOMUNICACIONES; PRENSA Y CRIMINALES ESTÁN PREOCUPADOS

Reporteros locales verán entorpecida su labor debido a esta medida de la policía de Colorado
Especialistas en seguridad en redes del Instituto Internacional de Seguridad Cibernética reportan que al menos diez de las agencias policiales de Colorado, E.U., han decidido implementar cifrado en todas sus comunicaciones de radio, medida que antes aplicaba solamente a las operaciones consideradas ‘sensibles’. Debido a esta nueva política, los periodistas ya no podrán utilizar escáneres o aplicaciones móviles para rastrear las llamadas policiales.
“Aplicar encriptación a nuestras comunicaciones mejorará la seguridad y la efectividad de los departamentos de policía”, mencionan funcionarios del estado de Colorado. “No sólo los periodistas usaban esta clase de tecnología, también criminales y sospechosos sacaban ventaja de escuchar nuestras llamadas”, añadieron los funcionarios.
Sin embargo, expertos en seguridad en redes consideran que esto afecta principalmente a los periodistas, pues les resultará más complicado acudir a los lugares donde se presentan los hechos relevantes para su trabajo, causa razonable para argumentar que las agencias de policía están limitando la transparencia en su actuar.
Aún así, esto no es algo que los activistas de la privacidad o alguna firma de ciberseguridad consideren intrínsecamente malo; la encriptación de las comunicaciones es, de hecho, algo deseable en la actualidad. El cifrado protege la información sensible de individuos y organizaciones contra los hackers maliciosos, como datos financieros, compras en línea o incluso nuestras identidades, consideran expertos en seguridad en redes.
Además, en estos días se ocurren múltiples incidentes de seguridad de datos que involucran a organizaciones de cualquier tamaño que carecen de los protocolos y medidas de seguridad de la información adecuadas, actores maliciosos de toda clase siempre se encuentran al acecho de las debilidades que permiten acceder a información de millones de personas. Las personas en verdad deben ser conscientes de la importancia de la privacidad de su información, del mismo modo que alguien cierra las puertas de su casa con llave antes de salir, los usuarios de servicios en línea deben proteger sus datos con medidas como contraseñas seguras o autenticación multi factor. Por lo tanto, aunque esta medida de la policía de Colorado puede ser polémica, también podría resultar benéfica para muchos.
DISTRIBUTED DENIAL OF SECRETS: UN NUEVO COMPETIDOR PARA WIKILEAKS
El ciberactivismo ahora cuenta con un nuevo rostro anónimo
Acorde a Salvador Ruiz, especialista en seguridad en redes en el Instituto Internacional de Seguridad Cibernética, Distributed Denial of Secrets (DDOS) es un colectivo dedicado a la transparencia cuyo objetivo principal es permitir la transmisión gratuita de información de interés público. DDOS tiene como premisa evitar cualquier inclinación política, corporativa o personal, y simplemente actuar como un faro de información disponible. Como colectivo, DDOS no respalda ninguna causa, idea o mensaje más allá de garantizar que la información esté disponible para quienes más la necesitan: las personas.
Cómo acceder: https://ddosecretspzwfy7.onion.to/
El grupo anunció una próxima filtración masiva de datos relacionados con oligarcas, miembros de la iglesia, empresarios y políticos rusos.
Si bien el equipo de DDOS se complace en servir como un índice para los datos de todas las variedades, primordialmente sigue estos dos criterios:
- ¿Son los datos de interés público?
- ¿Se puede comprobar de primera mano la veracidad del contenido?
El Colectivo
A menos que ya sea público, o según lo autorice su fuente, DDOS no divulga la identidad de las fuentes de ninguna información recibida, y está totalmente comprometido a garantizar su anonimato contra todas las amenazas. DDOS nunca podría aconsejar a los informantes sobre el procedimiento correcto para transferir datos a su plataforma de nadie más, pero puede actuar como un escudo para ese proceso y compartir consejos de su experiencia. A menudo, su función es no solo hacer que los datos estén disponibles, sino también actuar como un guardia de anonimato para pasar los datos a los periodistas y otras figuras mejor posicionadas para interrogarlos.
DDOS es un equipo pequeño, pero su alcance se extiende mucho más allá de los miembros, no todos los que están en la lista son reconocidos por su propia preferencia. Los miembros de DDOS han trabajado juntos de manera informal durante muchos años y han desarrollado conexiones profundas en el campo de la recopilación de datos, la investigación, el periodismo, el activismo y la tecnología. En 2018, los miembros de DDOS decidieron reunir su experiencia y tiempo para crear un proyecto unificado que represente sus objetivos compartidos, y proporcionar una plataforma en la que terceros puedan confiar.
El estado moderno de las organizaciones dedicadas a la recopilación de ‘filtraciones’ se ha deteriorado rápidamente, envenenado por sus propios egos e intereses. La visión de DDOS es tratar a estos datos como un recurso y un registro; estos datos nunca podrán contar toda la historia. DDOS confía en que el público sea responsable con los datos, y se los abre para que los examine rigurosamente. Con el tiempo, la verdad siempre podrá emerger.
El Equipo
Emma Best – @NatSecGeek
Emma es una periodista independiente que ha pasado más años peleando por el cumplimiento de la Ley de la Libertad de la Información que la mayoría de las personas que han pasado leyendo las noticias. Conocida por su tenacidad de encontrar siempre la siguiente pista y penetrar en los muros burocráticos del gobierno, tiene un ojo atento a los detalles en cada documento y es una despiadada defensora de la verdad, incluso cuando nadie más se atreve a profundizar.
“Vexsome” – Buró Federal de Investigaciones, 2016
“The Architect”
Este es el seudónimo del genio técnico de DDOS que prefiere permanecer en el anonimato. No es ajeno a la controversia y ha estado involucrado en el activismo de la privacidad y la tecnología durante al menos 10 años. “The Architect” es el principal responsable de asesorar sobre la seguridad operativa del colectivo y mantiene las operaciones web y técnicas para el grupo.
Qué necesita DDOS
DDOS siempre está buscando expandir sus conjuntos de datos disponibles. Pueden considerar casi cualquier dato, pero están buscando activamente la información a continuación. Si puedes ayudarles a encontrar esta información, sería muy apreciado.
Emails filtrados de ACAPOR (Torrent Hash: 4b92fe94ccb803d6c5b97abc4c7ebdf706290539)
Emails de Filipe Menezes (Torrent Hash: 2866dc3538d12d99c88eb254591773d3821d939c)
Goldcorp (Torrent Hash: 0c385c2010e8a47e046ac8284f2f848c3ce5f8de)
Presuntos emails del Comité Central de Elecciones en Ucrania (Torrent Hash: 2df1c468641911537e3fbd22647c4bd14afebed7)
Lanzamientos de Anonymous en Bulgaria, Grecia o España
Filtraciones y contra filtraciones de Armenia y Azerbayán
Emails de Moviemento 5 Stelle
Lista consultiva de GhostSec de sitios extremistas y contenido marcado en Internet Archive
Bases de datos de Lizard Squad
Filtraciones de LulzSec en Canadá y Peru
Filtraciones de mSpy hack-Parastoo
Filtraciones de RedHat
Lanzamientos de Team GhostShell
Lanzamientos de Telecomix
Lanzamientos de Seventh Day Adventist Church
Filtraciones de Syrian Electronic Army
Filtraciones de la Oficina del Fiscal General de Ucrania
Archivos filtrados de HBO Winter-Leak.com
Filtraciones del Ejército Cibernético de Yemen
JOK3R, ONE TOOL TO DO ALL HACKING.

In most of the cases pentesting is done manually. Where pentester uses all the tools available over the internet to find bugs or vulnerabilities in web applications. Nowdays most often pentesting is done on automated tools. These tools are getting so much attention as these tools save lot of time. Pentester can do another challenging tasks in pentesting work. Today we are talking about jok3R.
