Month: October 2015
Oracle points patching firehose at 154 vulnerabilities
Of course there’s a Java fix, there always is Sysadmins forced by circumstance or folly to support Java can get busy again, with 25 fixes for the product among the Scarlet Letter’s regular patch notice.
The good news is that Oracle says none of the vulnerabilities in its mammoth bug-splat had been exploited as of 19 October.
The fixes to Java SE and Java SE Embedded cover vulnerabilities in the CORBA (Common Object Request Broker Architecture), Remote Method Invocation (Java RMI), Java FX, serialisation, 2D, Java API for XML Processing (JAXP), Java Generic Security Services (JGSS), security and deployment sub-components, as well as various library flaws.

Over at the Big O’s security blog, regular bearer-of-bad-news Eric Maurice lists “Oracle database, Oracle Fusion Middleware, Oracle Hyperion, Oracle Enterprise Manager, Oracle E-Business Suite, Oracle Supply Chain Products Suite, Oracle PeopleSoft Enterprise, Oracle Siebel CRM, Oracle Industry Applications, including Oracle Communications Applications and Oracle Retail Applications, Oracle Java SE, Oracle Sun Systems Products Suite, Oracle Pillar Axiom, Oracle Linux & Virtualization, and Oracle MySQL” as getting fixes.
Of the Java SE fixes, he writes, 20 apply only to Java in the browser, the remaining five apply to both client and server Java SE, and 24 are remotely exploitable without authentication. Hooray.
There are eight fixes for the Oracle database, one of which (CVE-2015-4863, not yet described on Mitre) has a base score of 10, because it’s remotely exploitable without authentication.
There’s also a perfect 10 in Oracle Sun Systems’ Integrated Lights Out Manager (ILOM), and Maurice says as well as patching ILOM, sysadmins should block outside access to the software.
‘All Android devices’ vulnerable to new LTE security flaw
A flaw in the implementation of a security feature on the mobile networks of U.S. providers AT&T and Verizon could put every connected Android device at risk of eavesdropping and identity spoofing, according to a recent report.
Devices on AT&T and Verizon networks are vulnerable to “loss of privacy, incorrect billing, and data spoofing.”
AT&T and Verizon’s implementations of LTE are said to be vulnerable to “to several issues” that could result in eavesdropping, data spoofing, and over-billing for potentially millions of phones.
Android devices on these networks are at most risk because the software “does not have appropriate permissions model” for LTE networks.

-Mobile customers were affected but the issue has since been “resolved,” a spokesperson said.
Apple products are not affected.
The advisory, posted by Carnegie Mellon University’s public vulnerability database (CERT) on Friday, was based on a paperpublished by Korean academics and security researchers, which call for a “comprehensive solution that eliminates the root causes at mobile devices, mobile platforms, and the core network.”
LTE (also known as 4G) relies on packet switching, a common way of sending data across the internet, rather than the old method of circuit switching. This new method of sending data allows for new kinds of attacks, particularly against the Session Initiation Protocol (SIP), nowadays more commonly used in voice calls and instant messaging.
Researchers have found a method that exploits the way that SIP works, by spoofing phone numbers for calls or text messages. It’s also possible for an attacker to obtain free bandwidth for more data-intensive activities, like video calling, without incurring any additional costs. In some cases, an attacker can establish multiple SIP sessions at the same time, which could lead to a denial-of-service attack on the network.
The advisory said each network was vulnerable to “one or more” of the issues. CERT, which published the advisory, said it was currently unaware of a practical fix to the issues.
T-Mobile and Verizon were both identified as being at-risk from the peer-to-peer attacks. The researchers had not conducted full testing on AT&T but said it was likely at risk.
The researchers warned create a peer-to-peer network within that cell carrier’s network, allowing an attacker to “directly retrieve data from other phones,” the advisory said.
In one example, a malicious Android app could quietly make phone calls without the user’s knowledge. That could be used to generate money on premium lines, over-billing, as well conducting targeted eavesdropping.
The researchers said every version of Android was at risk, whereas other attacks were network dependent.
When contacted, a Google spokesperson said the company will fix the issue for Nexus devices as part of its November Monthly Security Update, but did not confirm which Android versions were affected.
It’s also not clear when a patch will land for other affected Android devices, as these are carrier dependent.
An AT&T spokesperson did not immediately provide comment. An email to Verizon was not returned. We will update the piece if we hear back.
Source:http://www.zdnet.com/
Google, Facebook, Microsoft and buddies stick a bomb under hated CISA cyber-law
Some of the biggest names in the tech industry have issued a public protest against the proposed Cybersecurity Information Sharing Act (CISA) working through US Congress.
An open letter protesting the bill was sent by the Computer and Communications Industry Association (CCIA), an industry body whose members include Microsoft, Google, Facebook, Amazon, Nvidia, eBay, and Yahoo!
The CCIA says that the legislation, as written, will have dire consequences for the American IT industry. (And, we presume, great news for non-US tech companies.)
“CISA’s prescribed mechanism for sharing of cyber threat information does not sufficiently protect users’ privacy or appropriately limit the permissible uses of information shared with the government,” it reads. “In addition, the bill authorizes entities to employ network defense measures that might cause collateral harm to the systems of innocent third parties.”
CISA would allow the government and companies to share people’s private information that federal investigators can analyze and look at for linkages to crime and terrorism. In return for sharing data, the companies receive indemnity against lawsuits for privacy and antitrust laws from customers.
Although lawsuits might be difficult. The bill’s language specifically excludes the government from having to reveal what information it is harvesting to freedom-of-information requests, so you’ll never know if your browsing habits or online messages are being viewed by government investigators.
The bill is a rewritten version of CISPA, which you may remember from protests in 2013 that saw over 400 websites go dark. That killed the bill, but a year later it was back, minus a digit, in a slightly amended form.
“While appropriately constructed cybersecurity information sharing legislation can provide a more efficient regime for the voluntary sharing of appropriately limited information between the private sector and government, it is not the only means through which information sharing can occur,” the CCIA letter notes.
“Current legal authorities permit companies to share cyber threat indicators with the government where necessary to protect their rights and the rights of their users, and should not be discounted as useful existing mechanisms.”
Supporters of the bill say that privacy safeguards exist and that users’ personal information can be protected. But the bill has raised the hackles of many in the technology space, and even some government agencies.
Rather bizarrely, the Department of Homeland Security came out against the bill in August. The DHS is concerned that all this internet data is going to federal agencies directly, rather than funneling it through a central database run by, for example, the Department of Homeland Security.
The CCIA’s opposition will be a welcome fillip to opponents of the bill, and comes as Congress iscurrently considering the new legislation. In the Senate, CISA has already galvanized politicians to oppose the legislation, led by Senator Ron Wyden (D-OR) and presidential candidates Bernie Sanders (I-VT) and Rand Paul (R-KY).
¿CÓMO ESCANEAR TODO INTERNET 3.7 MIL MILLONES DE IP’S EN POCOS MINUTOS?
Profesionales de hacking ético y servicios de auditoría de seguridad informática normalmente usan escáner para revisar la seguridad. Escaneo de todas las direcciones IP en Internet no es un trabajo fácil, y si usted no tiene los recursos de un botnet, un simple escaneo puede tomar meses. Va a ser muy difícil, si usted quiere tomar una grande foto de internet porque hacer un escaneo de las redes de internet ha tomado típicamente semanas o meses para terminar. Sin embargo, ahora esto es posible, explica expertos de servicios de seguridad informática con la ayuda de nuevas herramientas como ZMap, Masscan y otras. En este artículo vamos a cubrir diferentesherramientas avanzadas y muy rápidas de escaneo de puertos.
ZMap
ZMap está diseñado para ejecutar escaneos generalizados del espacio de direcciones IPv4 o gran parte de ellas. Es una poderosa herramienta para los investigadores de servicios de auditoría de seguridad informática, y se puede escanear el espacio de direcciones IPv4 entero con más de 1.4 millones de paquetes por segundo.
ZMap no pretende reemplazar los escáneres generales como Nmap, cual es excelente para el escaneo de subredes en profundidad. ZMap está diseñado para hacer un escaneo superficial – por lo general de un solo puerto o servicio – de todo el Internet, o al menos el Internet IPv4, desde una sola computadora dedicada, en menos de una hora. Ame Wilson, una consultara de servicios de auditoría de seguridad informática menciona que ZMap es capaz de escanear el espacio de direcciones públicas IPv4 más de 1300 veces más rápido que el Nmap.
ZMAP es competente de trabajar tan rápido porque utiliza grupos de cíclicos multiplicativos. ZMap ha sido diseñado para conseguir el paralelismo y el rendimiento. En primer lugar, es completamente sin estado, lo que significa que no conserva un estatus por conexión. En lugar de mantener una lista gigante de paquetes enviados, y el tiempo que han estado ahí, y cuánto más tiempo debe esperar para cada uno, y cuidadosamente actualización de la lista con cada respuesta; ZMAP simplemente deja todo eso a través de grupos de cíclicos multiplicativos explica Ame Wilson, consultara de servicios de auditoría de seguridad informática.
En segundo lugar, envía en paralelo tantos paquetes como la red lo permite, con el fin de lograr la mayor tasa posible. Los paquetes se envían en un orden aleatorio, por lo que si mucha gente hacen juntos no haya un ataque DDOS, de esta manera se reduce la probabilidad de sobrecarga de una única red. Aunque cada paquete sucesivo sigue una estricta secuencia algorítmica, los números IP rebotan en todo el espacio de direcciones IPv4. Como resultado, usted no recibe cientos o miles de paquetes que convergen en una sola subred al mismo tiempo.
Debido a estas razones con ZMAP podemos escanear alrededor de 3.7 billones de direcciones en las direcciones IPv4, en una hora así que con ZMAP realmente puede revisar todo el Internet.

