Month: January 2016
CenterPOS – The evolution of POS malware
Security Experts at FireEye discovered a new strain of POS malware dubbed CenterPOS that is threatening the retail systems.
In the last 2/3 years, we have seen a significant increase in the number of POS malware, their diffusion is becoming even more worrying. We read about many high-profile breaches that involved high-complex malware targeting payment systems worldwide.
Today we catch up with CenterPOS, a malicious code under investigation of FireEye experts. This fairly new malware was discovered in September 2015 in a folder that contained other POS malware, including NewPoSThings, two Alina variants known as “Spark” and “Joker,” and the infamous BlackPOSmalware.

The sample analyzed by FireEye is identified with an internal version number 1.7 and contains a “memory scraper that iterates through running processes in order to extract payment card information. The payment card information is transferred to a command and control (CnC) server via HTTP POST”:
Many variants of the malware version 1.7 were found, associated with different CC locations:

FireEye even discovered a live CnC server that show that in the underground the malware is known as “Cerebrus”( don’t mix it with the RAT also known as Cerberus):( don’t mix it with the RAT also known as Cerberus):
Besides the version 1.7, a version 2.0 was found, and it’s very similar with 1.7 with the difference that in version 2.0 its used a config file to store the information related to the CC server.
“The malware contains two modes for scraping memory and looking for credit card information, a “smart scan” mode and a “normal scan” mode. The “normal scan” mode will act nearly the same as v1.7”
The CenterPOS scans all processes searching for those that meets the following criteria:
- The process is not the current running process.
- The process name is not in the ignore list.
- The process name is not “system,” “system idle process,” or “idle.”
- The process file version info does not contain “microsoft,” “apple inc,” “adobe systems,” “intel corporation,” “vmware,” “mozilla,” or “host process for windows services.”
- The process full path’s SHA-256 hash is not in the SHA-256 blacklist.
If a process meets the criteria ” the malware will search all memory regions within the process searching for credit card data with regular expressions in the regular expression list.”
Moving on to the “smart scan”, this scan is initiated with a normal scan, and “any process that has a regular expression match will be added to the “smart scan” list. After the first pass, the malware will only search the processes that are in the “smart scan” list.”
“After each iteration of scanning all process memory, the malware takes any data that matches and encrypts it using TripleDES with the key found in the configuration file.”
The malware sends information to the CC server about the “hacked” system including the current settings, always after a performed scan. The collected info includes all system users, logged in users, sessions, process list, and current settings list. The info is send by a separate HTTP POST request.
” The malware primarily sends data to the CnC server, but can also receive commands and in addition to processing commands, the malware also accepts commands to update its current settings.”
The next table includes data related the variants of the CenterPOS version 2.0 found by FireEye:

As I referred in the beginning of the article, many POS malware were found in the last 2/3 years and this is related with the huge demand criminal underground. Retailers represent a privileged target to steal payment card information and get money.
CenterPOS or Cerebrus, as will likely continue to evolve, their authors will include more functionalities in future versions.
If you feel interested to get more details, please visit FireEye blog, here.
About the Author Elsio Pinto
Samsung Patches Critical Vulnerabilities in Android Devices
Samsung has released a maintenance update for its major Android flagship Galaxy models to resolve 16 vulnerabilities in these devices.
The updates, available as part of the company’s monthly Security Maintenance Release (SMR) process, include all patches released by Google up to its January 2016 Android Security Bulletin. The release also includes several Samsung Vulnerabilities and Exposures (SVE) items.
Samsung’s January 2016 SMR includes a patch for a remote code execution (RCE) vulnerability in Android Mediaserver (CVE-2015-6636) rated as Critical. During the media file and data processing of a specially crafted file, an attacker could exploit the flaw to cause memory corruption and remote code execution.The vulnerability appears to be similar in scope to the “Stagefright” vulnerability that was disclosed in July 2015, which affected nearly one billion Android devices. Google’s initial patch did not properly address the mediaserver service flaw.

Another Critical flaw addressed in the updates is CVE-2015-6617, a flaw in Skia that allows remote attackers to execute arbitrary code or cause a denial of service via a crafted media file. The vulnerability was resolved by Google in the December 2015 bulletin, and Samsung included it in its December SMR too.
This month, Samsung Android devices also received fixes for a series of Android flaws rated Medium risk, such as CVE-2015-6643, CVE-2015-5310, CVE-2015-6644, CVE-2015-6645, all of which were patched in Google’s December 2015 or January 2016 updates for the Nexus devices.
Of the 7 SVE items included in Samsung’s January 2016 SMR, three are rated Critical and could result in arbitrary code execution, memory corruption, or FRP/RL bypass. The first could be triggered when a malformed BMP image is scanned by a facial recognition library, the second is a flaw in ‘libQjpeg.so’ and can be triggered by a malformed JPEG file, while the third is a bug in download mode that can reset the FRP/RL partition by using ‘Odin’ protocol, according to the release notes.
Samsung also patched a vulnerability resulting from a combination of unprivileged local apps being able to access some providers and an SQL injection (SQLi) flaw, which allowed applications to access all messages from SecEmail. The update also resolves a memory corruption issue rated Medium, along with a Low rated bug that could cause crashes when malicious service commands were called.
Samsung didn’t provide information on all SVEs included in the package, but revealed that at least two of the bugs affect the Samsung Galaxy S6 smartphone. Users are advised to install the security updates as soon as possible, to ensure their devices are protected from any attempts to exploit the fixed vulnerabilities.
Samsung began delivering monthly updates to its Android users in October 2015, afterannouncing such plans in August. The move followed Google’s decision to resolve flaws in the mobile OS on a monthly basis, after the critical “Stagefright” vulnerability was found in July to affect nearly one billion devices.
Source:http://www.securityweek.com/
Hackers are blackmailing the creator of Open-Source Ransomware
The Turkish security researcher Utku Sen was blackmailed by hackers behind the Magic ransomware to close his projects.
The developers behind the open source-based “Magic” ransomware are blackmailing the creator of Hidden Tear and EDA2 in order to force the developer to abandon the projects.
Recently I have written about the RANSOM_CRYPTEAR.B ransomware developed Utku Sen starting from a proof-of-concept code available online.
According to the experts at TrendMicro, Utku Sen made a serious error in the development, resulting in victims’ files being completely unrecoverable. Researchers who analyzed the source code discovered that it was a modification of a proof-of-concept ransomware dubbed Hidden Tear that was leaked online by the Turkish coder Utku Sen for educational purpose.
It is not surprising that crooks have not missed the occasion as remarked by TrendMicro.
“Unfortunately, anyone on the internet can disregard this warning. This became evident when Trend Micro discovered a hacked website in Paraguay that distributed ransomware detected as RANSOM_CRYPTEAR.B. Our analysis showed that the website was compromised by a Brazilian hacker, and that the ransomware was created using a modified Hidden Tear code.” states a blog post published by TrendMicro.
The “Hidden Tear” is available on GitHub and it’s fully functional, it uses AES encryption to encrypt the files and displays a warning to users to pay up to get their data back.