Ethical hacking researcher of international institute of cyber security says that jok3r comes handy in initial phase of pentesting.
Jok3r is an popular pentesting framework which is build using many popular tools used in pentesting. This tool main goal is to save time on analyzing of the target. So the pentester can enjoy most of the time in another challenging part. This tool has been tested on Kali Linux 2017.3
ON TARGET WE WILL USE DVWA:-
- On Attacker side we are using DVWA to test the tool. For downloading DVWA iso go to : https://www.vulnhub.com/entry/damn-vulnerable-web-application-dvwa-107,43/
- After downloading iso, open iso in virtual box or vmware workstation. Then start iso.
- For getting DVWA ip type ifconfig
ON ATTACKER WE WILL DO JOK3R INSTALLATION :-
- For cloning type git clone https://github.com/koutto/jok3r.git
- Then type cd jok3r
- Type pip install -r requirements.txt
- install-all.sh and install-dependencies.sh permission needs to be change. For that type chmod u+x install-dependencies.sh and then type chmod u+x install-all.sh
- For checking if the permission has changed type ls -ltr
root@kali:/home/iicybersecurity/Downloads/jok3r# ls -ltr total 176 -rw-r--r-- 1 root root 35149 Jan 24 00:02 LICENSE -rw-r--r-- 1 root root 348 Jan 24 00:02 Dockerfile -rw-r--r-- 1 root root 461 Jan 24 00:02 CHANGELOG.rst -rw-r--r-- 1 root root 2519 Jan 24 00:02 TODO.rst -rw-r--r-- 1 root root 41498 Jan 24 00:02 README.rst -rw-r--r-- 1 root root 1934 Jan 24 00:02 jok3r.py -rwxr-xr-x 1 root root 3126 Jan 24 00:02 install-dependencies.sh -rwxr-xr-x 1 root root 129 Jan 24 00:02 install-all.sh drwxr-xr-x 2 root root 4096 Jan 24 00:02 docker drwxr-xr-x 3 root root 4096 Jan 24 00:02 doc -rw-r--r-- 1 root root 249 Jan 24 00:02 requirements.txt drwxr-xr-x 2 root root 4096 Jan 24 00:02 pictures drwxr-xr-x 3 root root 4096 Jan 24 00:02 webshells drwxr-xr-x 5 root root 4096 Jan 24 00:02 wordlists drwxr-xr-x 10 root root 4096 Jan 24 00:24 lib drwxr-xr-x 2 root root 4096 Jan 24 00:25 settings -rw-r--r-- 1 root root 32768 Jan 24 00:25 local.db drwxr-xr-x 5 root root 4096 Jan 24 00:25 toolbox
- Now type ./install-all.sh
- Type ./install-dependencies.sh
- This tool might take time to install dependencies as its an big tool some of the files takes time to download.
- If install-all.sh and install-dependencies.sh are not working properly or showing error while installing dependencies. Consider using docker to install all the dependencies.
- While installation it shows to upgrade pip for that type sudo apt-get install python3-pip. Then type pip –upgrade install pip
- If docker is not installed type sudo apt-get update Then type sudo apt-get install docker-ce or type sudo apt-get docker.io
- Type docker–version
root@kali:/home/iicybersecurity/Downloads/jok3r# docker --version Docker version 18.06.1-ce, build e68fc7a
- After installing docker type cd docker
- Type sudo docker pull koutto/jok3r This command will install all the dependencies/ tools that are needed by jok3r.
- Once the jok3r tools are installed type python3 jok3r.py –help
ATTACKER :-
vroot@kali:/home/iicybersecurity/Downloads/jok3r# python3 jok3r.py --help
____. __ ________ `Combine the best of...
| | ____ | | __\_____ \______ ...open-source Hacking Tools`
| |/ _ \| |/ / _(__ <_ __ \
/\__| ( (_) ) < / \ | \/
\________|\____/|__|_ \/______ /__| v2.0
\/ \/
~ Network & Web Pentest Framework ~[ Manage Toolbox | Automate Attacks | Chain Hacking Tools ]
usage:
python3 jok3r.py []
Supported commands:
toolbox Manage the toolbox
info View supported services/options/checks
db Define missions scopes, keep tracks of targets & view attacks results
attack Run checks against targets
optional arguments:
-h, --help show this help message and exit
- Type python3 jok3r.py toolbox –show-all
- toolbox is the list tools that have installed.
- –show-all will display all installed tools.
root@kali:/home/iicybersecurity/Downloads/jok3r# python3 jok3r.py toolbox --show-all
____. __ ________ `Combine the best of...
| | ____ | | __\_____ \______ ...open-source Hacking Tools`
| |/ _ \| |/ / _(__ <_ __ \
/\__| ( (_) ) < / \ | \/
\________|\____/|__|_ \/______ /__| v2.0
\/ \/
~ Network & Web Pentest Framework ~[ Manage Toolbox | Automate Attacks | Chain Hacking Tools ] Toolbox content - all services +--------------------------------+----------+-----------------+-------------------------------------------------------------------------------------------------------------+ | Name | Service | Status/Update | Description | +--------------------------------+----------+-----------------+-------------------------------------------------------------------------------------------------------------+ | ajpy | ajp | OK | 2019-01-24 | AJP requests crafter in order to communicate with AJP connectors | | ftpmap | ftp | OK | 2019-01-24 | FTP Scanner detecting vulns based on softs/versions | | halberd | http | OK | 2019-01-24 | HTTP load balancer detector | | wafw00f | http | OK | 2019-01-24 | Identify and fingerprint WAF products protecting a website | | whatweb | http | OK | 2019-01-24 | Identify CMS, blogging platforms, JS libraries, Web servers | | optionsbleed | http | OK | 2019-01-24 | Test for the Optionsbleed bug in Apache httpd (CVE-2017-9798) | | clusterd | http | OK | 2019-01-24 | Application server attack toolkit (JBoss, ColdFusion, Weblogic, Tomcat, Railo, Axis2, Glassfish) | | wig | http | OK | 2019-01-24 | Identify several CMS and other administrative applications | | fingerprinter | http | OK | 2019-01-24 | CMS/LMS/Library versions fingerprinter | | cmsexplorer | http | OK | 2019-01-24 | Find plugins and themes installed in a CMS (WordPress, Drupal, Joomla, Mambo) | | nikto | http | OK | 2019-01-24 | Web server scanner | | iis-shortname-scanner | http | OK | 2019-01-24 | Scanner for IIS short filename (8.3) disclosure vulnerability | | davscan | http | OK | 2019-01-24 | Fingerprint servers, finds exploits, scans WebDAV | | shocker | http | OK | 2019-01-24 | Detect and exploit web servers vulnerable to Shellshock (CVE-2014-6271) | | loubia | http | OK | 2019-01-24 | Exploitation tool for Java deserialize on t3(s) (Weblogic) | | exploit-tomcat-cve2017-12617 | http | OK | 2019-01-24 | Exploit for Apache Tomcat (<9.0.1 (Beta), <8.5.23, <8.0.47, <7.0.8) JSP Upload Bypass RCE (CVE-2017-12617) | | exploit-weblogic-cve2017-3248 | http | OK | 2019-01-24 | Exploit for Weblogic RMI Registry UnicastRef Object Java Deserialization RCE (CVE-2017-3248) | | exploit-weblogic-cve2017-10271 | http | OK | 2019-01-24 | Exploit for Weblogic WLS-WSAT RCE (CVE-2017-10271) | | exploit-weblogic-cve2018-2893 | http | OK | 2019-01-24 | Exploit for Weblogic Java Deserialization RCE (CVE-2018-2893) | | struts-pwn-cve2017-9805 | http | OK | 2019-01-24 | Exploit for Apache Struts2 REST Plugin XStream RCE (CVE-2017-9805) | | struts-pwn-cve2018-11776 | http | OK | 2019-01-24 | Exploit for Apache Struts2 CVE-2018-11776 | | domiowned | http | OK | 2019-01-24 | Fingerprint/Exploit IBM/Lotus Domino servers | | cmsmap | http | OK | 2019-01-24 | Vulnerability scanner for CMS WordPress, Drupal, Joomla | | cmseek | http | OK | 2019-01-24 | Detect and bruteforce CMS | | drupwn | http | OK | 2019-01-24 | Fingerprint Drupal 7/8 and exploit CVE | | dirhunt | http | OK | 2019-01-24 | Find web directories without bruteforce | | photon | http | OK | 2019-01-24 | Fast we crawler that extracts urls, emails, files, website accounts, etc. | | angularjs-csti-scanner | http | OK | 2019-01-24 | Angular Client-Side Template Injection scanner | | wpforce | http | OK | 2019-01-24 | WordPress attack suite | | wpscan | http | OK | 2019-01-24 | WordPress vulnerability