Por defecto, ZMap realizará un escaneo SYN TCP en el puerto especificado a la máxima velocidad posible. Una configuración más conservadora que escaneará 10,000 direcciones aleatorias en el puerto 80 en un máximo 10 Mbps se puede ejecutar de la siguiente manera:
$ ZMap –bandwidth=10M –target-port=80 –max-targets=10000 –output-file=results.csv
ZMap puede utilizarse también para explorar bloques CIDR o subredes específicas. Por ejemplo, para escanear sólo 10.0.0.0/8 y 192.168.0.0/16 en el puerto 80, ejecute:
ZMap -p 80 -o results.csv 10.0.0.0/8 192.168.0.0/16
Acuerdo con experto de servicios de seguridad informática, por defecto, ZMap entregará una lista de direcciones IP distintas que respondieron correctamente (por ejemplo con un paquete SYN ACK). Le recomendamos utilizar un archivo de lista negra, para excluir tanto el espacio IP reservado/asignado (por ejemplo, multicast, RFC1918), así como las redes que soliciten ser excluidos de escaneos. Por defecto, ZMap utilizará un archivo de lista negra simple que contiene direcciones reservadas y no asignadas en /etc/ZMap/blacklist.conf.
MASSCAN : Escáner puertos de muchas IP’s
Este es el escáner de puertos de Internet más rápido, ya que puede escanear todo el Internet en menos de 6 minutos con la transmisión de 10 millones de paquetes por segundo, acuerdo con profesor de hacking ético. Produce resultados similares a Nmap y utiliza transmisión asíncrona. La principal diferencia es que esa herramienta es más rápido que los otros escáneres. Además, es más flexible, permitiendo rangos de direcciones arbitrarias y rangos de puertos. Masscan utiliza una pila TCP/IP personalizada y eso significa que algo que no sea escaneo de puertos simples causará variación con la pila TCP/IP local. Esto significa que usted tiene que utilizar la opción -S para utilizar una dirección IP independiente, o configurar su sistema operativo para usar cortafuegos en los puertos que Masscan usa.
Aunque Linux es la plataforma principal para esa herramienta, el código funciona bien en muchos otros sistemas como.
- Windows w/ Visual Studio
- Windows w/ MingGW
- Windows w/ cygwin
- Mac OS X /w XCode
- Mac OS X /w cmdline
- FreeBSD
Para ir más allá de 2 millones de paquetes por segundo, necesita un adaptador de Ethernet de 10 gbps de Intel y un driver especial conocido como “PF_RING ADN”. Masscan no necesita ser reconstruido con el fin de utilizar PF_RING. Para utilizar PF_RING, es necesario construir los siguientes componentes:
- libpfring.so (instalado en /usr/lib/libpfring.so)
- pf_ring.ko (su controlador de kernel)
- ixgbe.ko (su versión del controlador de Ethernet de 10 gbps de Intel)

