Malware
TECHNICAL TEARDOWN: MAYBANK PHISHING MALWARE – PART 1
Recently, Jacob discovered 2 interesting phishing websites,http://maybankk2u%5Bdot%5Dcom and http://maybank2u-my%5Bdot%5DcomThis 2 websites had the same identical codes and come with a malware in it.
The malware that we discovered is a file infector virus. It scans the system for .html files, .exe and autorun.inf and insert malicious codes into the files.
[ Sample used in the analysis ]
MD5: 44A604F9D96368A83DF55E19644321D3
SHA1: CDBF41310DAE6EFF1127BB92A217369FD2F90B37896568D4F34528AC20468B5C
Malware Sample: index page
Password is “infected29A”
[Backdoor Analysis]
A brief high level overview of the malware infection process flow.

Figure 1 – Infection process
[ Initial Exploitation ]
The backdoor was dropped onto victims’ machine via a malicious VBScript in phishing home page.

Figure 2 – Maybank Phishing homepage
[ VBScript analysis ]
Scrolling down the html source of the webpage, you will come across a large chunk of alphanumeric text. If you look closer at the start of this large chunk of text, you will see the hexadecimal “0x5A4D” which stands for MZ in ascii. Files that start with a MZ header suggests that it is a PE file. You may refer to the following website http://wiki.osdev.org/PE for more information about PE files.
To download the payload you may either run the VBScript (which I don’t really recommend) or simply copy the entire hexadecimal wall of text into a hex editor and save it as a .exe file.

Figure 3 – MZ header spotted

Figure 4 – Dropping malware into temporary folder
When the VBScript is executed, it drops an executable into the targets’ temp folder. The file names are hard-coded as the malware author is probably trying to hide the malware in plain sight by using a common windows executable name, svchost.exe
The details of the extracted malware from the HTML is as follows:
SHA256: FD6C69C345F1E32924F0A5BB7393E191B393A78D58E2C6413B03CED7482F2320
VirusTotal Report: 50/54 (link); 2016-02-03 11:56:14 UTC
Compiled Date/Time: 2008-02-12 11:02:20
Packed: UPX
Let’s unpack the malware using UPX tool itself.

Figure 5 –Unpacking using upx -d
The details of the unpacked malware is as follows:
SHA256:876C5CEA11BBBCBE4089A3D0E8F95244CF855D3668E9BF06A97D8E20C1FF237C
VirusTotal Report: 44/54 (link); 2016-02-02 23:21:33 UTC
Compiled Date/Time: 2008:02:12 12:02:20+01:00
The malware camouflage itself as a bitdefender management console. Another interesting thing to note is that both the product version and the file version seems to be an ip address (106.42.73.61).

Figure 6 – Possibly IP address
[ Dynamic Analysis ]
Let’s begin our journey in analyzing this piece of malware. The malware author had used anti reversing techniques to deter malware analyst from reversing it. Using IDA Pro to see the binary isn’t of much use. Using Procmon surface some interesting stuff.

Figure 7 –New file dropped
As we can see from Figure 7, the malware is writing a new executable into “C:\Program Files\Microsoft\DesktopLayer.exe“. After examining the hashes of the newly dropped executable, I can conclude that the malware simply copy and pasted itself into the new location.

Figure 8 – Executing DesktopLayer.exe
After the file has been copied to the new location, A ProcessCreate function is called to execute the newly dropped executable. The current executable will then terminates.

Figure 9 – Executing Default Browser
Analyzing DesktopLayer.exe via olly debugger shows that the malware is attempting to run the default browser in the operating system. For this case here, it is attempting to execute IEXPLORE.EXE. On further examination, we will notice that the malware is actually trying to write process memory into the suspended IEXPLORE.exe process. This technique is known as process hollowing. Once the malware has finished writing its code into IEXPLORE.EXE process, it will then resume the suspended thread.

Figure 10 – Mutex
Based on Figure 10 taken from process explorer tool. We can observe that the malware uses a unique string (KyUffThOkYwRRtgPP) as it’s mutex.
It is also noted that the malware adds the following key into the registry “HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit“. By doing so, it is able to maintain it persistency in the victims’ machine.

Figure 11 – Persistent Registry Key
To get the actual malware codes that is running off IEXPLORE.exe, we would need to attach ollydbg into the running process and by using the OllyDumpEx plugin we can dump out the running process.
The dumped process contains some interesting strings.

Figure 12 – Script Tags and Autorun?
There are some more interesting strings in the dump that suggests that there is an Antidote for this virus. It also contained the mutex key and a domain name.

Figure 13 – Antidote is available
I am interested in using the antidote. Analyzing the injected process memory dump we come to this assembly codes. To activate the “Antidot”, we would just need to add a registry key; “HKLM\Software\WASAntidot\disable“.

Figure 14 – Disable Malware
As shown in Figure 15, we can prevent mass infection of the virus by adding the registry key as earlier . We even get to see a nice message box telling us that Antidot is activated.

Figure 15 – Antidot Activated
The malware loop through the folders in the victims’ machine and edit all html file it come across with the same malicious code we found in the phishing website. It also attempts to infect suitable .exe files with malicious codes. Once these infected executable gets executed, a copy of the same malware will be dropped and executed on the machine.
The malware also infects removable drives by editing the autorun.inf and planting itself in the RECYCLER sub folder. Better unplug your removable drives from the VM before you try analysing this!
The malware attempts to resolve a domain, fget-career.com. It also attempts to resolve google.com.
![]()
Figure 16 – DNS queries in Wireshark

Figure 17 – Spawning Shell
Once the malware calls fget-career url. It can executes shell on the target machine if commands are given.