scanner | | wpseku | http | OK | 2019-01-24 | WordPress vulnerability scanner | | joomscan | http | OK | 2019-01-24 | Joomla vulnerability scanner by OWASP | | joomlascan | http | OK | 2019-01-24 | Joomla vulnerability scanner | | joomlavs | http | OK | 2019-01-24 | Joomla vulnerability scanner | | droopescan | http | OK | 2019-01-24 | Drupal & Silverstripe plugin-based vulnerability scanner | | magescan | http | OK | 2019-01-24 | Magento CMS scanner for information and misconfigurations | | vbscan | http | OK | 2019-01-24 | vBulletin vulnerability scanner by OWASP | | liferayscan | http | OK | 2019-01-24 | Liferay vulnerability scanner | | xbruteforcer | http | OK | 2019-01-24 | CMS bruteforce tool | | dirsearch | http | OK | 2019-01-24 | Web path scanner | | wfuzz | http | OK | 2019-01-24 | Web application fuzzer | | barmie | java-rmi | OK | 2019-01-24 | Java RMI enumeration and attack tool | | jmxbf | java-rmi | OK | 2019-01-24 | Bruteforce program to test weak accounts configured to access a JMX Registry | | jmxploit | java-rmi | OK | 2019-01-24 | JMX (post-)exploitation tool in Tomcat environment | | sjet | java-rmi | OK | 2019-01-24 | JMX exploitation tool for insecure configured JMX services | | twiddle | java-rmi | OK | 2019-01-24 | CLI-based JMX client | | jdwp-shellifier | jdwp | OK | 2019-01-24 | Exploitation tool to gain RCE on JDWP | | msdat | mssql | OK | 2019-01-24 | Microsoft SQL Database Attacking Tool | | changeme | multi | OK | 2019-01-24 | Default credentials scanner | | impacket | multi | OK | 2019-01-24 | Collection of Python classes for working with network protocols | | jexboss | multi | OK | 2019-01-24 | Exploitation tool for JBoss, Jenkins, Struts2, JMX (Tomcat) | | jok3r-scripts | multi | OK | 2019-01-24 | Various small stand-alone scripts and dependencies for other tools | | metasploit | multi | OK | 2019-01-24 | Metasploit framework | | nmap | multi | OK | 2019-01-24 | Nmap port scanner | | patator | multi | OK | 2019-01-24 | Multi-purpose brute-forcer, with a modular design and a flexible usage | | testssl | multi | OK | 2019-01-24 | TLS/SSL encryption checker | | tls-prober | multi | OK | 2019-01-24 | Tool to fingerprint SSL/TLS servers | | vuln-databases | multi | OK | 2019-01-24 | Vulnerabilities databases from Vulners.com, vuldb.com (NSE scripts) and exploit-db.com | | ysoserial | multi | OK | 2019-01-24 | Tool for generating payloads that exploit unsafe Java object deserialization | | odat | oracle | OK | 2019-01-24 | Oracle database attacking tool | | nullinux | smb | OK | 2019-01-24 | Enumeration tool for SMB on Windows | | smbmap | smb | OK | 2019-01-24 | SMB Shares enumeration tool | | smtp-user-enum | smtp | OK | 2019-01-24 | Enumerate valid users on SMTP via EXPN, VRFY or RCPT TO | | snmpwn | snmp | OK | 2019-01-24 | SNMPv3 User enumerator and Attack tool | | snmp-check | snmp | OK | 2019-01-24 | SNMP enumerator | | ssh-audit | ssh | OK | 2019-01-24 | SSH server auditing tool (banner, key exchange, encryption, mac, compression, compatibility, security, etc) | | osueta | ssh | OK | 2019-01-24 | Exploit for OpenSSH (versions <= 7.2 and >= 5.*) user enumeration timing attack | | libssh-scanner | ssh | OK | 2019-01-24 | Exploit for authentication bypass (CVE-2018-10933) in libssh 0.6+ (fixed in 0.7.6 and 0.8.4) | +--------------------------------+----------+-----------------+-------------------------------------------------------------------------------------------------------------+
- This tool gives an options where you can save all the scanned services on the target. You can also see which service has been run on the target.
- For saving first you have to create database. For that type python3 jok3r.py db
- db will open jok3r database.
- For opening further options in db. Type help
root@kali:/home/iicybersecurity/Downloads/jok3r# python3 jok3r.py db
____. __ ________ `Combine the best of...
| | ____ | | __\_____ \______ ...open-source Hacking Tools`
| |/ _ \| |/ / _(__ <_ __ \
/\__| ( (_) ) < / \ | \/
\________|\____/|__|_ \/______ /__| v2.0
\/ \/
~ Network & Web Pentest Framework ~[ Manage Toolbox | Automate Attacks | Chain Hacking Tools ] The local database stores the missions, targets info & attacks results. This shell allows for easy access to this database. New missions can be added and scopes can be defined by importing new targets. ok3rdb[default]> help Documented commands (type help ): Attacks results results Attacks results Import nmap Import Nmap results Missions data creds Credentials in the current mission scope hosts Hosts in the current mission scope mission Manage missions services Services in the current mission scope Other alias Manage aliases help Display this help message history View, run, edit, save, or clear previously entered commands macro Manage macros quit Exit this application set Set a settable parameter or show current settings of parameters shell Execute a command as if at the OS prompt
- Then type mission testproject
- After creating mission. press ctrl + c
- Then type python3 jok3r.py attack -t http://192.168.1.105/ –add testproject
- attack is used to check the target.
- -t is used to enter target.
- –add is used to save the results in jok3r db.
root@kali:/home/iicybersecurity/Downloads/jok3r# python3 jok3r.py attack -t http://192.168.1.105/ --add testproject
____. __ ________ `Combine the best of...
| | ____ | | __\_____ \______ ...open-source Hacking Tools`
| |/ _ \| |/ / _(__ <_ __ \
/\__| ( (_) ) < / \ | \/
\________|\____/|__|_ \/______ /__| v2.0
\/ \/
~ Network & Web Pentest Framework ~[ Manage Toolbox | Automate Attacks | Chain Hacking Tools ]
[] URL given as target, targeted service is HTTP [] Check if target is reachable and grab banner using Nmap…
[+] Target URL http://192.168.1.105/ is reachable
[] Results from this attack will be saved under mission "testproject" in database [] A matching service has been found in the database
[+] Updated: host 192.168.1.105 | port 80/tcp | service http
+----+---------------+----------+------+-------+---------+-------------------------------------------------------------------+-----------------------+
| id | IP | Hostname | Port | Proto | Service | Banner | URL |
+----+---------------+----------+------+-------+---------+-------------------------------------------------------------------+-----------------------+
| >1 | 192.168.1.105 | dvwa | 80 | tcp | http | product: Apache httpd version: 2.2.14 extrainfo: (Unix) DAV/2 | http://192.168.1.105/ |
| | | | | | | mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 | |
| | | | | | | mod_perl/2.0.4 Perl/v5.10.1 | |
+----+---------------+----------+------+-------+---------+-------------------------------------------------------------------+-----------------------+
[?] Start attack ? [Y/n] Y
[*] HTTP Response headers:
Date: Thu, 24 Jan 2019 09:55:41 GMT
Server: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1
X-Powered-By: PHP/5.3.1
Set-Cookie: PHPSESSID=c03n54d2gciu1rh9niscqmij67; path=/
Set-Cookie: security=high
Expires: Tue, 23 Jun 2009 12:00:00 GMT
Cache-Control: no-cache, must-revalidate
Pragma: no-cache
Content-Length: 1224
Content-Type: text/html;charset=utf-8
[] Context-specific options set for this target: +----------+-------+ | option | value | +----------+-------+ | language | php | +----------+-------+ [] [SMART] Running initialization method…
{'Perl', 'Apache'}
[] [SMART] Wappalyzer fingerprinting returns: ['apache', 'mod_ssl', 'mod_perl', 'unix', 'php', 'perl', 'openssl'] [] [SMART] Detected option (no update): language = php
- After executing the above query jok3r has started the nmap scan on all services. This tool will scan all the services.