“While this may be helpful for some, there are significant risks. The Hidden Tear may be used only for Educational Purposes. Do not use it as a ransomware!” explained utkusen.
The hacker also developed a second open-source project for a ransomware dubbed EDA2. When the problem was discovered, Utku Sen removed all the files from the EDA2 project.
Recently another ransomware, based on the open-source code, has been detected in the wild, it has been dubbed “Magic” because it encrypts user files and adds a “.magic” extension to them.
Now the criminal gang behind the Magic ransomware began blackmailing the hacker Sen in an effort to shut down the Hidden Tear. The group announced that in a forum post that they are willing to provide victims with the decryption keys for free in case Sen agrees to close his open source ransomware projects.
Sen refused the condition and declared war on the blackmailers.
According to Sen, he deliberately inserted security flaws in both the Hidden Tear and EDA2 to sabotage cybercriminals using the proof-of-concept ransomware.
The Sen’s plan worked with the Hidden Tear allowing the recovery of the file encrypted by the Linux.Encoder and Cryptear.B ransomware, meanwhile failed with EDA2.
Sen inserted vulnerabilities in the EDA2’s control script in order to retrieve decryption keys. The problem is that despite the presence of the flaws, the unique way to obtain the keys to recover the files was to access the database that was left in crooks’ hands. He has forgotten to implement a mechanism to copy the database of the keys of the storage used by the crooks to another archive managed by the researcher.
It is not clear why the hackers behind the Magic ransomware blackmailed Sec, the unique certainty is that that don’t want the Hidden Tear project online. They also offered support to the victims if Sen will remove the Hidden Tear.
Source:http://securityaffairs.co/
A flaw in TeslaCrypt ransomware allows file recovering
The victims of the infamous TeslaCrypt ransomware can now rejoice, there is a free tool to decrypt files encrypted by TeslaCrypt and TeslaCrypt 2.0
TeslaCrypt is one of the most insidious ransomware first detected in the wild in 2015, today I have a good news for its victims.
TeslaCrypt was first detected in February 2015, the ransomware was able to encrypt user data including files associated with video games. In July, a new variant appeared in the wild, TeslaCrypt 2.0, the authors improved the encryption mechanism.
Both strains of the ransomware, TeslaCrypt and TeslaCrypt 2.0, are affected by a security flaw that has been exploited by security experts to develop a free file decryption tool.
The design issue affects the encryption key storage algorithm, the vulnerability has been fixed with the new release TeslaCrypt 3.0 which was improved in a significant way.

The security expert Lawrence Abrams published an interesting blog post detailing the issue, confirming that the decryption tool was available for a while but the news was not disclosed to avoid countermeasures of the malware developers.
Unfortunately, TeslaCrypt 3.0 resolves the issue, then research community decided to release decryption tools in the wild (i.e. TeslaCrack (https://github.com/Googulator/TeslaCrack).
“For a little over a month, researchers and previous victims have been quietly helping TeslaCrypt victims get their files back using a flaw in the TeslaCrypt’s encryption key storage algorithm. The information that the ransomware could be decrypted was being kept quiet so that that the malware developer would not learn about it and fix the flaw. Since the recently released TeslaCrypt 3.0 has fixed this flaw, we have decided to publish the information on how a victim could generate the decryption key for encrypted TeslaCrypt files that have theextensions .ECC, .EZZ, .EXX, .XYZ, .ZZZ,.AAA, .ABC, .CCC, and .VVV. Unfortunately, it is currently not possible to decrypt the newer versions of TeslaCrypt that utilize the .TTT, .XXX, and .MICRO extensions.”wrote Abrams.
As explained in the post, files encrypted with the newer versions of TeslaCrypt are recognizable by the extension (.TTT, .XXX, and .MICRO) and cannot be decrypted.
TeslaCrypt encrypts files with the AES encryption algorithm and uses the same key for both encryption and decryption. Abrams explained that the threat generated a new AES key each time it was restarted, and that it stored the key in the files encrypted during the session. The information about the encrypted key was stored in each encrypted file, fortunately the size of this stored key was vulnerable to decryption through specialized programs. These programs are able to factorize these large numbers, extract their prime numbers and pass them to other specialized tools used to reconstruct the decryption key.
Another interesting tool for decrypting the files is TeslaDecoder, it has been available for decrypting TeslaCrypt files since May 2015 and it has been updated to recover the encryption key for all TeslaCrypt variants.
Source:http://securityaffairs.co/
Hackers Breach University of Virginia HR System
The University of Virginia said on Friday that hackers managed to break into a “component” of an HR system and access sensitive information including W-2s and banking details of University employees.
In a security incident notice, the University said the FBI recently notified the University of a data breach following a law enforcement investigation, which resulted in suspects overseas involved in the incident being taken into custody.
“In collaboration with the FBI, the University confirmed that unauthorized individuals illegally accessed a component of our human resources system, exposing personally identifiable information of a subset of Academic Division employees,” the notice said.
According to the University, the attack came via a phishing email scam by which the attackers sent emails asking recipients to click on a link and provide user names and passwords.
After successfully gaining valid user credentials, the cybercriminals were able to gain access to the HR system and the W-2s of approximately 1,400 employees. Additionally, direct deposit banking information of 40 employees was accessed.
After investigating the incident, it was determined that the attackers gained access to the HR records beginning in early November 2014, with the last suspected intrusion occurring in early February 2015.
Fortunately, the breach affected a small percentage of the 20,000 people employed by the University.
“Phishing attacks have plagued and ravaged institutions for years, and will only escalate in 2016,” Adam Levin, Chairman and Founder of IDT911, told SecurityWeek. “While we don’t have intimate knowledge of the specific security protocols at UVA, it is clear that even if their IT and Information Security departments did everything right, one or more employees who click on a malicious link can be unwitting co-conspirators in the compromise of a database holding the personal information of countless individuals.”
“Even though this was a relatively small breach, the implications to the victims can be very far-reaching,” Paul Martini, CEO of iboss Cybersecurity. “Personal and financial information, like the bank documents and Social Security Numbers stolen in the University of Virginia hack, is very lucrative for hackers to sell on the black market. This is another reminder that even sophisticated networks need to improve their safeguards against data breaches by focusing on stopping malware from stealing information after a hacker has infiltrated the network.”
Source:http://www.securityweek.com/
Kovter Malware Victims Were Secret Zombies in the ProxyGate Proxy Network
Legitimate proxy software distributed with Kovter malware.
During the past few months, computers infected with the Kovter click-fraud malware were also secretly added to the proxy network operated by ProxyGate, the Forcepoint team reports.
Kovter is one of the oldest malware strains around, one that has adapted to fit various needs and niches, and survived mainly as a click-fraud toolkit, ideal for making a quick buck out of online ads.
A recent spam campaign detected by Forcepoint (formerly Raytheon|Websense) has identified Kovter delivered through file attachments in the form of ZIP files.
When uncompressed, these ZIP files automatically execute a JavaScript file which connects to a Web server and downloads the Kovter malware.
In this specific campaign, Forcepoint saw this auto-download process abusing an Alexa Top 10 site, but also downloading two additional payloads besides Kovter.
One of them is the Miuref adware while the second was a legitimate executable, the ProxyGate installer.
All three files were executed as soon as they finished downloading, and silently installed their payloads on the victim’s machine without any type of user interaction needed.