Figure 18 – Open port 4678
The malware also attempts to listen on port 4678.

Figure 19 – Port 4678 Opened
One of the common ways to find infected or breached systems that most AV companies use is using IOC. We should be looking for known (or suspicious) command and control (C&C) traffic on the network and looking for known bad or suspicious indicators on the hosts.
Based on our dynamic analysis, below are the known IOC that we can scan our PCs.
[ Host based Indicator ]
- Mutex – KyUffThOkYwRRtgPP
- File – C:\Program Files\Microsoft\DesktopLayer.exe
- File – temp folder\svchost.exe
- Registry Key – HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Userinit
- Process – Default Browser with no parent
- C:\Program Files\Internet Explorer\complete.dat (Default browser path)
- C:\Program Files\Internet Explorer\dmlconf.dat (Default browser path)
[ Network based Indicator ]
- fget-career.com (DNS)
- User Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1)
- Listener on port 4678
[ Whois information ]
Domain Name: MAYBANKK2U.COM
Registrar: CHENGDU WEST DIMENSION DIGITAL TECHNOLOGY CO., LTD.
Sponsoring Registrar IANA ID: 1556
Whois Server: whois.west263.com
Referral URL: http://www.west.cn
Name Server: NS3.MYHOSTADMIN.NET
Name Server: NS4.MYHOSTADMIN.NET
Status: ok https://www.icann.org/epp#OK
Updated Date: 02-feb-2016
Creation Date: 02-feb-2016
Expiration Date: 02-feb-2017
IP Address: 207.226.137.64
Domain Name: MAYBANK2U-MY.COM
Registrar: CHENGDU WEST DIMENSION DIGITAL TECHNOLOGY CO., LTD.
Sponsoring Registrar IANA ID: 1556
Whois Server: whois.west263.com
Referral URL: http://www.west.cn
Name Server: NS3.MYHOSTADMIN.NET
Name Server: NS4.MYHOSTADMIN.NET
Status: ok http://www.icann.org/epp#OK
Updated Date: 02-feb-2016
Creation Date: 02-feb-2016
Expiration Date: 02-feb-2017
IP Address: 207.226.137.64

Once again network whois on the suspicious ip we got from the product version earlier on points back to China.
However, based on the analysis done on the malware and based on passive DNS and past whois records from Virustotal and who.is, the ip address we got from product version earlier could likely to be a fake to throw us off.
Another thing to note is that fget-career.com seems to be offline at the moment and it will be expiring in March 2016. Therefore if we are interested to know/plot the infection widespread of this malware or to takeover this malware we can attempt to buy this domain and host our own C&C server.
Source:http://www.vxsecurity.sg/
Kovter Malware Victims Were Secret Zombies in the ProxyGate Proxy Network
Legitimate proxy software distributed with Kovter malware.
During the past few months, computers infected with the Kovter click-fraud malware were also secretly added to the proxy network operated by ProxyGate, the Forcepoint team reports.
Kovter is one of the oldest malware strains around, one that has adapted to fit various needs and niches, and survived mainly as a click-fraud toolkit, ideal for making a quick buck out of online ads.
A recent spam campaign detected by Forcepoint (formerly Raytheon|Websense) has identified Kovter delivered through file attachments in the form of ZIP files.
When uncompressed, these ZIP files automatically execute a JavaScript file which connects to a Web server and downloads the Kovter malware.
In this specific campaign, Forcepoint saw this auto-download process abusing an Alexa Top 10 site, but also downloading two additional payloads besides Kovter.
One of them is the Miuref adware while the second was a legitimate executable, the ProxyGate installer.
All three files were executed as soon as they finished downloading, and silently installed their payloads on the victim’s machine without any type of user interaction needed.

Spam campaign’s author may have participated in ProxyGate’s referral program
It is yet unknown why the malware operators installed the ProxyGate application on the victim’s PC. This application does nothing malicious on its own and is designed to add the user’s computer to ProxyGate’s network of available proxy servers.
A possible explanation for these strange actions may be ProxyGate’s referral programwhich allows users to boost their own account’s number of free proxies available per day.
The spam campaign’s author may possibly be running other malicious campaigns through ProxyGate’s network and wanted to boost his available proxy output IP addresses by secretly abusing ProxyGate’s referral program by packaging the legitimate installer alongside Kovter’s payload.
This is not the first malware campaign that infected users and added their PC to a proxy network. In the past, the Bunitu and the ProxyBack malware families did the same thing.
Users infected with Kovter, may also want to check their computer’s list of installed applications and check to see if they’re not an unwitting zombie in a ProxyGate’s service.
EU Cookie Law Notification Abused to Hijack Clicks for Invisible Ads
Did you click on a cookie notification, or was that an ad?. Cyber-crooks have come up with a new way to fool users into clicking on ads instead of letting them access a website’s content, and this method relies on the EU Cookie Law notification.
In May 2011, the European Parliament adopted an EU Directive which said that individuals have the right to refuse the use of cookies, and so, website operators should show a notification on their sites to inform users if and how cookies are used.
Since then, all Internet users have come accustomed to these cookie usage notifications, some sites showing them to all visitors, not just those coming from European countries.