- The above service has detected the language and the server of the target website.
- The above information can be used in other hacking activities.
- For scanning all services simply type Y whenever it prompt to scan another service. Do specific while scanning
[>] [Recon][Check 13/14] crawling-fast > Crawl website quickly, analyze interesting files/directories
[?] Run command #01 ? [Y/n/t/w/q] Y
cmd> dirhunt http://192.168.1.105/
Welcome to Dirhunt v0.6.0 using Python 2.7.15+
Starting…
[302] http://192.168.1.105/ (Redirect)
Redirect to: http://192.168.1.105/
[200] http://192.168.1.105/login.php (HTML document)
Index file found: index.php
[200] http://192.168.1.105/dvwa/css/ (Index Of) (Nothing interesting)
[200] http://192.168.1.105/dvwa/ (Index Of) (Nothing interesting)
[200] http://192.168.1.105/dvwa/images/ (Index Of) (Nothing interesting)
[200] http://192.168.1.105/dvwa/js/ (Index Of) (Nothing interesting)
[200] http://192.168.1.105/dvwa/includes/ (Index Of)
Interesting extension files: dvwaPage.inc.php (13K), dvwaPhpIds.inc.php (2.5K)
[200] http://192.168.1.105/dvwa/includes/DBMS/ (Index Of)
Interesting extension files: DBMS.php (2.4K), MySQL.php (2.9K), PGSQL.php (3.4K)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━
Starting…
http://192.168.1.105/login.php
(200) ( 154B) http://192.168.1.105/dvwa/includes/dvwaPage.inc.php [13K ]
Warning: define() expects at least 2 parameters,
(200) ( 156B) http://192.168.1.105/dvwa/includes/dvwaPhpIds.inc.php [2.5K]
Warning: define() expects at least 2 parameters,
(200) ( 154B) http://192.168.1.105/dvwa/includes/DBMS/MySQL.php [2.9K]
Fatal error: Call to undefined function dvwaMessa
(200) ( 626B) http://192.168.1.105/dvwa/includes/DBMS/DBMS.php [2.4K]
Notice: Undefined variable: DBMS in /opt/lampp (200) ( 154B) http://192.168.1.105/dvwa/includes/DBMS/PGSQL.php [3.4K]
Fatal error: Call to undefined function dvwaMessa
[>] [Recon][Check 14/14] crawling-fast2 > Crawl website and extract URLs, files, intel & endpoints
- The above service used is crawl where this tool tries to analyze files and directories which can be used in further hacking attacks.
- While crawling some of the pages shows the dvwa directory named as includes has pages like mysql.php, dbms.php, pgsql which can be used in other hacking activities.
- Scanning further shows vulnerabilities mentioned in CVE.
[>] [Vulnscan][Check 01/29] vuln-lookup > Vulnerability lookup in Vulners.com (NSE scripts) and exploit-db.com (lots of false positive !) [?] Run command #01 ? [Y/n/t/w/q] Y cmd> sudo nmap -sT -sV -T5 -Pn -p 80 --script nmap-vulners/vulners.nse --script-args vulscandb=scipvuldb.csv 192.168.1.105 -oX /tmp/nmaptmp.xml; ./exploit-database/searchsploit --nmap /tmp/nmaptmp.xml; sudo rm -f /tmp/nmaptmp.xml Starting Nmap 7.70 ( https://nmap.org ) at 2019-01-24 06:02 EST Nmap scan report for dvwa (192.168.1.105) Host is up (0.00046s latency). PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.2.14 ((Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1) |http-server-header: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 | vulners: | cpe:/a:apache:http_server:2.2.14: | CVE-2010-0425 10.0 https://vulners.com/cve/CVE-2010-0425 | CVE-2011-3192 7.8 https://vulners.com/cve/CVE-2011-3192 | CVE-2013-2249 7.5 https://vulners.com/cve/CVE-2013-2249 | CVE-2017-7679 7.5 https://vulners.com/cve/CVE-2017-7679 | CVE-2017-7668 7.5 https://vulners.com/cve/CVE-2017-7668 | CVE-2017-3167 7.5 https://vulners.com/cve/CVE-2017-3167 | CVE-2017-3169 7.5 https://vulners.com/cve/CVE-2017-3169 | CVE-2012-0883 6.9 https://vulners.com/cve/CVE-2012-0883 | CVE-2009-3555 5.8 https://vulners.com/cve/CVE-2009-3555 | CVE-2013-1862 5.1 https://vulners.com/cve/CVE-2013-1862 | CVE-2014-0098 5.0 https://vulners.com/cve/CVE-2014-0098 | CVE-2007-6750 5.0 https://vulners.com/cve/CVE-2007-6750 | CVE-2013-6438 5.0 https://vulners.com/cve/CVE-2013-6438 | CVE-2011-3368 5.0 https://vulners.com/cve/CVE-2011-3368 | CVE-2012-4557 5.0 https://vulners.com/cve/CVE-2012-4557 | CVE-2014-0231 5.0 https://vulners.com/cve/CVE-2014-0231 | CVE-2010-0408 5.0 https://vulners.com/cve/CVE-2010-0408 | CVE-2010-1452 5.0 https://vulners.com/cve/CVE-2010-1452 | CVE-2010-2068 5.0 https://vulners.com/cve/CVE-2010-2068 | CVE-2012-0031 4.6 https://vulners.com/cve/CVE-2012-0031 | CVE-2011-3607 4.4 https://vulners.com/cve/CVE-2011-3607 | CVE-2012-0053 4.3 https://vulners.com/cve/CVE-2012-0053 | CVE-2011-3348 4.3 https://vulners.com/cve/CVE-2011-3348 | CVE-2016-4975 4.3 https://vulners.com/cve/CVE-2016-4975 | CVE-2010-0434 4.3 https://vulners.com/cve/CVE-2010-0434 | CVE-2011-4317 4.3 https://vulners.com/cve/CVE-2011-4317 | CVE-2013-1896 4.3 https://vulners.com/cve/CVE-2013-1896 | CVE-2011-0419 4.3 https://vulners.com/cve/CVE-2011-0419 | CVE-2012-4558 4.3 https://vulners.com/cve/CVE-2012-4558 | CVE-2012-3499 4.3 https://vulners.com/cve/CVE-2012-3499 | CVE-2011-3639 4.3 https://vulners.com/cve/CVE-2011-3639 | CVE-2016-8612 3.3 https://vulners.com/cve/CVE-2016-8612 | CVE-2012-2687 2.6 https://vulners.com/cve/CVE-2012-2687 | CVE-2011-4415 1.2 https://vulners.com/cve/CVE-2011-4415 Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 7.72 seconds [i] SearchSploit's XML mode (without verbose enabled). To enable: searchsploit -v --xml… [i] Reading: '/tmp/nmaptmp.xml' [i] ./exploit-database/searchsploit -t apache httpd 2 2 14
- After executing above query shows the cve vulnerabilities which can be used in further hacking attacks.