Spam campaign’s author may have participated in ProxyGate’s referral program
It is yet unknown why the malware operators installed the ProxyGate application on the victim’s PC. This application does nothing malicious on its own and is designed to add the user’s computer to ProxyGate’s network of available proxy servers.
A possible explanation for these strange actions may be ProxyGate’s referral programwhich allows users to boost their own account’s number of free proxies available per day.
The spam campaign’s author may possibly be running other malicious campaigns through ProxyGate’s network and wanted to boost his available proxy output IP addresses by secretly abusing ProxyGate’s referral program by packaging the legitimate installer alongside Kovter’s payload.
This is not the first malware campaign that infected users and added their PC to a proxy network. In the past, the Bunitu and the ProxyBack malware families did the same thing.
Users infected with Kovter, may also want to check their computer’s list of installed applications and check to see if they’re not an unwitting zombie in a ProxyGate’s service.
Zcash, an Untraceable Bitcoin Alternative, Launches in Alpha
BITCOIN MAY HAVE become the currency of choice for the anonymity-loving Internet underground. But it’s never been anonymous enough for Zooko Wilcox. As he’ll remind anyone who’ll listen, the blockchain, bitcoin’s very public ledger of all transactions in its crypto-economy, means that unless bitcoin’s users funnel it through intermediaries or special software, their transactions can easily be traced.
Today Wilcox and his startup Zcash are launching the first public alpha release of the cryptography world’s best shot yet at perfectly untraceable digital money. Using a mathematical sleight-of-hand known as a “zero-knowledge proof,” Zcash (until recently known as Zerocoin or Zerocash) offers the same anti-forgery assurances as bitcoin: No one can counterfeit Zcash, or spend the same Zcash “coin” twice. But thanks to its zero-knowledge feature, any spender or receiver can also choose to keep their Zcash payment entirely secret.
The company holds the potential to empower a new form of near-perfect financial privacy—or, put in the terms of less friendly financial regulators, to enable a new form of airtight money laundering. “Consumers want to buy and sell things over the Internet and need privacy from snoops who might use the knowledge of their transactions against them,” says Wilcox, a 41-year-old cryptographer who’s also known in the crypto community for creating Tahoe LAFS, a decentralized, encrypted file-storage system. “This is the first time you can transact with anyone on the Internet, and control over who gets to find out about those transactions is solely in your hands.”