New clickjacking technique is hard to spot with the naked eye
According to cyber-security vendor Malwarebytes, a group of cybercrooks have found a way to abuse these innocent-looking notifications, tricking users into clicking on a hidden ad instead.
The scam is simple and quite ingenious. When accessing a website, a cookie usage notification is shown in the middle of a page inside a popup.
What users don’t know is that on top of this popup, the scammers also load an iframe with a Google ad inside. They then use the CSS property “opacity: 0” to make the ad invisible, letting the underneath notification show through.
The technique can also be used for malvertising campaigns
The ad is still there, but naked to the human eye. When the user clicks on any of the cookie notification’s buttons, he’s unwittingly clicking the ad, generating profits for the scammers, and redirecting the user to the ad’s target URL.
While this campaign is quite harmless in its current form, since it shows safe ads from legitimate companies, the trick behind it can easily be used to display malicious ads instead, cleverly redirecting users to dangerous Web pages where exploit kits infect users with malware.
Something tells us this isn’t the last time we hear about EU Cookie Law notifications being abused.

Source:http://news.softpedia.com/
Large Number of Adult Sites Distribute Malware Via AdXpansion Malvertising

While malvertising activity on adult sites has been ‘relatively’ quiet for some time, we started picking up dozens of attacks on moderately popular XXX portals, where moderate still means millions of daily visitors.
The modus operandi is quite straightforward and facilitated by a compromised Flash advert directly hosted and served by AdXpansion, an adult ad network, which triggers a hidden Flash exploit loaded from a seemingly innocent XML file. This technique has been used before in other self-sufficient Flash ad/exploit attacks.
This malvertising campaign has been running since at least Nov 21 and is affecting hundreds of adults sites. As soon as the rogue Flash advert is displayed in the browser (no click on it is required) it will attempt to load the exploit code.
Notable sites that were affected include:
- drtuber.com (55.3 M)
- nuvid.com (41.9 M)
- eroprofile.com (14M)
- iceporn.com (6.9M)
- xbabe.com (4.2M)
Monthly traffic in millions, according to SimilarWeb.
The malicious advert:

Malwarebytes Anti-Exploit blocks the malicious advert when it attempts to load the remote exploit shell code.
Technical details
An attack on drtuber.com:

The Flash exploit (CVE-2015-7645) resides inside of the second XML file loaded from malenkiyprince.website.
Same attack on iceporn.com distributes two different payloads at once:

The decoded Flash exploit:

We informed AdXpansion but have not received any response so far.
IOCs:
Malicious advert:
- media.hw.adxpansion.com/20151020133155/037ca5bba3dbe2a84632ebb9f7f98fdc.swf
- MD5: 037ca5bba3dbe2a84632ebb9f7f98fdc
Flash exploit:
- malenkiyprince.website/XFdjcl42RmNnXVZRc1wGGAY.xml
- MD5: f2145598b40e0b0506e6cb4b15513efd
- Decoded SWF MD5: 146d4f6d149c1b0613e1be3f3a777eab
Malware payloads:
- drtuber.com payload: 4bee00fbaede53b7b83192867717289c
- iceporn.com payload (1/2): f502ecb0e450df366fb110d102f34ce0
- iceporn.com payload (2/2): 3f7f1b51bdaccd3931ff78c154bda0b8
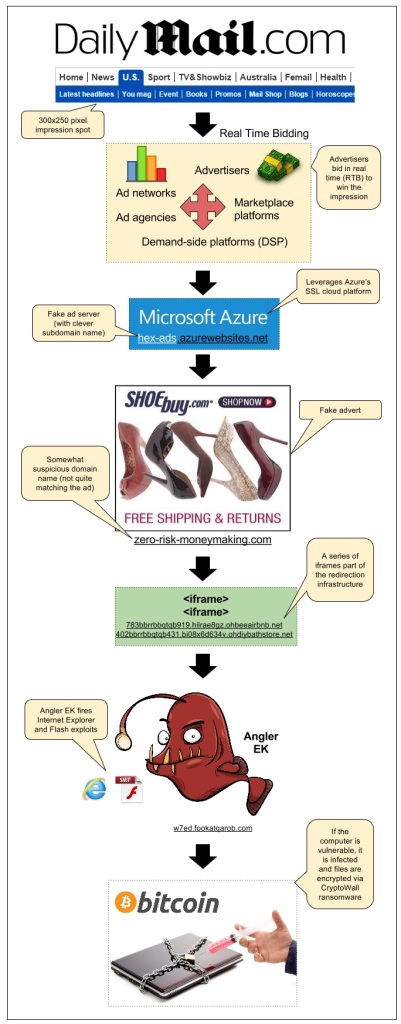
Angler Exploit Kit Blasts Daily Mail Visitors Via Malvertising
There has been a lot of buzz about the powerful Angler Exploit Kit in recent days. One thing is for sure, the gangs using it are extremely resourceful and won’t let attempts at slowing them down get in the way.
We detected an attack that happened via a sophisticated malvertising campaign we had previously documented on this blog: the SSL malvertising attack via Microsoft Azure.
This time it struck on popular British newspaper the Daily Mail which accounts for 156 million monthly visits according to SimilarWeb.
Infection flow:
- Publisher: dailymail.co.uk/ushome/index.html
- Ad call: www5.smartadserver.com/ac?out=js&nwid=1546&siteid=81193&pgname=sf300s&fmtid=35210&tgt=[sas_target]&visit=m&tmstp=[timestamp]&clcturl=http://pixel.mathtag.com/click/img?mt_aid=5829942979381995373&mt_id=1859987&mt_adid=148298&mt_sid=956001&mt_exid=9&mt_inapp=0&mt_uuid=90555615-e26a-4d00-8f31-09247eb00069&mt_3pck=http%3A//beacon-us-iad2.rubiconproject.com/beacon/t/ef1e4098-f217-4beb-8644-01803c6d7545/&mt_lp=http%3A//www.shoebuy.com/new-womens-shoes.htm%3F5DCjbVsxF67hxMc&redirect=
- Fake SSL ad server (malvertising): hex-ads.azurewebsites.net/?=awefyg677873jk2o
- Fake advert for shoebuy.com (malvertising): zero-risk-moneymaking.com/?vC237XnBcMvp
- iframe(1): 783bbrrbbqtqb919.hilrae8gz.ohbeeairbnb.net/287e1e7f185ac57172a0a7b70483e
- iframe(2): 402bbrrbbqtqb431.bi08x6d634v.ohdiybathstore.net/ced1d59c80127f0fb50e6e083d3
- Angler Exploit Kit: w7ed.fookatqarob.com/boards/viewforum.php?f=61ls0&sid=826888i5.161802rr6070
Malvertising has been one of the main infection vectors and continues to affect large publishers and ad networks through very distinct campaigns, very much like a whack-a-mole game.
In addition to spreading via compromised websites, Angler EK leverages malvertising thanks to several different threat actors who use clever ways to go undetected as long as possible or are able to quickly adapt and get back on their feet if one of their schemes gets too much attention and is disrupted.
During the past months we have been working very closely with ad networks, publishers, cloud providers and other companies that have been abused by these attacks.
In addition, we hope that well documented cases such as this one help consumers to realize that malvertising is a very dangerous and yet often misunderstood threat. There is no such thing as a safe website anymore and it is everyone’s responsibility to ensure their devices are fully patched and well protected.
We contacted the affected publisher (DailyMail) and related ad networks right when we found out about this incident. On 10/12, we were informed by MediaMath that the malicious creative had been disabled.
Malwarebytes Anti-Exploit users were already protected against this attack, thanks to its proactive exploit mitigation capabilities.
Novel malware dupes victims with fake blue screen of death
Malware creators are hijacking Microsoft Windows’ infamous BSOD in a fresh malvertising campaign.
A new malvertising campaign uses the Blue Screen of Death to scam users into handing over their money and potentially their identity.
Online search engines are used daily by millions of web users. In order to support the vast amounts of requests these search engines receive and process, search engine providers — such as Google, Yahoo and Microsoft — offer advertising platforms and packages for businesses. Users view sponsored links placed high up on a search results page, businesses gain more exposure and the search engine generates revenue.
However, search engine advertising is also a place ripe for exploit and is being used by cyberattackers in order to generate their own revenue. One of the most commonly-known techniques include setting up malicious domains which deliver malware payloads to victim machines — resulting in slave systems, compromised PCs and data theft. Some attackers also set up fraudulent domains which appear legitimate in order to lure victims to input their account information.
Unfortunately, many online advertisement schemes run through third-party platforms and sometimes threat actors slip through the net — resulting in fraudulent and malicious links being displayed on legitimate, trustworthy domains.
Now, a new and rather novel campaign has attracted cybersecurity firm Malwarebytes’ attention.
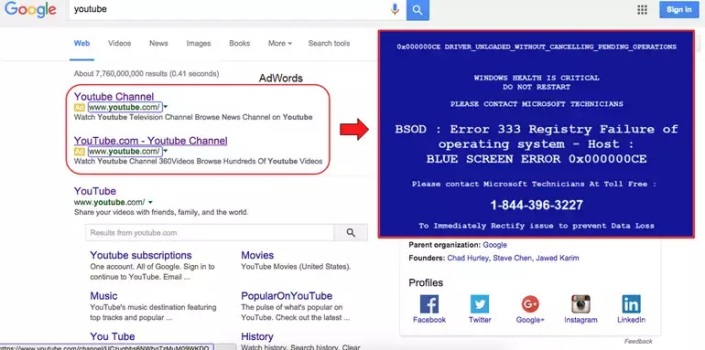
In a blog post on Monday, the team at Malwarebytes revealed their findings on a new malvertising campaign which uses the infamous Microsoft Windows’ Blue Screen of Death (BSOD) as its selling point.
The group uses BSOD to reel in potential victims as a social engineering technique. The security company found attackers bidding on popular phrases through Google’s AdWords advertising space, including the YouTube keyword to display their adverts at the top of the search engine. This link is meant to go to the designated YouTube URL, but instead, clicking on this advert leads to a convincing web page complete with the BSOD image.
While some users will not be fooled, others without much technical knowledge are likely to be.
On the page, users are instructed to call a toll-free “helpline” to resolve the BSOD issue. The scammers are waiting at the other end for these calls, where they pretend to be Windows support and offer their victims expensive and non-existent “support packages” — defrauding users of anything from $199 to $599.
However, this isn’t necessary the end of a painful story. Malwarebytes says innocent PC users may also end up having their identity stolen and bank accounts rinsed of funds.
In this particular campaign, at least two domains have been registered to redirect users to the fraudulent pages through IP addresses in Arizona.
The campaign was reported to Google and the adverts were immediately pulled, but this is is only one such campaign out of thousands of scams appearing every day online.
Source:http://www.zdnet.com/
Hilton hotels in credit-card-stealing malware infection scare
Someone has hacked the Hilton’s sales registers, and made off with guests’ credit-card details, it’s claimed. The hotel chain confirmed today it is investigating the alleged breach of its computer security.
Investigative journo Brian Krebs says malware in point-of-sale (POS) terminals is believed to have nicked the card information, some of which is already being used to make fraudulent transactions, we’re told.
Multiple sources have told Krebs that bank staff have traced the misused cards to a common source: the tills at restaurants and gift shops in various Hilton hotels around the US.
It is not clear how many accounts may have been compromised, but the malware was active from April 21 to July 27 of this year, apparently. Visa reportedly issued a security alert on the security breach back in August.