- It show many vulnerabilities in which are listed CVE recent years.
- Further scanning it uses nikto to scan for web vulnerabilities.
[>] [Vulnscan][Check 03/29] vulnscan-multi-nikto > Check for multiple web vulnerabilities/misconfigurations [?] Run command #01 ? [Y/n/t/w/q] Y cmd> cd program; perl ./nikto.pl -host dvwa -port 80 - Nikto v2.1.6 Target IP: 192.168.1.105 Target Hostname: dvwa Target Port: 80 + Start Time: 2019-01-24 06:14:56 (GMT-5) Server: Apache/2.2.14 (Unix) DAV/2 mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 Retrieved x-powered-by header: PHP/5.3.1 The anti-clickjacking X-Frame-Options header is not present. The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type Cookie PHPSESSID created without the httponly flag Cookie security created without the httponly flag Root page / redirects to: login.php Server leaks inodes via ETags, header found with file /robots.txt, inode: 9210, size: 26, mtime: Tue Aug 24 15:45:32 2010 Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var, HTTP_NOT_FOUND.html.var Perl/v5.10.1 appears to be outdated (current is at least v5.14.2) mod_ssl/2.2.14 appears to be outdated (current is at least 2.8.31) (may depend on server version) Apache/2.2.14 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current. PHP/5.3.1 appears to be outdated (current is at least 5.6.9). PHP 5.5.25 and 5.4.41 are also current. mod_perl/2.0.4 appears to be outdated (current is at least 2.0.7) OpenSSL/0.9.8l appears to be outdated (current is at least 1.0.1j). OpenSSL 1.0.0o and 0.9.8zc are also current. mod_ssl/2.2.14 OpenSSL/0.9.8l PHP/5.3.1 mod_apreq2-20090110/2.7.1 mod_perl/2.0.4 Perl/v5.10.1 - mod_ssl 2.8.7 and lower are vulnerable to a remote buffer overflow which may allow a remote shell. http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2002-0082, OSVDB-756. OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST OSVDB-112004: /cgi-bin/printenv: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271). OSVDB-112004: /cgi-bin/printenv: Site appears vulnerable to the 'shellshock' vulnerability (http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6278). OSVDB-3268: /config/: Directory indexing found. /config/: Configuration information may be available remotely. OSVDB-12184: /?=PHPB8B5F2A0-3C92-11d3-A3A9-4C7B08C10000: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. OSVDB-12184: /?=PHPE9568F36-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. OSVDB-12184: /?=PHPE9568F34-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. OSVDB-12184: /?=PHPE9568F35-D428-11d2-A769-00AA001ACF42: PHP reveals potentially sensitive information via certain HTTP requests that contain specific QUERY strings. OSVDB-561: /server-status: This reveals Apache information. Comment out appropriate line in the Apache conf file or restrict access to allowed sources. OSVDB-3092: /phpmyadmin/changelog.php: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts. OSVDB-3092: /phpmyadmin/ChangeLog: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts. OSVDB-3233: /cgi-bin/printenv: Apache 2.0 default script is executable and gives server environment variables. All default scripts should be removed. It may also allow XSS types of attacks. http://www.securityfocus.com/bid/4431. OSVDB-3233: /cgi-bin/test-cgi: Apache 2.0 default script is executable and reveals system information. All default scripts should be removed. OSVDB-3268: /icons/: Directory indexing found. OSVDB-3268: /docs/: Directory indexing found. OSVDB-3092: /CHANGELOG.txt: A changelog was found. OSVDB-3233: /icons/README: Apache default file found. /login.php: Admin login page/section found. /phpmyadmin/: phpMyAdmin directory found OSVDB-3092: /.svn/entries: Subversion Entries file may contain directory listing information. OSVDB-3092: /phpmyadmin/Documentation.html: phpMyAdmin is for managing MySQL databases, and should be protected or limited to authorized hosts. /CHANGELOG.txt: Version number implies that there is a SQL Injection in Drupal 7, can be used for authentication bypass (Drupageddon: see https://www.sektioneins.de/advisories/advisory-012014-drupal-pre-auth-sql-injection-vulnerability.html). /server-status: Apache server-status interface found (pass protected) 8167 requests: 0 error(s) and 39 item(s) reported on remote host + End Time: 2019-01-24 06:15:35 (GMT-5) (39 seconds) 1 host(s) tested
- The above tool shows that many of the configuration is not done properly thats why bruteforce attacks can be done easily.
- Some of the versions of the apache, perl are outdated. There are certain HTTP request which can generate sensitive information.
- This information can be used in other hacking activities.
- It also run tool like changme.
cmd> python3 changeme.py -v --protocols http 192.168.1.105:80
#####################################################
_
| |_ _ _ _ _ _ _ _ _ _
/ _| ' \ / | '_ \ / _ |/ \ '_ ` _ \ / _ \
| (| | | | (| | | | | (| | / | | | | | __/
___|| ||__,|| ||_, |___|| || ||__|
|_/
v1.1
Default Credential Scanner by @ztgrace
#####################################################
Loaded 113 default credential profiles
Loaded 324 default credentials
[06:28:15] Configured protocols: http
[06:28:15] Loading creds into queue
[06:28:15] Fingerprinting completed
[06:28:15] Scanning Completed
No default credentials found
[*] [SMART] Running post-check method "changeme_valid_creds" …
[*] [Vulnscan][Check 05/29] webdav-scan-davscan > Skipped because target's context is not matching
[*] [Vulnscan][Check 06/29] webdav-scan-msf > Skipped because target's context is not matching
[*] [Vulnscan][Check 07/29] webdav-internal-ip-disclosure > Skipped because target's context is not matching
[*] [Vulnscan][Check 08/29] webdav-website-content > Skipped because target's context is not matching
- After scanning target further it shows target context is not matching because this tool detects default backdoor credentials.
- Now scanning with another tool shell shocker which shows if target is vulnerable to exploit.
[>] [Vulnscan][Check 11/29] shellshock-scan > Detect if web server is vulnerable to Shellshock (CVE-2014-6271)
[?] Run command #01 ? [Y/n/t/w/q] Y
cmd> python2.7 shocker.py --Host 192.168.1.105 --port 80
.-. . .
( )| |
-. |--. .-. .-.|.-. .-. .--. ( )| |( )( |-.'(.-' | -' ' --' -''-`--'' v1.1
Tom Watson, tom.watson@nccgroup.trust
https://www.github.com/nccgroup/shocker
Released under the GNU Affero General Public License
(https://www.gnu.org/licenses/agpl-3.0.html)
[+] 402 potential targets imported from ./shocker-cgi_list
[+] Checking connectivity with target…
[+] Target was reachable
[+] Looking for vulnerabilities on 192.168.1.105:80
>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>>
[+] 3 potential targets found, attempting exploits
[+] The following URLs appear to be exploitable:
[1] http://192.168.1.105:80/cgi-bin/printenv
[2] http://192.168.1.105:80/cgi-bin/test-cgi
- The tool shell shocker shows that the target can be exploited using above 2 links. This information can be used in other hacking activities.
- Some times if the tool gots hanged while running press ctrl+c to start further scanning.
- Scanning further shows some of the tools are not supported as shown below.