On Wednesday morning Zcash published its source code on Github, and is now allowing anyone to test out the software in what Wilcox calls a “preview.” But in an interview with WIRED he warns that the data moving on the Zcash network doesn’t yet represent actual money, only a “test net” that’s designed to give Zcash a chance to iron out its bugs before anyone makes investments in the cryptocurrency. Wilcox estimates the “real money” launch of Zcash is likely still close to six months away. The prototype version of Zcash that WIRED downloaded still lacked a user interface and instead required figuring out a tough-to-navigate set of command line functions.
Like bitcoin, Zcash’s currency will be created by “mining” computers that compete to solve mathematical problems. But unlike bitcoin and other attempts to create an alternative cryptocurrency or “altcoin,” Zcash is launching as a for-profit company. For its first four years online, a portion of every mined Zcash coin will go directly to Wilcox’s Zcash company and a smaller portion to a non-profit he’s creating to oversee the Zcash code and community longterm. Wilcox says that he plans for 1 percent of Zcash’s currency to ultimately go towards that non-profit, and 10 percent to be paid to the for-profit startup.
That for-profit strategy, Wilcox says, was designed to raise money to fund the project: Much of the 10 percent it earns will repay Wilcox’s investors, whoas of November had put more than $715,000 into Zcash. Those investors include Naval Ravikant, an investor in Twitter and Uber, Barry Silbert, the founder of startup equity-trading platform SecondMarket, and Roger Ver, a staunch libertarian who’s invested in bitcoin startups Blockchain.info and Bitpay, and who also bankrolled much of the legal defense of now-convicted Silk Road creator Ross Ulbricht. (Wilcox says that Zcash remains on the sidelines of the schism over bitcoin’s scalability and speed that’s currently splitting the cryptocurrency community, though he hopes it will be able to integrate any upgrades to bitcoin’s code that solve those issues.)
Plenty of cryptocurrencies that have boasted features bitcoin lacks have launched and languished over the years, without seeing even a fraction of bitcoin’s adoption. But Wilcox argues that Zcash’s incognito properties, when the currency finally does launch for public consumption and real financial applications, will be crucial for those who need a more privacy-preserving form of digital money. That includes anyone from a medical startup trying to comply with healthcare privacy laws to a businesswoman in Afghanistan dodging corrupt cops and tyrannical male family members. “Privacy makes whole societies safer, stronger and more prosperous,” says Wilcox. “Ubiquitous privacy helps prevent corruption and abuse and oppression.”
Of course, the sort of “ubiquitous privacy” that Zcash is designed to allow will no doubt find fans within black markets, too, like the dark web’s $100 million-a-year drug trade. Until now, bitcoin’s lack of connection to banks or registered services has made it a convenient tool to spend money online without necessarily tying that money to the user’s identity. But the blockchain’s privacy problems have remained a nagging threat to anyone who makes a drug deal using bitcoin’s digital cash. Prosecutors proved bitcoin’s shortcomings for narco-money-laundering applications last year, for instance, when they traced $13.4 million from the drug site Silk Road to Ross Ulbricht’s laptop.
Zcash’s untraceability features promise to remove that sort of blockchain analysis as a tool for law enforcement surveillance. That notion has created controversy around the currency since it was first proposed by a team of cryptographers at Johns Hopkins University Back then, the anti-money-laundering think tank Global Financial Integrity published an op-ed in the Baltimore Sun describing the idea as a boon to black markets of all kinds, from human trafficking to wildlife poaching. “More girls will be sold as sex slaves, more rhinos will be poached, and every other large-scale transnational crime that you can name is going to become a lot easier if criminals have a way to transfer very large amounts of money completely anonymously,” wrote the group’s spokesperson E.J. Fagan.
Wilcox maintains his stealthy digital cash startup isn’t intended to facilitate crime, but also notes that the company isn’t liable for any criminal applications for which Zcash is used. “The people who built the first cars weren’t held responsible for car accidents or bank robberies,” he says. “The people who use these tools for good or ill are held responsible for that.”
But Wilcox also insists that Zcash’s legitimate applications will outweigh its shady ones. He compares Zerocoin’s ambiguous potential to that of the Internet itself. “Can the internet be used for crime? Yes, it can be, but that’s not what’s important about it.” Wilcox says. “I’m focused on the trillions of dollars of legitimate commerce that flow around the world.”
Source:http://www.wired.com/
¿Cómo proteger su software o malware contra piratería?
Los hackers hacen la vida difícil, incluso para el usuario de Internet más inocente, y es todo gracias a un pequeño truco desagradable llamada ingeniería inversa. Esto es cuando un hacker toma aparte el código que hace un programa, luego busca las vulnerabilidades o explotaciones. Hay una nueva solución de de seguridad está siendo utilizada para proteger contra la ingeniería inversa del software.
Según los expertos de empresa de pruebas de penetración, cuando se elimina malware de una máquina, se produce el mismo proceso. Con los conocimientos de hacking ético y usando técnicas de la ingeniería inversa los expertos excavan en el código del malware y explotan sus vulnerabilidades en contra de él. Sin embargo, ¿qué pasaría si el malware o software tenga un lógico que podría evitar la ingeniería inversa en el sistema? Según Dave Smith, el profesor del curso de hacking ético, hay una metodología que se llama Hardened Anti-Reverse Engineering System (HARES) y con eso es posible evitar ingeniería inversa.
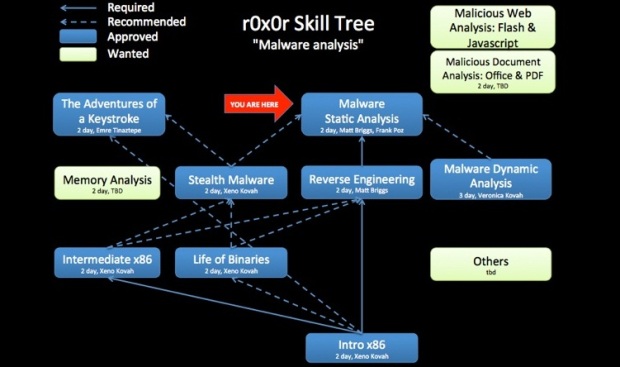
¿Cómo funciona HARES?
Los expertos de empresa de pruebas de penetración explican que, HARES intenta cifrar el código de programa hasta el momento exacto en que procesador necesita para ejecutar el código, lo que significa que no se puede descifrar y analizar el código mientras que el código está siendo ejecutado. Según Dave Smith, el profesor del curso de hacking ético esto se traduce en un código extremadamente protegido de cualquier hacker que quiere piratear el programa y luego averiguar los fallos de seguridad que se podrían utilizar para su propio beneficio.
Para proteger de las herramientas de ingeniería inversa, HARES utiliza un truco de hardware que funciona con chips de Intel y AMD denomina Translation Lookaside Buffer (or TLB) Split. Eso TLB Split separa la parte de la memoria de una computadora que almacena los datos de programa de la parte donde se almacenan las instrucciones. Todos los partes de la memoria de las instrucciones está encriptado de tal manera que sólo puede ser descifrado con una clave que reside en el procesador de la computadora. Cuando una herramienta de ingeniería inversa lee la memoria de la computadora para encontrar las instrucciones del programa, la división TLB redirige la herramienta a la sección de la memoria que está llena de comandos encriptados, ilegibles mencionan expertos de empresa de pruebas de penetración.
Las protecciones proporcionadas por HARES son: el aumento de la protección de código de un programa contra el análisis estático y significativamente difícil análisis dinámica. Estas protecciones pueden ayudar a prevenir algoritmos sensibles de ser invertidos, así como proteger una aplicación vulnerable contra ciertos tipos de explotaciones.
Según experiencia de empresa de pruebas de penetración, el resultado es una protección resistente al crack de cualquier hacker que le piratean el software, encontrar fallos de seguridad que podrían comprometer a los usuarios e incluso en algunos casos entender sus funciones básicas.
Por supuesto, cualquier herramienta que puede ser usada para el bien de la seguridad cibernética también podría ser usada por hackers para crear malware que son muy difíciles de descifrar y ser analizados. Pueden aprender más sobre HARES durante el curso de hacking ético de IICS.
Cyber attacks on industrial Internet of Things are on the rise
The United States government has revealed that it has detected a rise in cyber criminal attacks on industrial control systems.
The concern is that with leading manufactures and grid power producers’ early adoption of the industrial internet of things — and Industry 4.0 which are commercial and industry versions of the Internet of Things — sufficient safeguards have not been put in place to protect them from the internet.
Previously, these industrial companies had systems that were securely locked down and not connected or accessible to the outside world. The Industrial internet of Things (IIoT) has changed all that though, with companies embracing the internet to leverage remote control and management on a global basis.