Masscan puede hacer algo más que detectar si los puertos están abiertos explica expertos deservicios de seguridad informática. También puede completar la conexión TCP y la interacción con la aplicación en dicho puerto con fin de agarrar la información de “banner”. El problema con esto es que Masscan contiene su propia pila TCP / IP separada del sistema se ejecuta en. Cuando el sistema local recibe un SYN-ACK desde el objetivo, responde con un paquete RST que mata la conexión antes de Masscan puede agarrar banner. La forma más fácil de evitar esto es asignar Masscan una dirección IP independiente.
Cómo escanear todo Internet
Mientras que es útil para redes más pequeñas y redes internas, el programa está diseñado realmente con todo Internet en mente
# Masscan 0.0.0.0/0 -p0-65535
Escaneo de todo el Internet es malo. Por un lado, las partes de Internet reaccionan mal a analizarlos. Por otro lado, algunos sitios siguen a los escaneos y se suman su IP en una lista de prohibiciones, que le llevará, cortafuegos de partes útiles de Internet. Por lo tanto, recomendamos excluir una gran cantidad de rangos. Para la lista negra o excluir rangos, puede utilizar la siguiente sintaxis:
# Masscan 0.0.0.0/0 -p0-65535 –excludefile exclude.txt
Scanrand
Scanrand es un escáner de puerto de alta velocidad y route-tracer explica profesor de hacking ético de international institute o cyber security. Su alta eficiencia en la exploración se encuentra en su esquema de trabajo en particular. Es un escáner de red rápido que puede escanear hosts individuales hasta las redes muy grandes de manera eficiente. Scanrand puede hacer lo que se llama el escaneo TCP sin estado, que lo distingue de los otros escáneres de red. Scanrand toma un poco de enfoque diferente del escáner de red típico. Se implementa “dispara y olvida” ideología para escanear mezclando con un poco de matemáticas.

Scanrand se divide sí en dos procesos. Un proceso es responsable de hacer nada más que el envío de paquetes SYN usando libnet. El otro proceso es responsable de recibir las respuestas de los equipos remotos enviados utilizando libpcap. Una cosa importante a tener en cuenta es que estos procesos funcionan de forma independiente. No hay consultas con el otro proceso sobre “¿Usted envía este paquete?” o, “¿ Esto es un paquete válido?” Scanrand guarda lista de direcciones IP que están esperando una respuesta y el proceso de envío no espera una respuesta en absoluto. Se dispara un SYN, y luego pasa a la siguiente computadora dejando el proceso de recepción para resolver la avalancha de las respuestas.
Unicornscan
Unicornscan es una herramienta de código abierto (GPL) diseñada para ayudar en la recopilación de información y auditoría de seguridad. No se puede negar que Nmap establece el estándar para la exploración de puertos en Windows y sistemas UNIX. Sin embargo escaneo UDP y TCP (65k puertos) tardan mucho tiempo para terminar. Hay otro escáner que sobresale en la velocidad; Unicornscan es un escáner de puertos asincrónico sin estado que implementa su propia pila TCP / IP. Unicornscan pasa los puertos que se encuentra a Nmap y / o Amap para seguir con análisis.