Category > Exploit [*] [Exploit][Check 01/11] jboss-deploy-shell > Skipped because target's context is not matching [*] [Exploit][Check 02/11] struts2-rce-cve2017-5638 > Skipped because target's context is not matching [*] [Exploit][Check 03/11] struts2-rce-cve2017-9805 > Skipped because target's context is not matching [*] [Exploit][Check 04/11] struts2-rce-cve2018-11776 > Skipped because target's context is not matching [*] [Exploit][Check 05/11] tomcat-rce-cve2017-12617 > Skipped because target's context is not matching [*] [Exploit][Check 06/11] jenkins-cliport-deserialize > Skipped because target's context is not matching [*] [Exploit][Check 07/11] weblogic-t3-deserialize-cve2015-4852 > Skipped because target's context is not matching [*] [Exploit][Check 08/11] weblogic-t3-deserialize-cve2017-3248 > Skipped because target's context is not matching [*] [Exploit][Check 09/11] weblogic-t3-deserialize-cve2018-2893 > Skipped because target's context is not matching [*] [Exploit][Check 10/11] weblogic-wls-wsat-cve2017-10271 > Skipped because target's context is not matching [*] [Exploit][Check 11/11] drupal-cve-exploit > Skipped because target's context is not matching
- The above tools are not supported as the tools are of different context and target has different functionalities.
- Using another tool wfuzz. Wfuzz is a bruteforcing web application.
cmd> ./wfuzz -c -u http://192.168.1.105//FUZZ -w /home/iicybersecurity/Downloads/jok3r/wordlists/services/http/discovery/opendoor-paths.txt --hc 400,404,500,000 Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information. Wfuzz 2.3.4 - The Web Fuzzer * Target: http://192.168.1.105//FUZZ Total requests: 36942 ================================================================== ID Response Lines Word Chars Payload 000431: C=200 101 L 135 W 1480 Ch ".svn/all-wcprops" 000432: C=200 572 L 151 W 2726 Ch ".svn/entries" 000434: C=200 12 L 61 W 803 Ch ".svn/prop-base/" 000435: C=200 11 L 52 W 667 Ch ".svn/props/" 000436: C=200 25 L 175 W 2455 Ch ".svn/text-base/" 000437: C=200 4 L 39 W 538 Ch ".svn/text-base/index.php.svn-base" 000438: C=200 14 L 76 W 1010 Ch ".svn/tmp/" 001959: C=200 129 L 594 W 5066 Ch "CHANGELOG.txt" 001973: C=200 622 L 5214 W 33107 Ch "COPYING.txt" 002936: C=200 119 L 706 W 4934 Ch "README.txt" 004298: C=302 0 L 0 W 0 Ch "about.php" 004948: C=404 46 L 113 W 1118 Ch "admin/FCKeditor/editor/filemanager/browser/default/connectors/jsp/connector005061: C=404 46 L 113 W 1118 Ch "admin/fckeditor/editor/filemanager/browser/default/connectors/asp/connector005062: C=404 46 L 113 W 1118 Ch "admin/fckeditor/editor/filemanager/browser/default/connectors/aspx/connecto005063: C=404 46 L 113 W 1118 Ch "admin/fckeditor/editor/filemanager/browser/default/connectors/php/connector006673: C=404 46 L 113 W 1118 Ch "all/modules/ogdi_field/plugins/dataTables/extras/TableTools/media/swf/ZeroC007150: C=404 46 L 113 W 1118 Ch "apps/trac/pragyan/browser/trunk/cms/modules/article/fckEditor/editor/filema010085: C=403 44 L 109 W 1122 Ch "cgi-bin/" 010087: C=403 44 L 108 W 1108 Ch "cgi-bin/awstats.pl" 011523: C=200 12 L 61 W 776 Ch "config/" 013659: C=200 11 L 52 W 650 Ch "docs/" 013930: C=404 46 L 113 W 1118 Ch "dreamedit/includes/FCKEditor_/editor/filemanager/browser/mcpuk/browser.html014071: C=200 15 L 84 W 1101 Ch "dvwa/" 015076: C=403 44 L 109 W 1122 Ch "error/" 015477: C=200 12 L 60 W 772 Ch "external/" 015653: C=200 1 L 6 W 1549 Ch "favicon.ico" 015697: C=404 46 L 113 W 1118 Ch "fckeditor/editor/filemanager/browser/default/connectors/aspx/connector.aspx016920: C=404 46 L 113 W 1118 Ch "galeria/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folder016925: C=404 46 L 113 W 1118 Ch "galerie/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folder016955: C=404 46 L 113 W 1118 Ch "gallery/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folder018593: C=200 167 L 1300 W 18876 Ch "icons/" 018642: C=302 0 L 0 W 0 Ch "ids_log.php" 019087: C=404 46 L 113 W 1118 Ch "includes/fckeditor/editor/filemanager/browser/default/connectors/asp/connec019088: C=404 46 L 113 W 1118 Ch "includes/fckeditor/editor/filemanager/browser/default/connectors/aspx/conne019089: C=404 46 L 113 W 1118 Ch "includes/fckeditor/editor/filemanager/browser/default/connectors/php/connec019142: C=302 0 L 0 W 0 Ch "index.php" 019762: C=404 46 L 113 W 1118 Ch "ispcp/browser/trunk/gui/tools/filemanager/plugins/fckeditor/editor/filemana020212: C=404 46 L 113 W 1118 Ch "js/fckeditor/editor/filemanager/browser/default/connectors/php/connector.ph021551: C=200 65 L 108 W 1224 Ch "login.php" 021667: C=302 0 L 0 W 0 Ch "logout.php" 025961: C=404 46 L 113 W 1118 Ch "photo/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folder.p026010: C=404 46 L 113 W 1118 Ch "photos/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folder.026053: C=200 4 L 20 W 148 Ch "php.ini" 026339: C=302 0 L 0 W 0 Ch "phpinfo.php" 026390: C=200 0 L 0 W 0 Ch "phpmyadmin/phpinfo.php" 026389: C=200 72 L 206 W 2726 Ch "phpmyadmin/" 026673: C=404 46 L 113 W 1118 Ch "plugins/fckeditor/fckeditor/editor/filemanager/browser/default/browser.html026675: C=404 46 L 113 W 1118 Ch "plugins/p_fckeditor/fckeditor/editor/filemanager/browser/default/browser.ht026676: C=404 46 L 113 W 1118 Ch "plugins/p_fckeditor/fckeditor/editor/filemanager/connectors/uploadtest.html028932: C=200 1 L 4 W 26 Ch "robots.txt" 029580: C=404 46 L 113 W 1118 Ch "script/jqueryplugins/dataTables/extras/TableTools/media/swf/ZeroClipboard.s029817: C=302 0 L 0 W 0 Ch "security.php" 029987: C=200 51 L 292 W 2787 Ch "server-status/" 029986: C=200 1253 L 8719 W 120232 Ch "server-info/" 030080: C=404 46 L 113 W 1118 Ch "servlet/Oracle.xml.xsql.XSQLServlet/soapdocs/webapps/soap/WEB-INF/config/so030101: C=404 46 L 113 W 1118 Ch "servlet/oracle.xml.xsql.XSQLServlet/soapdocs/webapps/soap/WEB-INF/config/so030182: C=200 80 L 227 W 3549 Ch "setup.php" 036787: C=404 46 L 113 W 1118 Ch "zenphoto/zp-core/plugins/tiny_mce/plugins/ajaxfilemanager/ajax_create_folde Total time: 110.2424 Processed Requests: 36942 Filtered Requests: 36874 Requests/sec.: 335.0979
- The above query tries to find directories, files which are not linked directly. After running above query wfuzz has found ajax, servlets and some plugins.
- This data can be used in other hacking attacks.
As you can see that this tool comprises many small tools which shows many vital information. For scanning further you can following other tutorials
CRITICAL VULNERABILITIES IN CISCO ROUTERS AFFECT THOUSANDS OF COMPANIES IN THE ENTIRE WORLD

The firm has already released update patches for several SMEs products
The Cisco technology firm recently launched update patches to address two critical vulnerabilities present in RV320 and RV325 routers, products widely used in small businesses. According to network security specialists, the first of these failures (CVE-2019-1653) could be exploited by remote attackers to access confidential information, while the second (CVE-2019-1652) is a command-injection flaw.