There is also the new commercial and business model of utilizing big data collection and analytics, which requires cloud storage and internet access. However, opening up industrial and commercial systems to the Internet has also opened doors to potential attacks.
Not only is the potential scale of attacks far larger from an internet scale perspective, most industrial IT firms do not have the battle hardened skills of dealing with web scale attacks as they are accustomed to dealing with a fortress approach to IT security.
“We see more and more that are gaining access to that control system layer”, said Marty Edwards, who runs the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team, or ICS-CERT. “I am very dismayed at the accessibility of some of these networks… they are just hanging right off the tubes”.
Dave Palmer, director of Technology at Darktrace also commented: “This marks a dangerous and long predicted shift in the targets of hackers where industrial control systems and basic infrastructure is at risk in addition to the banking and credit card attacks we are used to hearing about”.
“If attacks move beyond intellectual property theft and intelligence collection to disrupting or destroying critical infrastructure then, more than ever, organizations within this sector really need to ensure that they have the right strategies and immune systems in place to detect emerging threats and respond to them before a crisis occurs”, adds Palmer.
Published under license from ITProPortal.com, a Net Communities Ltd Publication. All rights reserved.
Source:http://betanews.com/
Hacker reveals why he hacked UGA calendar and wrote “Get Ass Kicked by GT”
Hacker of UGA calendar pays price for ‘Greatest prank ever’, made to do community service. Ryan Gregory Pickren, a Georgia Tech student who had hacked University of Georgia computers and added an event that read “Get Ass Kicked by GT,” to the UGA master calendar two days before the annual football matchup in 2014 has announced that the charges against him have been dropped.
Pricken has today cleared his name from all charges through community service. “Today all of the charges regarding my incident with the University of Georgia have officially been dismissed,” he posted on his Facebook site Thursday. “I would like to take a moment to tell my story about how I ended up in a jail cell Christmas 2014.”

Pickren, a computer engineering major, “became desensitized to the impact that a computer breach could have on organizations. But I was about to learn the hard way that not all “research” ends with cash rewards and free merchandise,” he wrote.
Explaining how and why he posted what he did on his Facebook page, he said, “While sitting in my room waiting for Thanksgiving dinner, I decided that I was going to play a prank. I pulled up the University of Georgia’s homepage and started poking around. A few minutes later I stumbled upon their master calendar for campus events. I will spare you the technical details, but I had a hunch that I could circumvent their approval process by carefully forming an HTTP POST request.”
“In shock that it actually worked, I ran downstairs to show my parents what I had done,” Pickren continued. “I informed them that IT departments these days would find it funny and that the university expects pranks this time of year. My family laughed and gave me high fives.”
Later that night, an ESPN reporter discovered it and wrote about it. The prank received media attention that quickly spread from just ESPN to outlets across the Internet and the Southeast. An investigation was launched by UGA’s police department, who a few weeks later charged him with felony computer trespass for finding what Pricken done was illegal.
He was given a legal diversion that would keep him out of jail and drop charges in return for community service, an apology and keeping his nose clean. Pickren served Atlanta non-profits, helping them safeguard their websites against hacks.
It however did not impress legal authorities in Athens that his addition to the calendar was true. Georgia Tech beat UGA 30-24.
Pickren spent Christmas Eve 2014 in a jail cell, but ultimately begged out of the charges into pre-trial diversion and finished compulsory community service.
Currently, Pickren is still a Georgia Tech student and is expected to graduate with a degree in computer engineering.
Source:http://www.techworm.net/
Fifth Version of Tinba Trojan Expands to Target Asian Banks
Tinba is a well-known banking trojan that has been wreaking havoc among users in the past five years, ever since its source code was leaked online.
Through time, the trojan, also known as Tinybanker, Zusy or HµNT€R$, has had four major versions. In a report from F5 Labs, the cyber security vendor is announcing a fifth version, one that has received special updates so it can target banks from the APAC (Asia-Pacific) region, a territory in which Tinba hasn’t been very active until now.

This fifth version, named Tinbapore, doesn’t differ too much from the previous versions and still works in the same way.
It infects users through spam, it goes on to gain boot persistence via a rootkit, it initiates conversations with a C&C server after scanning and collecting data from the victim, and then goes on to hijack the user’s browsers.
Whenever the user accesses a Web-based banking portal or Web-based payments system, the malware will use Web injection techniques to insert malicious JavaScript code in the page, and collect the user’s credentials and other financial information. This data is later used for making fraudulent transactions.
More than half of Tinbapore infections were recorded in the APAC region
Differences from previous versions include the usage of a domain name generation algorithm that makes it harder for security researchers to track down its C&C, and its own separate explorer.exe process that runs in the operating system’s background.
According to F5 researchers, the campaign responsible for spreading this most recent version of Tinba is originating from Russian domain names.
Furthermore, most of its targets are located in Singapore, the country from whose name Tinbapore’s moniker was derived. Second to Signapore’s 30% we find Indonesia with 20%, another APAC country, and also Malaysia with 5%.
“Financial institutions in APAC are not the only ones at risk; the malware has also targeted institutions in the Europe, Middle East, and Africa (EMEA) region and the Americas,” F5 researchers reveal. “However, it is clear that the majority of attacks target financial institutions in Asia and the Pacific.”
The full Tinbapore: Millions of Dollars at Risk is available for download.
SlemBunk Android Banking Trojan Continues to Wreak Havoc Around the World
One month later, the SlemBunk Android banking trojan is still going strong, FireEye researchers confirming that despite its activities being made public, the malware’s operators have continued to infect users and steal their financial information.
SlemBunk, first discovered by FortiNet last year, has intensified its activities towards the middle of December 2015 when FireEye researchers saw a spike in activity.
The banking trojan managed to infect users all over the world, targeting 33 mobile banking applications via 170 different SlemBunk variants.

For most of these infections, SlemBunk was offered to its victims as an Android version of the Adobe Flash Player on adult-themed video portals where access to videos was blocked because users didn’t have their “Flash Player up to date.”
According to FireEye, this campaign has suffered very little modifications after they dissected the SlemBunk’s malware mode of operation.
SlemBunk campaign carried on unabated
Following through on their previous work, security researchers continued to monitor SlemBunk infections and discovered that before the banking trojan lands on the users’ devices, up to three intermediary apps are used to mask the final infection.
This prolonged attack chain usually starts with a drive-by download attack that automatically starts a download for the SlemBunk dropper (dropper – malware that serves to initially penetrate systems), which unpacks another app that serves as the SlemBunk downloader (downloader – malware that downloads other malware), which in turn downloads the final SlemBunk payload (the actual banking trojan).
Additionally, besides the fake Flash Player app, FireEye researchers also identified SlemBunk posing as other types of apps as well, from essential tools to adult-themed apps, and all distributed from sources outside the Play Store.
The researchers identified the campaigns’ CnC server, even reaching its login page. Most of these domains were registered at the start of December 2015, but their operators already abandoned them and moved to new ones. As it stands now, SlemBunk’s operators don’t seem to look scared or threatened by the security firm’s discoveries, being always one step ahead.

