trojan
Carbanak Banking Trojan Returns with a New Series of Attacks
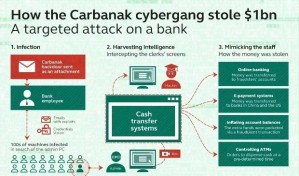
The Carbanak banking trojan was spotted once again in attacks on financial institutions and businesses across the globe, as CSIS is reporting.
Carbanak, also known as Anunak, was previously discovered and analyzed by Russian-based Kaspersky Lab security firm, in February 2015.
Back then, Kaspersky Lab was estimating that the group behind Carbanak infiltrated up to 100 financial institutions worldwide, gaining control over their computers, and stealing around $1 billion / €876.7 million.
Since then, the trojan has been making sporadic returns, always changing one small detail in its operation to keep up with firewall and antivirus updates.
New Carbanak variant uses a new proprietary communications protocol
As the CSIS team is now reporting, a new variant of the trojan has been observed in the wild, targeting the same kind of financial corporations as before.
This version of Carbanak is different from the original, using a predefined IP address instead of random generated domains to talk to the C&C server, employing random generated file names, and featuring a new proprietary protocol for managing its plugins and internal communications.
Just as before, Carbanak still hides in an infected svchost.exe process, keeps its modular structure that allows it to shape shift and adapt to victims, and continues to use a legitimate code-signing certificate to avoid detection.
According to CSIS, this new version of Carbanak uses a code-signing certificate issued by Comodo, to what appears to be a legal Russian-based business.
Carbanak continues to brazenly flaunt its Russian connection
Security researchers believe the criminals behind Carbanak have registered a real company with the sole purpose of having a legal base for some of their fraudulent transactions.
“Carbanak-related transfers are rather huge,” says the CSIS team. “Possibly, they have registered a company and opened bank accounts in order to receive their stolen money while having full control of the transferring process.”
Previously ESET researchers found a version of Carbanak using stolen certificates belonging to companies Moscow-based companies Stroi-Tekh-Sever, Flash, OOO “Techcom” and Torg-Group.
The Russian connection for the Carbanak trojan is very well known, Trend Micro researchers previously linking one of its C&C servers to an IP owned by the Russian Security Service (FSB).
Source:http://news.softpedia.com/
Poweliks Trojan goes fileless to evade detection and removal
A recently-discovered Trojan in the wild does not exist as a detectable files on compromised PCs to stay hidden under the radar as it generates ad-click revenue for hackers.
The Poweliks Trojan has been in a constant state of evolution to avoid detection by today’s antivirus systems. First discovered in 2014, the Trojan now uses interesting techniques to infect and stay undetected on victim systems — such as staying fileless.
Explored by Symantec researchers and explained in a blog post Tuesday, the malware, used to generate revenue for cyberattacks through ad-click fraud, is now a registry-based threat which resides only in Windows registries — and with no files to speak of and persistence mechanisms which allow the malware to stay on a PC even after a restart.
Poweliks is considered a “fileless” threat which uses a variety of techniques in order to exist only in a Windows registry. Security researchers from Symantec say Poweliks “stands out from crowd” due to a persistence mechanism which involves the use of a legitimate Windowsrundll32.exe file to execute Javascript code embedded within the registry subkey itself. The code reads additional data from the registry, acting as a payload before execution. Some of this data is encoded, and after execution what is called a “Watchdog process” is installed.
A Watchdog process is used to make sure the malware is still operating. If Poweliks is no longer running and the malware’s registry subkeys have been deleted, the process reinstates the subkeys.
In order to keep Poweliks running, Watchdog changes access rights to prevent access and uses unprintable characters so the keys can be hidden, according to the firm.