Sales terminals in Doubletree, Embassy Suites, Hampton, and Waldorf Astoria hotels were also compromised, it is claimed.
A Hilton spokesperson told The Register late on Friday afternoon:
Hilton Worldwide is strongly committed to protecting our customers’ credit card information. We have many systems in place and work with some of the top experts in the field to address data security. Unfortunately the possibility of fraudulent credit card activity is all too common for every company in today’s marketplace. We take any potential issue very seriously, and we are looking into this matter.
If Krebs’ sources are on the money, Hilton will be the latest major American chain to suffer a massive credit card security breach as the result of a malware incursion. Criminals typically plant malware on PC-like tills to collect credit card information when a purchase is made, and then siphon off the numbers.
Malware implants on Cisco routers revealed to be more widespread
Researchers detected 200 Cisco routers with malicious firmware in 31 countries, with the U.S. having the largest number of potentially infected routers.
Attackers have installed malicious firmware on nearly 200 Cisco routers used by businesses from over 30 countries, according to Internet scans performed by cyber crime fighters at the Shadowserver Foundation.
Last Monday, FireEye subsidiary Mandiant warned about new attacks that replace the firmware on integrated services routers from Cisco Systems. The rogue firmware provides attackers with persistent backdoor access and the ability to install custom malware modules.
At the time Mandiant said that it had found 14 routers infected with the backdoor, dubbed SYNful Knock, in four countries: Mexico, Ukraine, India, and the Philippines. The affected models were Cisco 1841, 8211, and 3825, which are no longer being sold by the networking vendor.
Since then, the Shadowserver Foundation, a volunteer organization that tracks cyber crime activities and helps take down botnets, has been running an Internet scan with Cisco’s help in order to identify more potentially compromised devices.
The results confirmed Mandiant’s suspicions: there are more than 14 routers infected with SYNful Knock out there. Shadowserver and Cisco identified 199 unique IP (Internet Protocol) addresses in 31 countries that show signs of compromise with this malware.
The U.S. has the largest number of potentially infected routers, 65. It is followed by India with 12 and Russia with 11.
Shadowserver plans to start notifying network owners who have signed up for the organization’s free alert service if any of the compromised routers fall into their IP blocks.
“It is important to stress the severity of this malicious activity,” the organization said Monday in a blog post. “Compromised routers should be identified and remediated as a top priority.”
By controlling routers, attackers gain the ability to sniff and modify network traffic, redirect users to spoofed websites and launch other attacks against local network devices that would otherwise be inaccessible from the Internet.
Since the devices targeted by the SYNful Knock attackers are typically professional-grade routers used by businesses or ISPs, their compromise could affect large numbers of users.
Cisco has been aware of attackers using rogue firmware implants for several months. The company published a security advisory in August with instructions on how to harden devices against such attacks.
Source:http://www.infoworld.com/
MWZLesson POS Trojan borrows code from other malware
Security experts at Doctor Web have discovered a new PoS Trojan dubbed MWZLesson that borrows code from other popular malicious software.
Security experts at Dr. Web have discovered a new PoS Trojan that was designed by mixing code from other malware.
The new PoS Trojan, dubbed Trojan.MWZLesson, was designed reusing the code of other popular malware, including the Dexter PoS and the Neutrino backdoor.
“This code was borrowed from another Trojan designed for POS terminals and named Trojan.PWS.Dexter. The malware sends all acquired bank card data and other intercepted information to the command and control server.” states the blog post published by Dr. Web.
Like its predecessors, MWZLesson compromises the POS terminals, scraping the RAM memory to search for credit card data. Once infected the PoS system, the malware communicates with the server over the HTTP protocol, it steals card data and sends it to the command and control server through GET and POST requests.
“Trojan.MWZLesson can intercept GET and POST requests sent from the infected machine’s browsers (Firefox, Chrome or Internet Explorer). Such requests are forwarded to the command and control server run by cybercriminals.” continues the post.
Trojan.MWZLesson can update itself, download and run additional files, find specific documents, and even mount an HTTP Flood attack.
The experts at Dr.Web discovered that the Trojan.MWZLesson also implements features to avoid detection and eradicate other malware that infected the PoS malware.
“Trojan.MWZLesson checks for virtual environments and debuggers and gather information on the infected machine. The newly discovered PoS malware is able to remove other malware present on the machine and is able to exfiltrate different kinds of data.”
The discovery of the Trojan.MWZLesson confirms the great interest of the criminal crews in infecting POS terminals and their abilities in recyclying code of older and efficient malware.
Source:http://securityaffairs.co/
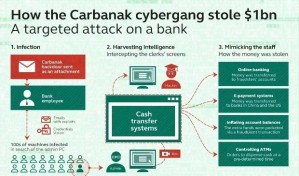
Carbanak Banking Trojan Returns with a New Series of Attacks
The Carbanak banking trojan was spotted once again in attacks on financial institutions and businesses across the globe, as CSIS is reporting.
Carbanak, also known as Anunak, was previously discovered and analyzed by Russian-based Kaspersky Lab security firm, in February 2015.
Back then, Kaspersky Lab was estimating that the group behind Carbanak infiltrated up to 100 financial institutions worldwide, gaining control over their computers, and stealing around $1 billion / €876.7 million.
Since then, the trojan has been making sporadic returns, always changing one small detail in its operation to keep up with firewall and antivirus updates.
New Carbanak variant uses a new proprietary communications protocol
As the CSIS team is now reporting, a new variant of the trojan has been observed in the wild, targeting the same kind of financial corporations as before.
This version of Carbanak is different from the original, using a predefined IP address instead of random generated domains to talk to the C&C server, employing random generated file names, and featuring a new proprietary protocol for managing its plugins and internal communications.
Just as before, Carbanak still hides in an infected svchost.exe process, keeps its modular structure that allows it to shape shift and adapt to victims, and continues to use a legitimate code-signing certificate to avoid detection.
According to CSIS, this new version of Carbanak uses a code-signing certificate issued by Comodo, to what appears to be a legal Russian-based business.
Carbanak continues to brazenly flaunt its Russian connection
Security researchers believe the criminals behind Carbanak have registered a real company with the sole purpose of having a legal base for some of their fraudulent transactions.
“Carbanak-related transfers are rather huge,” says the CSIS team. “Possibly, they have registered a company and opened bank accounts in order to receive their stolen money while having full control of the transferring process.”
Previously ESET researchers found a version of Carbanak using stolen certificates belonging to companies Moscow-based companies Stroi-Tekh-Sever, Flash, OOO “Techcom” and Torg-Group.
The Russian connection for the Carbanak trojan is very well known, Trend Micro researchers previously linking one of its C&C servers to an IP owned by the Russian Security Service (FSB).
Source:http://news.softpedia.com/
Hacker pleads guilty in Facebook malware and spam scheme
A New York man has pleaded guilty in federal court for violating an anti-spam law, although his alleged involvement in cybercriminal activities went way beyond sending spam.
Eric L. Crocker, the accused hacker, pleaded guilty to just one charge carrying a maximum penalty under the CAN-SPAM Act of three years in prison and a fine of $250,000.
Crocker was allegedly involved in hacking computers to create an enormous botnet that he maintained for co-conspirators, who used the network of compromised computers to send spam and much more.