Mejores Prácticas de Escaneo
Expertos de servicios de auditoría de seguridad informática ofrecen estas sugerencias para los investigadores que realizan escaneos en todo el Internet como directrices para la buena ciudadanía de Internet.
- Coordinar con los administradores de redes locales para reducir los riesgos.
- Verifique que los escaneos no abrumar a la red local o el proveedor de internet.
- Señalan la razón de los escaneos en las páginas web y entradas de DNS de las direcciones del origen.
- Explicar con claridad el objetivo y el alcance de los escaneos en todas las comunicaciones
- Proporcionar un medio simple de la exclusión voluntaria y honrar las solicitudes con prontitud.
- Llevar a cabo las exploraciones no más grande o más frecuente de lo que es necesario para los objetivos de investigación.
- Difundir el tráfico de exploración sobre las direcciones y tiempo cuando sea posible.
No hace falta decir que los investigadores de escaneos deben abstenerse de explotar vulnerabilidades o acceder a los recursos protegidos, y debe cumplir con todos los requisitos legales especiales en sus jurisdicciones.
Los problemas de seguridad y problemas éticos
Como de costumbre, la capacidad de descubrir casi instantáneamente las redes y computadoras que tienen vulnerabilidades de seguridad puede ser una buena cosa para los investigadores de sombrero blanco, pero pueda ser utilizado para el motivo malo por los hackers. Estos son seguramente buenas herramientas y probablemente serán adoptadas por muchos investigadores. Sin embargo, eso poderosos escáneres de Internet podrían ser utilizados por los hackers para actividades maliciosas como la detección y la explotación de las vulnerabilidades. La única cosa que un atacante necesita es una máquina potente y una red con buen ancho de banda. Hoy en día, estos requisitos se pueden satisfacer fácilmente mediante el lanzamiento de una máquina virtual en la nube. La existencia de estas herramientas demuestra también que la ventana de tiempo entre la presencia de vulnerabilidad y su detección por los hackers es corta día a día. Por esta razón, es importante asegurar adecuadamente su propia infraestructura.
Profesores de hacking ético recomiendan que estas herramientas deban ser usadas con cuidado, sin invadir la privacidad de otra persona como cualquiera puede usarlos.
Chrome finally kills off the HTTP-HTTPS “mixed content” warning
Slightly alarming and not wholly useful yellow triangle is being retired.
In the new version of Chrome, which should be rolling out to everyone today, the “mixed content” warning—that mysterious little yellow “caution triangle” in the address bar—will finally be removed. Instead, sites with a mix of HTTP and HTTPS content will show a normal, grey piece of paper, as if it’s a regular HTTP-only website.
According to Google, this change is intended to “encourage site operators to switch to HTTPS sooner rather than later.” The problem is that it’s almost impossible to switch completely from HTTP to HTTPS in one fell swoop—there are just too many factors that need to be tested and debugged. At the same time, webmasters weren’t keen to begin the migration process to HTTPS because of that pesky mixed content warning, which had a tendency to spook less-experienced users of the Information Superhighway. This was far from an optimal solution, according to Google: “During this [migration] process the site may not be fully secured, but it will usually not be less secure than before.”
As a result, in Chrome 46 (on desktop PCs, at least), there will be just three security states: a green padlock (full HTTPS), a red padlock (broken HTTPS), and a grey piece of paper (HTTP). “We’ve come to understand that our yellow “caution triangle” badge can be confusing when compared to the HTTP page icon, and we believe that it is better not to emphasize the difference in security between these two states to most users,” says a Google blog post.
In the long term, Google eventually plans to reduce Chrome’s security states to just two: secure (full HTTPS) and non-secure (everything else). The goal of this hardcore proposal is to “more clearly display to users that HTTP provides no data security.”
Chrome 46, without the mixed security warning, was released to the stable channel yesterday; you may already be running it. If not, your browser should update soon.
Source:http://arstechnica.com/
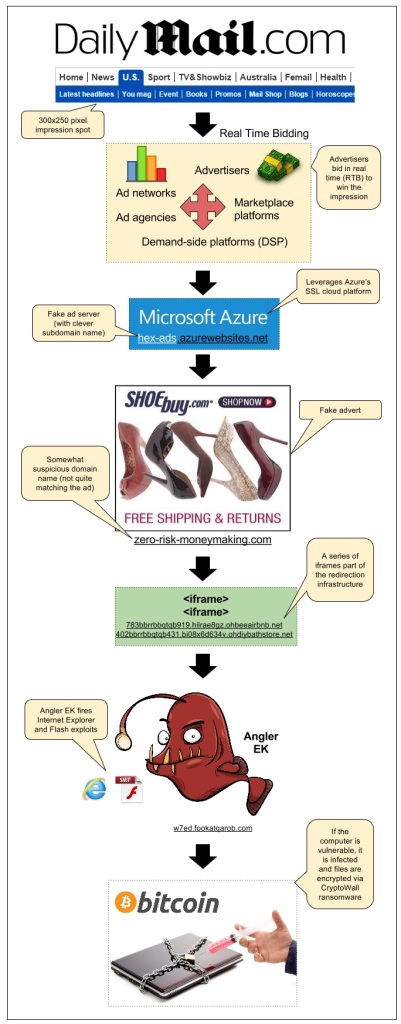
Angler Exploit Kit Blasts Daily Mail Visitors Via Malvertising
There has been a lot of buzz about the powerful Angler Exploit Kit in recent days. One thing is for sure, the gangs using it are extremely resourceful and won’t let attempts at slowing them down get in the way.
We detected an attack that happened via a sophisticated malvertising campaign we had previously documented on this blog: the SSL malvertising attack via Microsoft Azure.
This time it struck on popular British newspaper the Daily Mail which accounts for 156 million monthly visits according to SimilarWeb.
Infection flow:
- Publisher: dailymail.co.uk/ushome/index.html
- Ad call: www5.smartadserver.com/ac?out=js&nwid=1546&siteid=81193&pgname=sf300s&fmtid=35210&tgt=[sas_target]&visit=m&tmstp=[timestamp]&clcturl=http://pixel.mathtag.com/click/img?mt_aid=5829942979381995373&mt_id=1859987&mt_adid=148298&mt_sid=956001&mt_exid=9&mt_inapp=0&mt_uuid=90555615-e26a-4d00-8f31-09247eb00069&mt_3pck=http%3A//beacon-us-iad2.rubiconproject.com/beacon/t/ef1e4098-f217-4beb-8644-01803c6d7545/&mt_lp=http%3A//www.shoebuy.com/new-womens-shoes.htm%3F5DCjbVsxF67hxMc&redirect=
- Fake SSL ad server (malvertising): hex-ads.azurewebsites.net/?=awefyg677873jk2o
- Fake advert for shoebuy.com (malvertising): zero-risk-moneymaking.com/?vC237XnBcMvp
- iframe(1): 783bbrrbbqtqb919.hilrae8gz.ohbeeairbnb.net/287e1e7f185ac57172a0a7b70483e
- iframe(2): 402bbrrbbqtqb431.bi08x6d634v.ohdiybathstore.net/ced1d59c80127f0fb50e6e083d3
- Angler Exploit Kit: w7ed.fookatqarob.com/boards/viewforum.php?f=61ls0&sid=826888i5.161802rr6070
Malvertising has been one of the main infection vectors and continues to affect large publishers and ad networks through very distinct campaigns, very much like a whack-a-mole game.
In addition to spreading via compromised websites, Angler EK leverages malvertising thanks to several different threat actors who use clever ways to go undetected as long as possible or are able to quickly adapt and get back on their feet if one of their schemes gets too much attention and is disrupted.
During the past months we have been working very closely with ad networks, publishers, cloud providers and other companies that have been abused by these attacks.
In addition, we hope that well documented cases such as this one help consumers to realize that malvertising is a very dangerous and yet often misunderstood threat. There is no such thing as a safe website anymore and it is everyone’s responsibility to ensure their devices are fully patched and well protected.
We contacted the affected publisher (DailyMail) and related ad networks right when we found out about this incident. On 10/12, we were informed by MediaMath that the malicious creative had been disabled.
Malwarebytes Anti-Exploit users were already protected against this attack, thanks to its proactive exploit mitigation capabilities.
Great Firewall of China at Work, Apple News May Have Been Blocked
Apple news (Currently in testing mode) has been taken down in China by the company itself. The reason behind this seems obvious: Strict internet laws and surveillance by the Chinese government.
Though, Apple has a very big market in China (2nd largest to be precise) it still had to take down its new service.
According to the reports from the New York Times, when you try to open Apple news on your device in China, it shows an error message: “Can’t refresh right now. The news isn’t supported in your current region.”
But, if you use the same device in the USA, the news feed loads properly, which clearly means the service has been taken down in China.
“THEY’RE CENSORING NEWS CONTENT THAT I DOWNLOADED AND STORED ON MY DEVICE PURCHASED IN THE USA, BEFORE I EVEN ENTER CHINA JUST BECAUSE MY PHONE HAPPENS TO CONNECT TO A CHINESE SIGNAL FLOATING OVER THE BORDER,”“THEY’RE CENSORING NEWS CONTENT THAT I DOWNLOADED AND STORED ON MY DEVICE PURCHASED IN THE USA, BEFORE I EVEN ENTER CHINA JUST BECAUSE MY PHONE HAPPENS TO CONNECT TO A CHINESE SIGNAL FLOATING OVER THE BORDER,”
This means that all the news content has been censored and is not available to the users using the devices in China.
This is not the first time a tech giant had to take such a step. Google did it also in 2010 when they re-directed all the Chinese IP addresses to Google’s Hong Kong domain.
Although, Google still provides services in China, most of Google’s products are blocked by authorities.
Weibo (Chinese version of twitter) once was a popular community in China, also declined due to China’s strict laws. Web blocks have been quite common in China and they all come under a system known as “Great Firewall of China censorship”
They have even used this for local shutdowns. One such instance was in Xinjiang when they completely blocked the internet service in the region after riots.
The Great Firewall of China known for censoring/blocking websites in the country. In the past, the firewall blocked Reuters website as a result of a DDoS attack on the great firewall. However, the University of California, Berkley and the University of Toronto researchers identified that the Great Firewall hasn’t been used by China at all but instead a very strong new weapon which they have labelled as the Great Cannon.
Source:https://www.hackread.com
Company Behind the Wall Street Journal Hacked, Subscriber Details Exposed
Some credit card information may have also been stolen
The Wall Street Journal is reporting that its parent company, Dow Jones & Co. has been the target of a cyber-attack, during which data for some of its subscribers was accessed and potentially stolen.
Dow Jones, a News Corp subsidiary, is reporting that between August 2012 and July 2015, an attacker has illegally gained access to one of its servers which could have resulted in exposure of information for around 3,500 of its subscribers.
This includes names, addresses, email addresses and phone numbers, for both current and former Dow Jones subscribers.
The data breach was reported by US law officials in late July, and Dow Jones sent notification letters to all affected subscribers after an investigation by a security vendor confirmed the breach.
In the letter, Dow Jones Chief Executive William Lewis said that the attack seems to be part of a bigger campaign which also targeted other similar publications.
The attackers wanted to get their data on customer contact information, so they would be able to send unsolicited emails or letters, which could be used to carry out other types of cyber-attacks.
Additionally, the criminals may have also gotten their hands on some credit card information as well.
“As part of the investigation to date, we also determined that payment card and contact information for fewer than 3,500 individuals could have been accessed, although we have discovered no direct evidence that information was stolen,” Mr. Lewis’ letter states.
Source:http://news.softpedia.com/
FBI Warns About the Dangers of EMV Credit Card Chips
All US banks will replace all magnetic strip cards with EMV chip-based cards by the end of October 2015
The US is finally catching up to the rest of the world as banks are getting ready to migrate most of their customers to EMV chip-based credit and debit cards. While this technology is not new, it is not as widespread in the States and most people don’t know how to particularly use it.
Now, to prevent abuses and better inform American citizens, the FBI has put out a Public Service Announcement (PSA), about the dangers that are still looming over chip-based card users.
While EMV cards are many times more secure over classic cards that used a magnetic strip and the user’s signature to authenticate them, the FBI warns that the presence of the chip does not completely safeguard users from dangers.
The card’s EMV chip, named after the companies that pioneered it, Europay, MasterCard, and Visa, is an advancement in card security technology, mainly because of the famous 4-digit PIN which serves to protect transactions.
Cards with EMV chips are safer, but not 100% safe, FBI warns
Despite this, the FBI warns new EMV chip card users that are going to migrate to the technology this October in the US, that hackers may still be able to steal their data either by installing malware on PoS (Point of Sale) systems or by stealing card details (like before) and using them in online or phone transactions, where the merchant cannot verify the card via a PIN.
Additionally, the FBI also urges new EMV card holders to activate their new cards as soon as possible and reinforces the old advice of keeping your credit card safe at all times, since thieves can use EMV or non-EMV cards in the same manner.
Basically, what the FBI is trying to say is that the same security rules that were applied before need to be applied with the new cards as well, since the new EMV chip and PIN do nothing more than add an extra layer of security, but not fully protect users from all threats.
Source:http://news.softpedia.com/
Microsoft Pays $24,000 To Researcher For Preventing Dangerous Outlook Worm
Email is, perhaps, the most hopelessly insecure of all web apps. For individuals and businesses it can be a nightmare attempting to keep hackers out of inboxes. This summer, Wesley Wineberg, a security researcher at Synack, found that to be all too true, discovering a bug affecting all services running over Microsoft’s Live.com, allowing malicious hackers to gain access to a user’s entire Outlook account.
Admittedly, there was plenty of trickery involved. Wineberg first analysed the way in which Outlook allowed other apps to access it, using a standard set of authentication code known as OAuth. He discovered he could create an “evil app” containing an OAuth bypass, only needing to trick a user to visiting a website and they would effectively grant that naughty software access to everything in their account.
But for most hackers, this kind of vulnerability, known as across-site request forgery (CSRF), is all too common across the web. Typically, these attacks end as soon as the legitimate user logs out, but in the case of Outlook anyone abusing Wineberg’s vulnerability would have permanent access to the account, Wineberg said.
Most concerning of all, it could have been abused to create a nasty email worm, he added. “The real danger of this vulnerability is that it would be very easy to turn into the classic email worm of decades past. After the first victim is compromised, this vulnerability could be used to email every one of their contacts with a link that would then compromise those users’ accounts as well,” Wineberg noted, providing the below footage of his attack to FORBES.
“This really is just a classic CSRF vulnerability. The only thing that’s surprising about it is that it’s in a critical authentication system which ultimately can be used to take over any user’s account,” he added in a Synack blog post.
Microsoft fixed the bug in mid-September, paying out a whopping $24,000 to Wineberg for that vulnerability alone as part of the tech titan’s bug bounty program. As he was doing the research in his own time, Wineberg kept all the money rather than handing it over to his employer.
Just earlier this week, researchers highlighted more problems in Outlook, though affecting business users. Israeli company Cybereason discovered a malicious DLL loaded into the Outlook Web App (OWA) server, the webmail part of Microsoft Exchange Server, hosted by one of its clients. That DLL file was able to install a backdoor on the OWA server and wait for users to sign in, hoovering up their usernames and passwords as they did.
By its very definition, OWA has a wide attack surface, effectively acting as a route from the outside internet, past the firewalls and into the internal network, Cybereason noted. Where companies configure OWA to let remote workers in, they’re risking letting hackers in too.
Even those bidding for better webmail security, such as the PGP encryption service ProtonMail, can’t offer total protection, especially not from sophisticated hackers and web attacks like those demonstrated by Wineberg. The struggle goes on…
Source:http://www.forbes.com/
Exclusive: In lawsuit over hacking, Uber probes IP address assigned to Lyft exec – sources
Eight months after disclosing a major data breach, ride service Uber [UBER.UL] is focusing its legal efforts on learning more about an internet address that it has persuaded a court could lead to identifying the hacker. That address, two sources familiar with the matter say, can be traced to the chief of technology at its main U.S. rival, Lyft.
In February, Uber revealed that as many as 50,000 of its drivers’ names and license numbers had been improperly downloaded, and the company filed a lawsuit in San Francisco federal court in an attempt to unmask the perpetrator.
Uber’s court papers claim that an unidentified person using a Comcast IP address had access to a security key used in the breach. The two sources said the address was assigned to Lyft’s technology chief, Chris Lambert.