The real problem for Cisco is that some hackers have been attacking the RV320 and RV325 routers using new exploits. After public disclosure of the initial exploit concept test, hackers began searching for vulnerable devices on the Internet to try to compromise them.
Both vulnerabilities are found in the web management interface of the compromised routers, reported network security specialists from the International Institute of Cyber Security. By chaining the two flaws, a hacker can take control of these devices, attackers exploit vulnerabilities to obtain privileged passwords and execute arbitrary commands.
Specialists in a cybersecurity firm were responsible for reporting these flaws to Cisco, the code tests for exploitation were revealed to the public a few days after the company launched the update patches. Experts published the proof-of-concept for command-injection vulnerabilities, information disclosures, and data leakage.
When using Shodan to look for some of the compromised routers models, it is possible to find tens of thousands of these devices running online.
Troy Mursch, a network security specialist, performed his own scanning for vulnerable systems, discovering about 9.6k online exposed routers (6 247 Cisco RV320 routers and 3 410 Cisco RV325 routers).
Mursch described on a map the geographic distribution of the compromised routers, proving that most of these devices are found in the United States.
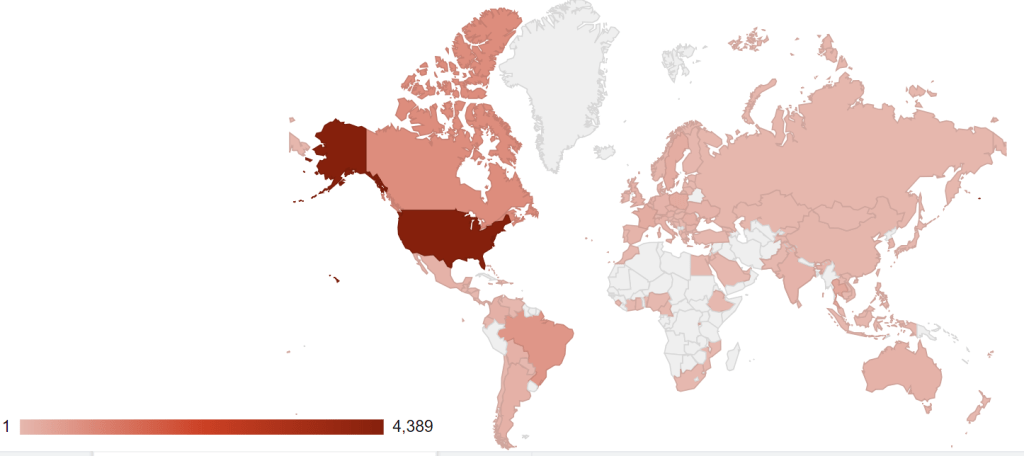
“Although the research we did will be published shortly, the IP addresses of the Cisco routers affected by these failures will not be revealed, as it is sensitive information,” said Troy Mursch on his blog.
JAPAN IS PLANNING MASSIVE HACKING OF CITIZENS’ IOT DEVICES

The Japanese government will try to protect IoT devices before the Tokyo 2020 Olympics to prevent cyberattacks
Last Friday the Japan Government approved an amendment that provides its public employees the ability to hack any citizen Internet of Things (IoT) devices; according to specialists in network security and ethical hacking from the International Institute of Cyber Security, this measure is part of an unusual and highly invasive research on vulnerable IoT devices.
This research will be carried out by employees of the Japan National Institute of Information and Communications Technology (NICT), with the supervision of the Ministry of Internal Affairs, the Japanese government reported.
The legislation states that NICT employees will be able to use default password dictionaries to try to access consumer IoT devices. This is intended to gather a list of unsafe IoT equipment (with predetermined or easy to guess passwords) so that the Government, in collaboration with major telecommunications companies, can make decisions and alert the owners of these devices to reinforce network security.
The research will begin in the next few days, focusing mainly on routers and webcams. The Japanese government expects to analyze around 200 million of IoT devices in households and organizations.
Reports of network security specialists claim that cyberattacks targeting IoT devices in Japan equals one-third of all the cyberattacks reported annually in the country, which could increase during the upcoming Tokyo 2020 Olympics, as the Japanese government knows that groups of hackers are always in the expectation of this kind of events to attack important IT infrastructures.
During the 2018 Winter Olympics in PyeongChang, South Korea, Russian government-sponsored hacker groups deployed the “Olympic Destroyer” malware against the South Korean computer infrastructure, all in retaliation for the decision of the International Olympic Committee (IOC) to expel hundreds of Russian athletes from the competition.
In addition, the same hackers built VPNFilter, a gigantic botnet, using domestic IoT equipment with which they planned to cut the transmission of the final of the UEFA Champions League of 2018 in Kiev, according to reports from the Ukrainian intelligence agencies.
As anticipated, the Japanese government’s decision has provoked indignation among citizens and privacy activists groups. The disgruntled ones argue that this is an unnecessary measure, as it is enough for the Japanese government to implement an awareness-raising campaign on the security of these devices.
On the other hand, the Japanese Government considers that this is a legitimate measure, because most of the IoT botnets are created by hackers thanks to the weak security within this kind of devices. Moreover, although a botnet can also be created by exploiting vulnerabilities in the routers, the most used way is to corrupt the devices without security measures.
POLICE DEPARTMENTS DECIDE TO ENCRYPT THEIR RADIO COMMUNICATIONS; PRESS AND CRIMINALS SEEM WORRIED

Local reporters will be in a weak position for their work due to this measure of the Colorado police
Network security and ethical hacking specialists from the International Institute of Cyber Security report that at least ten of the police agencies in Colorado, U.S. have decided to implement encryption in all their radio communications, as previously applied only to operations considered ‘sensitive’. Because of this new policy, journalists will no longer be able to use scanners or mobile applications to track police calls.
“Applying encryption to our communications will improve the security and effectiveness of police departments,” said Colorado state officials. “Not only were journalists using this kind of technology, also criminals and suspects took advantage of listening to our calls,” officials added.
However, network security experts consider that this mainly affects journalists, as it will be more difficult for them to go to the places where the facts relevant to their work are happening, reason to argue that the Police agencies are limiting transparency in their tasks.
Still, this is not something that privacy activists or some cybersecurity firm consider intrinsically wrong; communication encryption is, in fact, something desirable today. Encryption protects individuals and organizations sensitive information, such as financial data, online purchases or even identities, against malicious hackers, as considered by network security experts.
In addition, these days there are multiple data security incidents involving organizations of any size that lack the right protocols and information security measures, malicious actors of all kinds are always at the stalking of weaknesses that allow access to information belonging to millions of people.
People should really be aware about the importance of their information privacy, just as someone closes the doors of their house with key before leaving; online service users must protect their data with measures such as passwords or multi-factor authentication. Therefore, although this measure of the Colorado police may be controversial, it could also be beneficial to many.
DISTRIBUTED DENIAL O SECRETS: A NEW COMPETITOR FOR WIKILEAKS
The cyberactivism has a new anonymous face
According to Salvador Ruiz, network security specialist from the International Institute of Cyber Security, Distributed Denial of Secrets(DDOS) is a transparency collective whose main goal is to enable the free transmission of public interest data. DDOS aims to avoid any political, corporate or personal leanings, and simply act as a beacon of available information. As a collective, DDOS do not support any cause, idea or message beyond ensuring that information will be available to those who need it most – the people.
How to get: https://ddosecretspzwfy7.onion.to/
The grouo recently announced the release of a massive email leaking belonging to Russian oligarchs, journalists, religious leaders and politicians.
While DDOS team is happy to serve as an index to data of all varieties, mostly follow this two criteria:
- Is the data of public interest?
- Can a prima facie case be made for the veracity of the contents?
Unless already public, or as authorized by its source, DDOS do not disclose the providing party of any received information, and it’s fully committed to ensuring their anonymity from all threats. DDOS could never advise on the perfect procedure for transferring data to its platform anyone else, but it can act as a shield for that process and share advice from its experience. Often its role is to not just make data available, but to act as an anonymity guard to pass data to journalists and other figures best positioned to interrogate it.