In addition, Symantec says the Microsoft Windows Remote Privilege Escalation Vulnerability (CVE-2015-0016) may be exploited by the Trojan in order to wrestle control of a compromised computer. The vulnerability has been patched on up-to-date systems, but those who have not patched their systems are vulnerable.
The security team says:
“Trojan.Bedep also used this zero-day exploit to take control of compromised computers and it did this around the same time that Poweliks was exploiting the vulnerability. This led us to recognize that there could be a connection between Poweliks and Bedep.
Bedep is a downloader and one of the threats it often downloads onto compromised computers is Poweliks.”
Despite the sophisticated techniques Poweliks uses to stay lurking undetected on computer systems, the malware is ultimately still just a click-fraud Trojan used to generate money through fraud. The Trojan requests adverts based on keywords, manipulates searches to make them seem like legitimate user requests, and browses to the URL returned by the ad network by the search. This, in turn, allows the threat actor to earn money based on click rates.
However, these adverts are not shown to victims, so they remain unaware of the infection for longer. The adverts themselves are not such a problem in comparison to the vast amount of adverts Poweliks sends to victims, which can reach up to 3,000 per day according to the security team.
As a result, this high influx of ads can end up clogging up victim machines, hogging memory and can also provide a tunnel for additional malware to be downloaded.
For example, Poweliks can provide a conduit for ransomware to be downloaded, which can end up with a computer being locked, its files encrypted and the victim receiving a demand for money to unlock their PC.
Source:http://www.zdnet.com/
Vawtrak Banking Malware Hides Its Servers in Tor
Some variants of Vawtrak banking Trojan, also known as Neverquest, have been found to hide their command and control (C&C) servers in Tor anonymity network, making the cybercriminal operation more difficult to disrupt.
Most versions of the malware rely on hard-coded IP addresses for the C&C, but this approach makes the domains used to deliver commands to the infected machine easy to discover via threat analysis techniques.
DGA is not foolproof
A different mechanism for making Vawtrak more resilient to takedown efforts involves a domain generation algorithm, which creates a set of domain names the malware contacts to receive commands.
Cybercriminals register only a small number of them because Vawtrak will check each of them until the appropriate response is received.
Raul Alvarez from Fortinet explains how the process works for this piece of malware, saying that Vawtrak’s code includes multiple DWORD values matching different domain names.

“Each DWORD value is a seed used to generate the domain name. These seeds are stored as fixed values within the malware code, thereby producing the same pseudo-randomized domain names. To generate the corresponding domain name, Vawtrak uses the seed to generate the pseudo-randomized characters of the domain name,” he says in a blog post.
However, this technique is not infallible because researchers can break the algorithm and find the strings generated.
Tor2Web proxy used to access hidden services
More recent variants of the threat rely on Tor2Web, a proxy that establishes a direct connection to a server in Tor network without the need for additional tools.
The strings generated by the DGA are for locations in Tor, and the author implemented a function that passes them through the Tor2Web proxy service.
Although a user connecting to the proxy service can be traced, the connection beyond it is not. Traffic in Tor is encrypted and routed through multiple machines that do not keep records of the origin and destination. The result is access to a server whose location is shrouded in anonymity.
Vawtrak includes multiple protection mechanisms (such as disabling antivirus solutions) that allow it to evade detection and analysis. After compromising a machine, it can pilfer credentials and record user activity (keystrokes, screenshots and video).
Its operator can access the system remotely through a VNC channel and alter web sessions by injecting fake content in order to collect passwords for online banking accounts and the additional codes needed to access them.
Source:http://news.softpedia.com/
High-level, state-sponsored Naikon hackers exposed
The activities of yet another long-running apparently state-sponsored hacking crew have finally been exposed.
The Naikon cyber-espionage group has been targeting government, military and civil organisations around the South China Sea for at least five years, according to researchers at Kaspersky Lab.
The Naikon attackers appear to be Chinese-speaking and chiefly interested in top-level government agencies and civil and military organisations in countries such as the Philippines, Malaysia, Cambodia, Indonesia, Vietnam, Myanmar, Singapore, and Nepal.
The group relies on standard cyber-spy tactics: custom malware and spear phishing featuring emails carrying attachments designed to be of interest to the potential victim. This attachment might look like a Word document, but is in fact an executable file with a double extension.

Naikon has developed platform-independent code and the ability to intercept the entire network traffic, marking them out as more capable than the norm.
The remote access trojan routinely used by the crew comes with 48 commands, including instructions for downloading and uploading data, installing add-on modules or working with the command line.
Each target country has a designated human operator, whose job it is to take advantage of cultural aspects of the country, such as a tendency to use personal email accounts for work.
As well as this social engineering to fine-tune targeting, the group also routinely places its hacking command and control infrastructure (a proxy server) within the country’s borders to facilitate real-time connections and data exfiltration.
The tactic means that suspicious traffic is not travelling outside a target’s country and is therefore less likely to be flagged as potentially dodgy and subjected to further scrutiny.
“The criminals behind the Naikon attacks managed to devise a very flexible infrastructure that can be set up in any target country, with information tunnelling from victim systems to the command centre,” explained Kurt Baumgartner, principal security researcher at Kaspersky Lab. “If the attackers then decide to hunt down another target in another country, they could simply set up a new connection. Having dedicated operators focused on their own particular set of targets also makes things easy for the Naikon espionage group.”
The Naikon crew recently locked horns with Hellsing, another cyberspy group. The incident prompted Kaspersky Lab researchers, who were already looking into Hellsing, to cast their attention towards Naikon.