The court papers draw no direct connection between the Comcast IP address and the hacker. In fact, the IP address was not the one from which the data breach was launched.
However, U.S. Magistrate Judge Laurel Beeler ruled that the information sought by Uber in a subpoena of Comcast records was “reasonably likely” to help reveal the “bad actor” responsible for the hack.
On Monday, Lyft spokesman Brandon McCormick said the company had investigated the matter “long ago” and concluded “there is no evidence that any Lyft employee, including Chris, downloaded the Uber driver information or database, or had anything to do with Uber’s May 2014 data breach.”
McCormick declined to comment on whether the Comcast IP address belongs to Lambert. He also declined to describe the scope of Lyft’s internal investigation or say who directed it.
Lambert declined to comment in person or over email.
Attorneys for the Comcast subscriber, who is not named in court documents, did not respond to an interview request on Monday.
In an email on Monday, an Uber spokeswoman declined to comment on any aspect of the case beyond what is in court filings, including what led the company to believe that more information about the Comcast subscriber might lead them to the hacker.
Uber’s lawsuit alleges the hacker violated civil provisions of the federal Computer Fraud and Abuse Act, as well as a similar California law. It is unclear if the leaked driver information was ever used by the hacker or anyone else.
According to documents filed in the case, the company learned months after the hack that someone had used an Uber digital security key to access the driver database. A copy of the key was inadvertently posted by Uber on one of its public pages on the code development platform GitHub in March of 2014, prior to the breach, the court filings show, and remained there for months.
After Uber discovered the unauthorized download, it examined the Internet Protocol addresses of every visitor to the page during the time between when the key was posted and when the breach occurred, according to court documents. The Uber review concluded that “the Comcast IP address is the only IP address that accessed the GitHub post that Uber has not eliminated” from suspicion, court papers say.
The numeric Comcast IP address and some other details have been redacted from court filings, so Reuters was unable to independently assess whether there was a connection between Lambert and the Comcast IP address. The two sources, however, said Uber researched the address and discovered that it showed up elsewhere in Internet postings associated with Lambert, and that the address was assigned to his name.
Lawyers for the unnamed Comcast subscriber have pointed out in court that the web page containing the key was publicly available and that anyone could have visited the site without violating any laws. They also stressed that the data breach stemmed from a different IP address.
In his statement on Monday, Lyft spokesman McCormick noted that “Uber allowed login credentials for their driver database to be publicly accessible for months before and after the breach.”
The two sources said that the address from which the hack was launched is associated with a virtual private network service. One of them added that the service is based in a Scandinavian country and is known for vigorously protecting the privacy of its users. The hacker’s numeric IP address is redacted from court papers.
In July, the federal magistrate judge in San Francisco approved Uber’s request for a subpoena granting the company access to the Comcast subscriber’s identity, source of payment and other subscription details. The subpoena also requires Comcast to disclose information connecting the subscriber to certain other IP addresses and to the GitHub web pages.
Attorneys for the unnamed Comcast subscriber appealed to the 9th U.S. Circuit Court of Appeals, and Beeler put her ruling on hold pending the outcome.
In fighting the subpoena, the subscriber’s attorneys asserted in court that Uber has improperly focused on their client instead of other possible perpetrators of the breach.
They noted that automated web crawlers also visited the site with the security key. Google and other search engines use such crawlers to visit and gather information from web pages for indexing and caching. One of those crawlers could have saved the key somewhere else, the subscriber’s attorneys argued in court filings, where it could have been accessed by the hacker.
The attorneys also suggested that a disgruntled Uber engineer could have taken the driver data to a new job, as it would be valuable for a competitor.
In her ruling, Beeler concluded there was “no evidence” that the key was available anywhere else online other than the place Uber inadvertently posted it.
Lyft, with a valuation of $2.5 billion, is much smaller than rival Uber, valued at $51 billion, based on previous funding rounds. The companies compete fiercely for drivers and customers.
Lambert has been Lyft’s CTO since 2012, according to his LinkedIn page. Prior to that, he was a software engineer at Google for 5 years, working on mobile maps and Google location.
Source:http://www.reuters.com/
Windows Phone Store Distributes Fake Apps Infected with Adware
Over 58 infected apps detected on the Windows Phone Store
After the Apple App Store and the Google Play Store were used to distribute all kinds of malware to users’ phones, it seems that now’s the time for Microsoft’s Windows Phone Store to be abused as well.
While Apple and Google’s stores were used to push quite dangerous malware, Microsoft’s store seems to be affected by a much less critical issue, allowing developers to upload fake apps that only force-feed users with adware.
According to Avast, Windows Phone users are in danger of being duped into installing fake apps that are repackaged versions of legitimate applications, retooled to serve ads and redirect users to buy or download specific products.
58 of these kind of (fake) apps were uploaded on the Windows Phone Store, and the culprits are two developers: Ngetich Walter and Cheruiyot Dennis.
Some of the fake apps uploaded by these two developers mimic successful apps like the ones from CNN, Avast, Facebook, BBC, Bet365, and WhatsApp.
Fake apps are showing ads and redirecting users to other apps and websites
As you can see from the screenshots attached to this article, the apps come with a real-looking, fully functional UI, but after a certain period of time, the user is prompted with an interstitial ad that covers their entire screen.
If this add is clicked, the user is redirected to a page where they are then asked to download or install various other apps. In some cases, this redirect occurs automatically, without the user doing anything.
The two behind this campaign are gaining money from various advertising campaigns, which reward developers that get other people to click on ads, or to install apps from a list of sponsored applications.
“For some reason, no one takes the time to report bad apps, even if it’s clear that they are fake and the majority of user reviews are extremely negative,” says Filip Chytry of Avast.
Softpedia has checked the Windows Phone Store, and while we haven’t seen any apps for Ngetich Walter, we have been able to find 20 apps from Cheruiyot Dennis still being listed.
Source:http://news.softpedia.com/
North Korean Hackers Suspected for Attack on Seoul’s Subway System
Hackers gained access to 213 Seoul Metro computers
According to South Korea’s National Intelligence Service (NIS), Seoul’s subway system has been attacked using techniques linked to a North Korean-linked hacking group.
The information came to us via the Korea Herald (not working now, probably under DDoS,WebCache view here), which reported today that NIS discovered an attack on Seoul Metro, a state-owned company that manages four subway lines in the nation’s capital (Lines 1, 2, 3, and 4).