$30 webcam spun into persistent network backdoor
Bring on the Internet of dangerously hacked things. Vectra Networks security wonks have spun a cheap webcam into a backdoor to persistently p0wn PCs.
The junk hacking expedition led Vectra’s chief security chap Gunter Ollman into the internals of the D-Link DCS 930L, a network camera that can be had for US$30.
The attacks are useful as an alternative backdoor for targeted attackers who already have access to a machine, or for those capable of compromising a device before it is installed by the user.

It is not something users should expect to surface in the wild and is rather an example of the risks posed by internet-of-things devices.
Ollman dumped and reflashed the camera’s firmware so that it opened a remote backdoor that was difficult to detect and did not affect normal operation.
The update feature was also removed, preventing the backdoor from being lost through patches.
“The irony in this particular scenario is that WiFi cameras are typically deployed to enhance an organisation’s physical security, yet they can easily become a network security vulnerability by allowing attackers to enter and steal information without detection,” Ollmann says.
“Consumer-grade internet-of-things products can be easily manipulated by an attacker, used to steal an organisation’s private information, and go undetected by traditional security solutions.
“While many of these devices are low-value in terms of hard costs, they can affect the security and integrity of the network, and teams need to keep an eye on them to reveal any signs of malicious behaviour.”
D-Link has not fixed the vulnerability but researchers do not expect a patch will be forthcoming. A fix would require a Trusted Platform Module or specialised chip to verify software updates.
Hardware analysis complete with Leatherman-sliced hand is available for engineer’s viewing pleasure.
Trend Micro Password Manager Discloses Passwords via Leaky Node.js Server
Google’s Project Zero researcher, Tavis Ormandy, has yet again discovered a security bug in one of the world’s leading antivirus engines, this time in Trend Micro’s Antivirus for Windows.
According to Mr. Ormandy’s findings, when installing the Trend Micro Antivirus for Windows, the company’s Password Manager application, which comes bundled with the main antivirus, is also installed.
The application, used as a side feature to the main antivirus, is used to store passwords and works just like any other password manager application.
Trend Micro’s Password Manager is written mainly in JavaScript, and it works by starting a Node.js server on the local computer every time the main antivirus starts.
RCE bug allows total system compromise
As Mr. Ormandy discovered, this server opens multiple HTTP RPC ports for handling API requests coming from other applications querying or interacting with information stored in Trend Micro’s Password Manager.
Available at “http://localhost:49155/api/”, Mr. Ormandy discovered that attackers could craft malicious links that, when clicked by a user that has a Trend Micro antivirus installed, would allow a malicious party to execute arbitrary code on the local computer.
Depending on the hacker’s skill level, various level of attacks can be carried out via this entry point.
Besides reporting the issue to Trend Micro’s team and helping them create a patch for this issue, Mr. Ormandy also discovered that the Trend Micro Password Manager also exposes around 70 APIs through this same Node.js server.
Leaky Password Manager is leaky
During his research, he was able to steal encrypted passwords from the password manager application, expose the domains for each encrypted password entry, and also decrypt passwords, using one of the exposed Node.js APIs, responsible for decrypting passwords inside the Password Manager application itself.
Theoretically, an attacker could create a malicious link that chained all these exploits. The attacker would only have to send this malicious link via email, or embed it in a Web page, which if clicked by a Trend Micro user would steal all his passwords and send them to a remote server, under the attacker’s control.
No details were given about which Trend Micro Antivirus and Password Manager versions were vulnerable, but a new release has been put out to fix these flaws, so just update your Trend Micro Antivirus to the latest version.
Previously, Mr. Ormandy has discovered security issues in other antivirus engines like AVG,FireEye, Kaspersky, Avast, and ESET.
UPDATE: Trend Micro has published a response to the recent vulnerability disclosure.

Cryptography Guru Announces Anonymous Communications Network Called PrivaTegrity
David Chaum, the father of many encryption protocols, has revealed a new anonymity network concept that aims to fix many of Tor’s current problems, both in the legal and technical department.
Many scientists have tried to fix Tor in the past with concepts like I2P, HORNET or Vuvuzela. David Chaum’s advantage is the fact that the Tor Project actually copied his work in the past, implementing an evolved version of one of his anonymity protocols called Mix Network, also used by Bitcoin’s creators.
Mix Network (sometimes called Mixing Network) relies on encrypting data in layers as it passes through intermediary servers. The concept was first published in 1979 and was later used as the basis for the Onion protocol, on which the Tor network was built.
This past Wednesday, on January 6, 2016, Mr. Chaum presented himself at the Real World Cryptography Conference in Stanford, where he revealed a project on which he had worked for the past two years alongside other cryptography experts from four universities in the US, UK, and Holland.
His paper, called “cMix: Anonymization by High-Performance Scalable Mixing,” presents an evolution of the Mix Network concept, called cMix, which took into account Tor’s advancements, but also addressed some of the issues governments and regular users had with its implementation. The researchers plan to use this new cryptography protocol to build their own, more secure PrivaTegrity network, as an alternative to Tor.
An incredibly simplified explanation of cMix
According to their research paper (page 1 – Section I, and page 4 – Chapter III-D), for each communications path established in a cMix network, the message sender creates connections with a series of trusted servers, with which it shares a series of keys.
When the sender sends out a message, its data is multiplied with all the keys. As the message passes through each server, it is divided with each server’s corresponding key, but also multiplied again by a random number. Messages are then stored randomized in each server’s buffer.
When the data needs to be retrieved and sent to the receiver, each server will retrieve the message from its random position, divide out the random numbers, and then multiply it with the recipient’s keys.
When the data arrives on the recipient’s computer, their keys are used to divide the data and decrypt the message.