Crocker was one of a dozen people arrested in the US in July for their connection with the notorious Darkode cybercrime forum.
According to US Attorney David J. Hickton, of the Western District of Pennsylvania, Crocker used Darkode to market his botnet.
An unidentified co-conspirator paid Crocker and others $200-$300 for every 10,000 computers they infected as part of the botnet, according to the federal indictment.
To build the botnet, Crocker infected victims through Facebook.
As described by law enforcement, Crocker used a “Facebook Spreader” malware called Slenfbot to infect victims via booby-trapped links in Facebook chat messages.
It worked like this: a user became infected after clicking on a link to the malware sent to them via a Facebook message. The malware was then used to send phishing messages to the victim’s friends on the social network.
When those recipients clicked on a link in the message, thinking it was from their friend, they automatically downloaded the malware and so the cycle began again.
Once the malware was on a victim’s computer, the computer became a “bot” that Crocker could control remotely to send further spam.
The Darkode forum, where Crocker allegedly sold his services as “Phastman,” was taken down by the FBI and Europol in July 2015.
Described by the FBI as “the most sophisticated English-speaking forum for criminal computer hackers around the world,” Darkode’s small membership used it as a hub for buying and selling services including malware, zero-day exploits, and botnets.
Members reportedly included some of the Lizard Squad hackers responsible for denial-of-service attacks on Sony and Microsoft.
Lenovo used shady ‘rootkit’ tactic to quietly reinstall unwanted software
Lenovo has been caught using a technique, often used by some malware to withstand being deleted, to reinstall unwanted software on the computers it sells.
As reported on a number of forums and news-sharing sites, some users have accused the computer maker of overwriting Windows files to ensure its own-brand software and tools were installed — even after a clean install of the operating system.
The issue was first reported as early as May, but was widely reported Tuesday.
The “rootkit”-style covert installer, dubbed the Lenovo Service Engine (LSE), works by installing an additional program that updates drivers, firmware, and other pre-installed apps. The engine also “sends non-personally identifiable system data to Lenovo servers,” according to the company. The engine, which resides in the computer’s BIOS, replaces a core Windows system file with its own, allowing files to be downloaded once the device is connected to the internet.

But that service engine also put users at risk.
In a July 31 security bulletin, the company warned the engine could be exploited by hackers to install malware. The company issued a security update that removed the engine’s functionality, but users must install the patch manually.
Many Yoga and Flex machines (among others) running Windows 7, Windows 8, and Windows 8.1 are affected by the issue. Business machines, such as Think-branded PCs, are not affected.
A full list of affected notebooks and desktops is listed on Lenovo’s website.
It’s not the first time Lenovo has been caught in a privacy-related pickle.
Earlier this year, the computer maker was forced to admit it had installed Superfish adware over a three-month period on new machines sold through retail channels. The adware had the capability to intercept and hijack internet traffic flowing over secure connections, including online stores, banks, among others.
Users were told they should “not use their laptop for any kind of secure transactions until they are able to confirm [the adware] has been removed,” security researcher Marc Rogers told ZDNet at the time.
It was thought as many as 16 million consumers and bring-your-own-device users were affected by the preinstalled adware.
Source:http://www.zdnet.com/
“Funtenna” software hack turns a laser printer into a covert radio
LAS VEGAS—During the Cold War, Soviet spies were able to monitor the US Embassy in Moscow by using a radioretroreflector bug—a device powered, like modern RFID tags, by a directed radio signal. But that was too old school for Ang Cui, chief scientist at Red Balloon Security and a recent PhD graduate of Columbia University. He wanted to see if he could do all of that with software.
Building on a long history of research into TEMPEST emanations—the accidental radio signals given off by computing systems’ electrical components—Cui set out to create intentional radio signals that could be used as a carrier to broadcast data to an attacker even in situations where networks were “air-gapped” from the outside world. The result of the work of his research team is Funtenna, a software exploit he demonstrated at Black Hat today that can turn a device with embedded computing power into a radio-based backchannel to broadcast data to an attacker without using Wi-Fi, Bluetooth, or other known (and monitored) wireless communications channels.