The attack happened during July 2013, and as a consequence of hacking two server gateways, hackers gained access to 213 of Seoul Metro’s computers.
NIS is also reporting that 58 out of the 213 computers were infected with malware, which helped attackers steal 12 documents from the computers’ hard drives.
According to official statements, the documents did not contain any kind of sensitive information, just basic human resources data, along with internal management procedures.
The Seoul subway system was not affected by the hack
None of the affected computers was used to manage the actual subway system and its trains.
Seoul Metro representatives say that the subway network is managed through a different computer system, not connected to the Internet, just for these reasons.
As with any hacking incident that happens in South Korea, first suspicions will always be taking into account that a North Korean state-sponsored group was at the source of this attack.
NIS says that because the incident took place so long ago, there were not enough logs to analyze and detect “the first point of hacking and the source of the code.”
Officials do say that the techniques they’ve observed are very similar to the same techniques used in the hacking of South Korean banks and broadcasters in March 2013. At that time, for those events, evidence pointed towards North Korea.
Only this year, Seoul Metro is reporting that over 350,000 cyber-attacks have been recorded targeting its network.
Source:http://news.softpedia.com/
¿CÓMO INTERCEPTAR Y HACER ATAQUES DE HACKING SOBRE COMUNICACIONES SATELITAL?