Better anonymity than on Tor
According to Mr. Chaum, by moving most of the computational operations to the server, instead of the client, cMix achieves the same transfer speeds as Tor, but unlike its predecessor, it is not vulnerable to a series of “tagging” attacks.
Tagging attacks rely on compromising Tor nodes, which on their own allow attackers to tag input slots with their output location. By using cMix’s setup, the protocol is not vulnerable to these type of attacks, unless the malicious entity compromises all nodes that participated in the encryption process.
Additionally, researchers said that, in PrivaTegrity, tagging attacks are also blocked by how users set up keys with network nodes.
“PrivaTegrity aims to provide privacy at a technical level that is not penetrable by nation states,” the researchers claim. “PrivaTegrity implements a new approach to user identification requiring each user to provide a small but different type of identifying information to each mix node.”
But…
This identification may include anything from passphrases to images, from phone numbers to email addresses. “A user reveals comparatively little to any single node, but collectively the nodes possess significant identifying information,” researchers revealed.
While its encryption protocol is incredibly strong, the researchers also said that data about users is not 100% anonymous.
In an interview with Wired, Mr. Chaum revealed that, to prevent cybercrime and other nefarious groups from using their network, the researchers behind this initiative are planning to create a PrivaTegrity Council.
This council will provide access to data about users to law enforcement, but only for those who use the network for criminal activities. This council will have nine members from across the world, and all have to agree to release information about users to any government inquiring for data.
With the rising trend of government requesting backdoors to encryption protocols, Chaum and his associates are trying to move the backdoor from the hands of governments to an international council.
While technically as fast as Tor and even more secure from third-party attacks, admitting that a group of nine people get to play judge over your anonymity may deter users from embracing PrivaTegrity.
Currently, Chaum and his team are working on a smartphone IM app to test their PrivaTegrity network.
Source:http://news.softpedia.com/
EZCast TV Streaming Dongle Blows Up Your Home Network’s Security
EZCast device may be fun but fails in terms of security.
A Chromecast-like TV streaming device manufactured by EZCast comes with a few security flaws that allow attackers access to a user’s home network.
EZCast devices are HDMI-based TV dongles that can be connected to any regular TV and transform it into a smart appliance. The stick contains all the necessary brain power to allow apps to run on the device, and stream audio and video files from the local network or the Internet.
Check Point security researcher Kasif Dekel discovered bugs in the EZCast device’s firmware, flaws that the manufacturer failed to address, even after Check Pointed contacted them.

EZCast has weak passwords, susceptible to brute-force attacks
According to Mr. Dekel, the first major issue he saw is that the device created its own WiFi network to allow the user to connect various devices (laptops, desktops, mobiles) to the dongle and start streaming content.
The issue was the fact that this WiFi network was only protected by an 8-digit password. The device had no protection against brute-force attacks, and Mr. Kessel successfully cracked a dongle’s WiFi password.
Additionally, using simple social engineering tricks, the researcher also created malicious links, which could be sent to the user via Skype or Facebook messages. If these messages were opened from the TV, while surfing the Web via their EZCast, the attacker would also gain access to the dongle’s network.
If the dongle is connected to your TV, it doesn’t mean your PC is safe
Giving an attacker access to the dongle’s network would also grant them access to any laptop or mobile connected to that network, and indirectly to all the data hosted on them.
According to Google statistics, the EZCast device has about 5 million users.
“The EZCast device was never designed with security in mind. We were able to uncover a number of critical vulnerabilities, and we barely scratched the surface,” Check Point researchers say. “Would you sell a root shell in your network for $25 dollars? Because that’s what you’re essentially doing when you buy and use this device.”
After he was all done, Mr. Dekel found 2 remote code execution vulnerabilities, 1 command injection, and 1 unrestricted file upload flaw, with some flaws allowing execution of code as the root user.

EU Cookie Law Notification Abused to Hijack Clicks for Invisible Ads
Did you click on a cookie notification, or was that an ad?. Cyber-crooks have come up with a new way to fool users into clicking on ads instead of letting them access a website’s content, and this method relies on the EU Cookie Law notification.
In May 2011, the European Parliament adopted an EU Directive which said that individuals have the right to refuse the use of cookies, and so, website operators should show a notification on their sites to inform users if and how cookies are used.
Since then, all Internet users have come accustomed to these cookie usage notifications, some sites showing them to all visitors, not just those coming from European countries.

New clickjacking technique is hard to spot with the naked eye
According to cyber-security vendor Malwarebytes, a group of cybercrooks have found a way to abuse these innocent-looking notifications, tricking users into clicking on a hidden ad instead.
The scam is simple and quite ingenious. When accessing a website, a cookie usage notification is shown in the middle of a page inside a popup.
What users don’t know is that on top of this popup, the scammers also load an iframe with a Google ad inside. They then use the CSS property “opacity: 0” to make the ad invisible, letting the underneath notification show through.
The technique can also be used for malvertising campaigns
The ad is still there, but naked to the human eye. When the user clicks on any of the cookie notification’s buttons, he’s unwittingly clicking the ad, generating profits for the scammers, and redirecting the user to the ad’s target URL.
While this campaign is quite harmless in its current form, since it shows safe ads from legitimate companies, the trick behind it can easily be used to display malicious ads instead, cleverly redirecting users to dangerous Web pages where exploit kits infect users with malware.
Something tells us this isn’t the last time we hear about EU Cookie Law notifications being abused.

Source:http://news.softpedia.com/
Security experts disclosed SCADAPASS, a list of default credentials for ICS and SCADA systems
Security experts from SCADA StrangeLove group disclosed SCADAPASS, a list of default credentials for ICS and SCADA systems.
Recently I wrote about the SCADA StrangeLove research team reporting their study on the level of cyber security implemented in modern railroad systems .
Now the SCADA StrangeLove group has published a list of default credentials, dubbed “SCADAPASS,” associated with industrial control system (ICS) products from various vendors.
The list includes default credentials for more than 100 products, and experts hope that the security community will add new entries to the database in the incoming months. Each record of the database includes the name of the affected ICS/SCADA product, the type of device, the vendor’s name, default credentials (usernames and passwords), the port and protocol over which the device can be accessed, and the source of the information.