The Collective
DDOS is a small group, but its reach expands far beyond just the members, not all of who are listed or ever acknowledged by their own preference. DDOS have informally worked together for many years and have developed deep connections in the field of data gathering, research, journalism, activism and technology. In 2018, DDOS members decided to put together their expertise and time to create a unified project representing their shared goals, and provide a platform for others to know and trust.
The modern state of “leaking” organizations has deteriorated rapidly for many years, poisoned by their own egos and interests. The DDOS view is that data is a resource and a record – this data can never tell the whole story. DDOS trusts the public to be responsible with data, and open it to them for the rigorous examination of it. In time, the truth can always emerge.
The Team
Emma Best – @NatSecGeek
Emma is an independent journalist who has spent more years filling out FOIA’s than most people have spent reading the news. Known for her tenacity in always finding the next lead and penetrating the bureaucratic walls of government, she has a keen eye for the details in every document and is a ruthless advocate for the truth even when all others dare not dig deeper.
“The Architect”
This is the pseudonym for DDOS’s technical behemoth that prefers to remain anonymous. He is no stranger to controversy and has been involved in privacy and technology activism for at least 10 years. The Architect is primarily responsible for advising on the operational security of the collective and maintains web and technical operations for the group.

WANTED
DDOS is always looking to expand its available data sets. They can consider almost any data, but they are actively seeking out the below information. If you can help them locate it, it would be greatly appreciated!
ACAPOR Leaked Emails (Torrent Hash: 4b92fe94ccb803d6c5b97abc4c7ebdf706290539)
Filipe Menezes Emails (Torrent Hash: 2866dc3538d12d99c88eb254591773d3821d939c)
Goldcorp (Torrent Hash: 0c385c2010e8a47e046ac8284f2f848c3ce5f8de)
Alleged emails from Ukraine’s Central Election Committee (Torrent Hash: 2df1c468641911537e3fbd22647c4bd14afebed7)
Anonymous Bulgaria/Greece/Spain releases
Armenia/Azerbaijan leaks and counterleaks
Five Star Movement (Moviemento 5 Stelle, M5S) emails
GhostSec advisory list of extremist sites and flagging content on Internet Archive
Lizard Squad database
LulzSec Canada/Peru releases
mSpy hack-Parastoo leaks
RedHat leaks
Team GhostShell releases
Telecomix releases
Seventh Day Adventist Church leak
Syrian Electronic Army leaks
Ukraine General Prosecutor’s Office leak
Winter-Leak.com leaked HBO files
Yemen Cyber Army Leaks
NUEVA CAMPAÑA DE MALVERTISING ATACA A USUARIOS DE DISPOSITIVOS APPLE

Un reconocido grupo de hackers está detrás de esta campaña maliciosa
Especialistas en seguridad en redes del Instituto Internacional de Seguridad Cibernética advierten sobre una nueva campaña de malvertisingcontra los usuarios de dispositivos Apple. Acorde al experto en ciberseguridad Eliya Stein, el grupo detrás de esta campaña, llamado VeryMal, ha desplegado diversas campañas desde mediados del año pasado, tratando de redirigir a los usuarios de Apple al dominio veryield-malyst.
El especialista calcula que hasta 5 millones de usuarios podrían haber sido expuestos durante la más reciente campaña maliciosa, en la que los atacantes recurrieron al uso de la esteganografía para que los sistemas de seguridad no pudieran detectar las cargas útiles.
“Entre más sofisticada se vuelve la detección de malvertising, los hackers también desarrollan mejores métodos para evadir los sistemas de seguridad y conseguir los objetivos de sus campañas maliciosas”, menciona Stein. “Técnicas como la esteganografía son útiles para la entrega de cargas útiles sin depender de cadenas codificadas o voluminosas tablas de búsqueda”.
En este caso, la campaña está diseñada para entregar un troyano conocido como Shlayer, un instalador de adware que recurre a “un proceso de instalación inusual”, para tratar de eludir la detección, reporta el experto en seguridad en redes.
Las campañas del grupo VeryMal concentran su mayor actividad en unos pocos días, esta vez, solo se mantuvo activa entre el 11 y el 13 de enero, concentrándose principalmente en infectar a los usuarios de iOS y macOS en Estados Unidos. Acorde al experto en seguridad en redes, con la esteganografía los actores maliciosos ocultan el malware Javascript dentro de un archivo multimedia, como una imagen, práctica que se ha vuelto muy popular recientemente.
La industria del marketing podría ser afectada al igual que Apple; según cálculos sobre el impacto de este incidente, la campaña de malvertising generó pérdidas por alrededor de 1.2 millones de dólares cada día que se mantuvo activa derivados de sesiones de usuario interrumpidas y bloqueo de futuros anuncios.
Los anunciantes incluso podrían ser acusados de fraude publicitario y encontrados responsables directos por los daños a los dispositivos infectados.
HACKERS ESTÁN USANDO ‘TUNNELING’ DE RED PARA ELUDIR EL FIREWALL EN LUGAR DE RDP

La técnica ‘network tunneling’ cada vez está siendo más utilizada para ataques que usan RDP
Remote Desktop Protocol (RDP) es un componente de Windows diseñado para proporcionar a los administradores y usuarios una vía de acceso remota a sus sistemas. Acorde a especialistas en seguridad en redes del Instituto Internacional de Seguridad Cibernética reportan que hackers maliciosos han estado abusando de esta característica para atacar los sistemas vulnerables, ya que en ocasiones esta clase de ataques pueden ser más difíciles de detectar que un backdoor.
“Los usuarios maliciosos recurren al uso del RDP debido a su estabilidad y funcionalidad por encima de un backdoor. Hemos detectado que los hackers usan las funciones nativas del Windows RDP para conectarse lateralmente a través de sistemas en entornos comprometidos”, comentan los especialistas.
Según los especialistas en seguridad en redes, el acceso a un sistema vía RDP permite a los atacantes ganar persistencia, aunque depende de un vector de ataque adicional para entrar en el sistema comprometido, como un ataque de phishing, por ejemplo. Además, los atacantes han recurrido cada vez más a la ‘tunelización de la red’ y al reenvío de puertos basado en el host.
Gracias a esto, los atacantes pueden establecer una conexión con un servidor remoto bloqueado por un firewall para explotar esa conexión y usarla como medio de transporte para ‘cavar un túnel’ hacia los servicios locales a través del firewall.
Una utilidad que se usa para canalizar sesiones RDP es PuTTY Link, o Plink, que permite a los atacantes establecer conexiones SSH a otros sistemas. Acorde a los expertos en seguridad en redes, dado que muchos entornos no inspeccionan los protocolos o no bloquean las comunicaciones SSH que salen de su red, los atacantes pueden usar la herramienta para crear túneles cifrados y establecer conexiones RDP con C&C.
Por otra parte, las sesiones RDP también permiten a los atacantes moverse lateralmente a través de un entorno; los atacantes pueden usar el comando nativo de Shell de red en Windows (netsh) para usar el reenvío de puertos RDP para descubrir redes segmentadas.
Los mecanismos de prevención y detección en host y en red deben proporcionar a las organizaciones las defensas necesarias para mitigar esta clase de ataques, afirman los expertos.
Asimismo, deshabilitar el RDP cuando no se use, habilitar las reglas del firewall en host para prohibir las conexiones RDP entrantes son consejos útiles para reforzar la prevención de riesgos.
Por otra parte, a nivel de red los administradores deben hacer cumplir las conexiones RDP desde un buzón designado o un servidor de administración central, evitar que se usen cuentas privilegiadas para RDP, revisar las reglas del firewall para identificar vulnerabilidades de reenvío de puertos e inspeccionar el contenido del tráfico de red.