En este artículo vamos a cubrir el ataque de hacking satelital que ha sido utilizado por grupos de hackers desde muchos años. Este ataque le proporcionará anonimato completo y así va a ser muy difícil por los expertos informática forense para rastrearle. En el último artículo hablamos acerca de la intercepción de tráfico por satélite y cubrimos los siguientes temas.
http://noticiasseguridad.com/tecnologia/como-interceptar-comunicaciones-satelital-facilmente/
- Configuración de antena parabólica.
- Diferentes satélites y frecuencias correspondientes.
- Diferentes programas para escanear frecuencias satelitales.
- Formas de interceptar el tráfico satelital.
- Cómo tener conexión a internet por satélite, televisión gratis y ataques básicos de piratería /hacking.
Con la ayuda de un software como DVB Snoop y Wireshark podemos interceptar las comunicaciones por satélite y tomar una descarga de datos, como comunicación no está cifrada explica Mike Stevens experto de hacking ético y empresa de seguridad informática. Después de seguir los pasos mencionados en el artículo anterior, vamos a configurar antena parabólica apuntando al satélite específico que emite el tráfico. Como sabemos que los paquetes no están cifrados, utilizaremos DVB-Snoop junto a Wireshark para interceptar el tráfico. Una vez que se identificamos una dirección IP de satélite que ruta a través del enlace descendente del satélite, podemos empezar a interceptar los paquetes de Internet a esta IP específica. Para interceptar los paquetes, podemos hacer ataque de secuestro TCP fácilmente revela experto de empresa de auditoría informática.
¿Qué es el ataque de secuestro TCP satelital?
Protocolo de Control de Transmisión (TCP) es un protocolo muy importante de la capa de transporte. TCP es un protocolo orientado a la conexión, lo que significa una conexión que se hace y se mantiene hasta que los programas de aplicación en cada extremo hayan terminado la comunicación. Este protocolo determina cómo dividir los datos de la aplicación en paquetes que la red puede entregar. También se comunica con la capa de red y gestiona el control de flujo. El protocolo TCP divide los datos en paquetes, los numera y luego los envía de forma individual a la capa de IP para la entrega. También gestiona la retransmisión y el reconocimiento de los paquetes según expertos de empresa de seguridad informática. En el modelo de comunicación Open Systems Interconnection (OSI), TCP cubre partes de la capa 4, la capa de transporte, partes de la Capa 5 y la capa de sesión. TCP procesa paquetes por número de secuencia y pone los paquetes fuera de orden en sus lugares. El protocolo TCP es el único protocolo de la familia de protocolos TCP/IP que soporta los mecanismos de paquetes adicionales, identificación de la conexión y la autenticación. Eso explica por qué los protocolos de nivel de aplicación, tales como SMTP, FTP, etc. utilizan TCP para obtener acceso remoto a otras máquinas. Para la definición de los paquetes, la cabecera TCP consta de dos campos de 32 bits que se utilizan como contadores de paquetes. Se denominan número de secuencia y reconocimiento. Otro campo, llamado Bit de Control, es 6 bits de largo, y lleva los siguientes indicadores de comando y es muy importante entender esos indicadores para hacer auditoría informática:
URG: Indicador de Urgencia
ACK: Indicador de Reconocimiento
PSH: Indicador de Empuje
RST: Indicador para Restablecer
SYN: Indicador para sincronizar los números de secuencia
FIN: Indicador, cuando no hay más datos del remitente
Durante el ataque secuestro TCP el hacker se hace cargo de sesión de comunicación entre los diferentes usuarios haciéndose pasar por el usuario autorizado. Una vez que se ha accedido a detalles de la sesión del usuario, el hacker pueda enmascararse como el usuario y hacer cualquier cosa que el usuario está autorizado a hacer en la red.
Métodos de secuestro TCP satelital
Existen diferentes métodos de secuestro TCP satelital explica Dave Taylor experto deinformática forense y algunos de ellos son:
IP Spoofing (Falsificación de IP)
IP spoofing es una técnica utilizada para obtener acceso no autorizado de la comunicación, donde los mensajes se envían por el secuestrador a un ordenador con una dirección IP de un host de confianza. Cuando el secuestrador ha suplantado con éxito una dirección IP, él / ella determina el siguiente número de secuencia que el satélite espera e inyecta el paquete RST con el mismo en la sesión TCP antes de que el cliente puede responder. Así crea un estado no sincronizado. Los números de secuencia y ACK ya no están sincronizados entre cliente y satélite y el secuestrador aprovecha de esta situación para establecer la conexión como usuario de confianza explica experto de empresa de auditoría informática.
Blind Hijacking (Secuestro Ciego)
Cuando el enrutamiento de origen está desactivado y secuestrador no puede ver la respuesta del satélite. El secuestrador utiliza secuestro ciego donde el secuestrador inyecta sus datos maliciosos en comunicaciones interceptadas en una sesión TCP. Así, la palabra “ciegos” porque el secuestrador puede enviar los datos o comandos, pero no puede ver la respuesta. El secuestrador, básicamente, adivina las respuestas del cliente y el satélite.
Man in the Middle (MiTM) (Interceptar Paquetes)
Esta técnica implica el uso de un analizador de paquetes (sniffer) para interceptar la comunicación entre el cliente y el satélite. Todos los datos entre los hosts fluyen a través de sniffer del secuestrador y él es libre de modificar el contenido de los paquetes. Esta técnica significa que los paquetes sean enviados a través de host del secuestrador señala experto de empresa de auditoría informática.
Por el secuestro de comunicación satelital los hackers normalmente utilizan combinación de man in middle y ataque de IP spoofing. Una comunicación normal TCP tiene un apretón de manos de 3 vías usando paquete SYN de usuario por satélite, luego SYN + ACK del satélite al usuario y, por último ACK del usuario al satélite.