Cui has previously demonstrated a number of ways to exploit embedded systems, including printers and voice-over-IP phones. In 2012, he demonstrated an exploit of Cisco phones that turned on the microphone and transformed phones into a remote listening device. Michael Ossmann of Great Scott Gadgets, a hardware hacker who has done some development of exploits based on concepts from the NSA’s surveillance “playset,” suggested to Cui that he could turn the handset cord of the phone into a “funtenna”—an improvised broadcast antenna generating radio frequency signals programmatically.
With just seven lines of code injected into the embedded computer of an otherwise unmodified laser printer, Cui was able to turn the printer into a radio transmitter by simply leveraging the electrical properties of existing input and output ports on the printer. By rapidly flipping the power state of general purpose input/output (GPIO) pins, Pulse Width Modulation (PWM) outputs, and UART (serial) outputs on a Pantum P2502W laser printer—“the cheapest laser printer we could find,” Cui said—the Funtenna hack was able to create a modulated radio signal as a result of the magnetic fields created by the voltage and resulting electromagnetic waves.
The hack couldn’t generate signals strong enough using the relatively short wires of the GPIO connections on the printer. Despite flipping every GPIO output available, he only got an effective range of transmission of a few meters. Instead, the UART output with a 10-foot cable generated a signal that could be picked up from outside a building—even through reinforced concrete based on Cui’s research.
The demonstration, Cui said, shows that embedded devices need their own built-in defenses to truly be secure. And printers are merely a starting point for Cui’s work. The same sort of attack could conceivably be launched from any “internet of things” device or other system with onboard computing power—including network routers and firewalls.
“A network [intrusion detection system] is no substitute for host-based defense,” he said. “You could monitor every known spectrum, but it would be very expensive and may not work. The best way is to have host-based defense baked into every embedded device.”
Source:http://arstechnica.com/
WordPress 4.2.3 is out, update your website now
If you own a website then there’s a good chance – better than one in five – that it uses the WordPress Content Management System (CMS).
If it is, you should update it now.
The latest version, version 4.2.3, was released on 23 July 2015 and includes a fix for a cross-site scripting (XSS) vulnerability that your website could do without.
The flaw allows WordPress users who have Contributor or Author roles to add javascript to a site (something normally reserved for Editors and Administrators) using specially crafted shortcodes.