The SCADAPASS list includes default credentials for a number of industrial devices such as wireless gateways, routers, programmable logic controllers (PLC), servers and network modules.
The default passwords have been obtained from open sources which include documentation from the vendor and other reports from various industries.
The devices are manufactured by the most important vendors for industrial components, including ABB, B&B Electronics, Digi, Emerson, eWON, Hirschmann, Moxa, Netcomm Wireless, Rockwell Automation /Allen-Bradley, Samsung, Schneider Electric, Phoenix Contact, Tridium, Wago, Siemens and Yokogawa.
According to SecurityWeek, the SCADA StrangeLove group has also compiled a list containing hardcoded passwords of many industrial devices. The experts will not disclose this second list to avoid threat actors will exploit it in cyber attacks in the wild.
These hardcoded passwords can only be removed by applying a patch from the vendor.
The availability of a list of default passwords for SCADA systems represents a serious issue and experts published it to sensibilize the operators of industrial systems and ICS vendors.
Security experts speculate ICS vendors should implement security by design, implementing security controls to mitigate cyber threats.
Source:http://securityaffairs.co/
Hardsploit: Una herramienta como Metasploit para hacking del hardware
Adopción de Internet de las cosas (IoT) está ganando impulso, y escuchamos muchas veces que será el desafío más grande implementar seguridad en IoT. Una empresa de seguridad informática ha salido con una herramienta que permitirá a los auditores de seguridad informática de IoT, dispositivo industrial, sistemas SCADA y productos electrónicos básicos utilizados en la vida cotidiana. Se llama HardSploit y es un marco modular de hardware y software destinado a facilitar una opción por auditoría de los sistemas electrónicos, a los consultores de hacking ético. En resumen, es una herramienta de hardware hacking.
Módulos de Hardsploit permiten expertos de empresa de seguridad informática interceptar los datos, hacer pruebas, reproducción y enviar datos a través de cada tipo de bus electrónico utilizado por el dispositivo probado. El nivel de interacción que expertos de empresa de seguridad informática tendrán depende de las características del bus electrónico, menciona el experto de hacking ético.
Hardsploit es una herramienta con software y los elementos electrónicos. Es una plataforma técnica y modular (usando FPGA) para realizar pruebas de seguridad en las interfaces de comunicaciones electrónicas de dispositivos integrados.
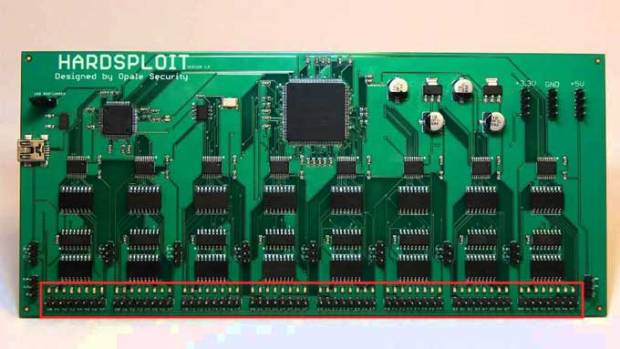
Módulos de Hardsploit
Las principales funciones de auditoría de hacking ético de dispositivos integrados son:
- Sniffer, escáner, Proxy, interactuarcon el buselectrónico
- Dump de Memoria
- Exploits
Módulos de HardSploit ‘s le permiten analizar toda clase de bus electrónico (tipo serie y paralelo)
- JTAG, SPI, I2C
- Direcciónparaleloybus de datosen el chip
- yotros máspor veniren el futuro (OneWire, UART, etc…)
Función visual de ayuda para cablear
Los expertos de empresa de seguridad informática, no deben preocupar con parte de las pruebas de hacking ético de dispositivos integrados. Los expertos de empresa de seguridad informática sabrán donde tiene que conectar los cables y cómo conectarlas con la ayuda de función visual de ayuda para cablear. Este módulo ayuda en conexión de los cables con el dispositivo probado:
- GUI guía la organización de pin (pin OUT) del chip de dispositivo probado.
- GUI le guía durante todo el proceso de cableado entre conector de Hardsploit y el dispositivo probado.
- GUI controla un conjunto de LED que se encienden y se apagan y permiten encontrar el Hardsploit Pin para conectar con el dispositivo probado.
GUI y software asociado
La parte del software de Hardsploit ayuda a llevar a cabo una auditoría de hacking ético de extremo a extremo. Será compatible (integrado) con las herramientas existentes, como Metasploit. Existen API’s para la integración con otras API en el futuro.
HardSploit pretende convertirse en una herramienta de auditoría de hacking ético para la seguridad de Internet de las cosas y Hardware. Pueden aprender más sobre hacking de hardware en el curso de hacking ético de IICS.
Google Patches Android for Yet Another RCE Flaw in Its Mediaserver Component
Google patches RCE flaw in Mediaserver five months in a row. Google has just released the changelog of its most recent Android security bulletin, in which it fixed 12 bugs, five of which were labeled as of critical severity.
Ever since Google announced and started offering monthly security updates for Android, the company has been patching an RCE (Remote Code Execution) critical bug in its Mediaserver component every month. It did so in September (CVE-2015-3864), in October(15 bugs in libstagefright, part of Mediaserver), in November (CVE-2015-6608), December(CVE-2015-6616), and now in January (CVE-2015-6636).

Some (smart) users might say that it’s time for Google to rethink its Mediaserver component, especially since it was the origin point of the first two Stagefright vulnerabilities that affected over one billion devices, first in August, then in October.
Of course, bugs are often found in software products, but not with the frequency and severity at which security researchers are finding them in Android’s Mediaserver.
Since Google has announced plans to migrate Android’s code from Java to OpenJDK, this might be the perfect time to do so.
Latest Mediaserver RCE has shades of Stagerfight
This most recent issue affects only devices running Android 5.0 or higher, and Google says that “the affected functionality is provided as a core part of the operating system and there are multiple applications that allow it to be reached with remote content, most notably MMS and browser playback of media.”
This means that, just like in Stagefright’s case, an attacker can craft a malicious image, audio, or video file, and send it via an MMS or stream via the user’s browser.
When this happens, exploiting a memory corruption bug, attackers can execute remote code on the device. Based on their skills in working with loopholes in Android’s system, they could take control of targeted devices.
Google’s own security researchers discovered this flaw, and the company said that it had not seen any attacks exploiting this new Mediaserver vulnerability. Below is the complete list of patched Android security issues.
| Issue | CVE | Severity |
|---|---|---|
| Remote Code Execution Vulnerability in Mediaserver | CVE-2015-6636 | Critical |
| Elevation of Privilege Vulnerability in misc-sd driver | CVE-2015-6637 | Critical |
| Elevation of Privilege Vulnerability in the Imagination Technologies driver | CVE-2015-6638 | Critical |
| Elevation of Privilege Vulnerabilities in Trustzone | CVE-2015-6639 | Critical |
| Elevation of Privilege Vulnerability in Kernel | CVE-2015-6640 | Critical |
| Elevation of Privilege Vulnerability in Bluetooth | CVE-2015-6641 | High |
| Information Disclosure Vulnerability in Kernel | CVE-2015-6642 | High |
| Elevation of Privilege Vulnerability in Setup Wizard | CVE-2015-6643 | Moderate |
| Elevation of Privilege Vulnerability in Wi-Fi | CVE-2015-5310 | Moderate |
| Information Disclosure Vulnerability in Bouncy Castle | CVE-2015-6644 | Moderate |
| Denial of Service Vulnerability in SyncManager | CVE-2015-6645 | Moderate |
| Attack Surface Reduction for Nexus Kernels | CVE-2015-6646 | Moderate |