Durante un ataque de secuestro TCP, el hacker intercepta la comunicación y envía un paquete RST para el usuario y se inicia la comunicación con el satélite con la dirección IP falsificada del usuario.

Cómo hacer Secuestro TCP Satelital
Puede utilizar las siguientes herramientas para hacer TCP Secuestro Satelital:
Hunt
Hunt (distribución binaria de Linux) es un programa para entrometerse en una conexión TCP, revisarlo y reiniciarlo señala experto de empresa de seguridad informática.
1) Con Hunt, podemos hacer la gestión de conexiones y detectar una conexión permanente. Hunt permite secuestro activo con la detección de ACK, ARP spoof y la sincronización del cliente con el satélite después de secuestro.
2) Con Hunt, podemos reiniciar el daemon para restablecimiento de conexión automática y actuar como relay de daemon para ARP spoof. Permite buscar información en el tráfico y la recolección de direcciones MAC.
3) Hunt actúa como programa para resolver host DNS y el motor de paquetes extensible para la observación de TCP, UDP, ICMP y el tráfico ARP.

Shijack
Shijack es una herramienta de secuestro de conexiones TCP para Linux, FreeBSD y Solaris. La herramienta requiere Libnet. Es un código de fuente abierta y se puede utilizar para tomar el control de la sesión TCP.

Scapy
Scapy es una poderosa herramienta de manipulación de paquetes interactivo escrito en Python, y la mejor parte es que también pueda ser utilizada como una biblioteca en programas Python, que proporciona la pentester la capacidad de crear su propia herramienta basada en la exigencia. Scapy nos permite interceptar crear, enviar y paquetes rebanada modificados para hacking y el análisis de informática forense.

Juggernaut
Juggernaut es básicamente un sniffer de red, que también puede ser utilizado para secuestrar sesiones TCP. Se ejecuta en Linux y tiene un módulo Trinux también. Juggernaut puede ser activado para ver todo el tráfico de red en la red local, o se pueda configurar para escuchar un “token” especial. De esta manera, esta herramienta puede ser utilizada para capturar ciertos tipos de tráfico y puede funcionar durante unos días, y luego el atacante sólo tiene que recoger el archivo de registro que contiene el tráfico registrado.

En el próximo artículo vamos a cubrir más sobre ataques de hacking más avanzados que involucran satélites, también pueden aprender durante curso avanzado de hacking ético de International Institute of Cyber Security. Este artículo es sólo con fines educativos.
Leer Más sobre eso
http://noticiasseguridad.com/tecnologia/como-interceptar-comunicaciones-satelital-facilmente/
Fuente:http://www.iicybersecurity.com/ataques-comunicaciones-satelital.html
Anonymous Leaks Top Secret Canadian Government Documents, Again
Operation Anon Down continues as Anonymous enacts revenge
Anonymous is continuing its cyber-protest against the Canadian government, which started after the shooting of a Canadian protester, and it has now released a secret document related to some of the country’s foreign diplomatic centers in the UK.
The document released last week to 10 Canadian media agencies has been confirmed as authentic and contains information about the Department of Foreign Affairs selling one of its diplomatic buildings in London, and then relocating and refurbishing a new one.
Opinions are still split if the document is of any importance, with some arguing that it reveals a shady transaction, because the Canadian government eventually bought a new building, paying CAD300 million (USD228 million) more than it anticipated, as reported by the National Post.
The document is dated February 6, 2014, and the operations detailed in it seem to have taken place in 2012.
Curiously, this banal transaction was labeled as “top secret” by the Canadian government, which also raised more suspicions.
Despite the leak, the Canadian government has been more annoyed with the fact that hackers found a way to break into their systems, more than anything else.
Operation Anon Down: Anonymous wants justice
This document leak is part of Anonymous’ Operation Anon Down, which is in response to an incident that took place in Dawson Creek, B.C., in July.
Back then, a protester wearing the classic Guy Fawkes (Anonymous) mask was shot and killed by an RCMP officer. Operation Anon Down was started as an online protest to force the Canadian Government to release the officer’s name, fire him from the force, and bring official charges against him.
The protest in which the masked man (James McIntyre, 48) was shot wasn’t even related to Anonymous, but against a local hydroelectric project.
Previously in July, the hacktivist group released Canadian Cabinet documents regarding its spying policy and current capabilities.
Details about Operation Anon Down:
Source:http://news.softpedia.com/
Breaking Bad Ransomware Goes Completely Undetected by VirusTotal
Would you like a touch of Walter White with your malware?
Heimdal Security is reporting on a new ransomware campaign they’ve uncovered, which, at the time of this article, is still undetected by any of the 57 security products listed on Google’s VirusTotal antivirus aggregator.
This new ransomware wave is the fourth the company has detected only in September, and even if it uses traditional ransomware delivery methods, it’s still evading detection from known cyber-security providers.
The campaign is being spread in Scandinavia using spam emails, which come with a Word document attached. This file is booby-trapped with a malicious macro that, when the document opens, executes and downloads the ransomware on the victim’s PC.
Ransomware: I am the one who knocks!
The ransomware then goes on to encrypt the user’s most important documents, by renaming files with the “.breaking_bad” file extension.
Access to the encrypted files is locked, and owners can regain their data only after they pay the ransom by sending emails to two different Gmail accounts.
While the “.breaking_bad” file extension and the two different Gmail accounts is an imaginative touch, the way the ransomware is delivered is quite trivial, being also used by many other malware campaigns, not just ransomware.
The same old Microsoft Word macro trick
On this very same day, we reported on the Dyreza banking trojan, which used a similar technique of packing malware download instructions inside Word macros.
Word macros have also been used by a Chinese hacking group to target Russian military bases just this summer. And attackers are also using them to deliver old-school Visual Basic malware inside Word documents.
The reason why this technique is so beloved by the underground virus-making community is that it allows them to create malicious files which aren’t malicious at all.
This is probably the reason why the ransomware campaign is currently undetected in VirusTotal. The Word documents look like any other Word documents, because they only contain “a few instructions to download a file from the Web” inside a macro. That file can be anything: an image, a CSS file, or a malware payload. Since the malware is not actually packed inside the Word file, the only way to protect against this type of threats is by educating users to stop opening random Word files received via the Internet from unknown people.
Source:http://news.softpedia.com/