Attackers who can add javascript to a site can use it to do all manner of damage such as infecting users with malware or stealing their cookies.
Some measure of protection is afforded by the fact that attackers will need a way to log in to a vulnerable site with at least Contributor privileges.
However, it is far easier (and safer) to simply close off a backdoor than to try and second-guess how an attacker might lever it open – and you should update even if you think you won’t be vulnerable.
Across the hundreds of millions of WordPress sites that exist there are likely to be plenty that have registration or membership schemes for unknown users and plenty more that unwittingly suffer from badly configured user rights, disgruntled ex-users, poorly protected passwords and session cookies or users who’ve had credentials stolen.
Any one of those things (and no doubt more I’ve not thought of) could give an attacker the foothold they need.
And bother they will because of the vast size of the WordPress install-base.
Criminal gangs use huge networks of compromised computers, called botnets, to spread malware and send spam and they’re always looking for easy ways to harvest more victims.
Vulnerabilities in popular web platforms like WordPress and Drupal provide an easy way for them to target tens or even hundreds of millions of websites at a time with automated tools.
And they can get those automated attacks up and running fast.
In October 2014, the Drupal security team reported that automated attacks started appearing within three hours of a Highly Critical vulnerability being announced.
In a sobering follow-up message two weeks later they told their users toassume that their site had been compromised if it hadn’t been patched within seven hours of the original announcement!
It’s why the number one rule of WordPress security is always run the latest version of WordPress.
Fortunately that’s become a lot easier since October 2013 when WordPress released the first version of their software, version 3.7, with automatic security updates (something Drupal is still waiting for).
Sites with automatic updates enabled began receiving their updates almost immediately.
If your site doesn’t update automatically you can upgrade by logging in and going to Dashboard → Updates and clicking “Update Now” or bydownloading a copy of the software and installing it yourself.
New GamaPoS Malware served by the Andromeda Botnet
The experts at Trend Micro discovered GamaPoS, a new PoS malware that is spread through the Andromeda botnet in the US and Canada.
GamaPoS is the name of the last PoS malware used by criminal crews to steal credit card data from the memory of payment systems. Security experts at Trend Micro discovered which discovered the GamaPoS malware explained that it is distributed by a large botnet known as Andromeda, which has been around since 2011.
“We discovered GamaPoS, a new breed of point-of-sale (PoS) threat currently spreading across the United States and Canada through the Andromeda botnet .” states Trend Micro in a blog post.
The experts found systems infected in the US and Canada, the malware that targets Windows systems is written in Microsoft’s.
NET. Researchers explained that the choice of .Net is unusual for RAM scraping PoS malware.
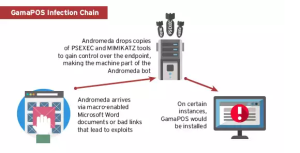
The experts noticed that hackers have chosen to spread the malware through a botnet instead by stealing or guessing remote access credentials in response to countermeasures implemented by many retailers. Many organizations, in fact, have improved the security of their systems protecting internal resources from remote attacks.
Bad actors have used a botnet in order to infect machines worldwide, including machines inside the trusted internal networks of target organizations.
Trend Micro reported that the attacks start with spam messages containing malicious emails purporting to include PCI DSS (Payment Card Industry Data Security Standard) compliance documents or software updates necessary to protect systems from the recently discovered MalumPs malware. The attachments contain malicious macros that install the backdoor on the infected PC that is used to serve the GamaPoS.
“This means that it launches a spam campaign to distribute Andromeda backdoors, infects systems with PoS malware, and hopes to catch target PoS systems out of sheer volume. Rough estimates show us that GamaPOS may have only hit 3.8% of those affected by Andromeda.” continues the post.
The experts also discovered that threat actors used the backdoor to download tools that can be used to to manually hack other systems from the networks of affected organizations and make lateral movements .
The experts detected infected systems in a number of industries, including home health care, online retail and consumer electronics.
GamaPoS targets a range of cards, including Visa and Discover, their users are exposed to the risk of hack.
“While the evaluated example does not do Luhn validation, GamaPoS does manually filter the data by evaluating the first few numbers of the scraped data.
- 4 (length=12) – Visa
- 56 to 59 (length=14) – Maestro and other ATM/debit cards
- 6011 (length=12) – Discover Card
- 65 (length=14) – Discover
Finally, it would attempt to upload the collected data via the command-and-control server that has been selected during initial execution.” states the post.
Source:http://securityaffairs.co/
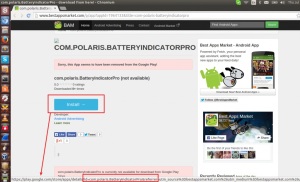
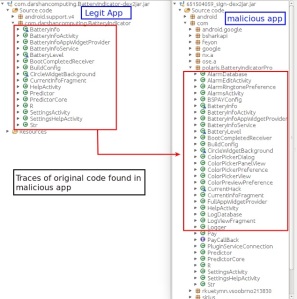
Beware of Fake Apps: Google Deletes Fake BatteryBot Pro Malware App
Last week we reported hackers are developing Android malware every 17 seconds, making it one of the most vulnerable OS ever.
Now a spoofed copy of the popular app named as “BatteryBot Pro” requested unnecessary permissions from the user during installation in an attempt to get full control over the user’s Android device, a researcher found out.
The app is alleged to imitate the functionalities of the authentic app and possess hidden ad-fraud activity, the app has recently been removed byGoogle from their official Android Play Store.
For those of you who don’t know, BatteryBot Pro is a genuine battery monitoring app that already exists in the Android app store which offers its users to check detailed information related to their smartphone’s battery like its temperature, voltage, health, current information in mA, and other useful data.
An unknown hacker decided to copy the original app’s functionalities while implementing irremovable malware, but thanks to a researcher named Shivang Desai who reported the app to Google and spoiled the developer’s vision of hacking Android devices.
The package of this app was named “com.polaris.BatteryIndicatorPro.”
The developers behind this app were trying to infect enough devices so that they can generate profit through ad click fraud and premium short messaging service (SMS) fraud. Apart from that, the app is precisely designed to download and install additional malicious Android APKs without the user’s permission. In addition to the hidden downloading of apps, the malware app also displays pop-up advertisements to the user.
“This malware was not only built with the purpose of displaying ads, it was also designed with more evil intentions,” Desai said.
INSTALLATION OF MALWARE APP
When installing the malicious app, it requested lots of more permissions as compared to the original app, some were normal but other were troublesome which included the permission to access the Internet, mount and unmount file system, send SMS messages, disable keyguard, get user account information, download without notification, and initiate outgoing calls.
After installation of the malicious app, the researcher found out that the malicious app “demanded administrative access,” which indicates that the objective of developer is “to obtain full control access of the victim’s device.”
EXECUTION OF CLICK FRAUD AND AD FRAUD ACTIVITIES
But once the permission is granted by the victim, the malware app will provide exactly the same functionality of the original BatteryBot Pro app but continues to execute malicious activity in the background.
Apart from the execution of malicious activity the app also tried to download various advertisement libraries which carry a click fraud campaign, thesecurity researcher found out.
“Some of these URLs were hard coded in the app and some were sent by the remote server.” – Shivang Desai, Zscaler Security Researcher.
The malware app also tried to pull some personal information from the device, including cell phone operator, availability of SIM card, IMEI number, language, cell phone model, location and available device memory.
Then depending on the collected parameters, the malware app begins to receive the list of advertisements to be displayed on the device along with the URL from where the ads will be fetched.
UNABLE TO UNINSTALL MALWARE APP
Apart from the execution of click fraud and ad fraud activities, the app is explicitly designed so that it once installed can never be uninstalled again, at least by the novice user. The app run with administrative rights so that the user cannot remove it.
According to the researcher who tried to uninstall this malicious app,
“While in some of the scenarios we were able to manually delete the app, the malware authors have taken care of ensure persistence. The malware silently installs an app with a package name of com.nb.superuser, which runs as a different thread and resides on the device even if the app is forcefully deleted.”
“A few traces of command execution were also seen in the app but were not fully implemented,” said Shivang Desai, the researcher at Zscaler. “Perhaps the developer is working on an upgraded version of the malware with proper ‘command-execution’ functionality,” Desai further added.
Fuente:https://www.hackread.com
Hackers’ capability to crash trains raises security concerns, malware could lead to train crashes in the UK
Cyber attacks can crash trains. Intense security concerns have emerged, after the upgrade of the British railway network that can be affected by malware.
The new railway network upgrade in the United Kingdom has raised a lot of concerns, as far as its overall network security is concerned. It seems that over thirty million pounds will be invested in the upgrade, which can potentially lead to loss of control over the railway network, according to the estimates of security experts. Several types of malicious software can result in an increase of hazards, which can in turn deteriorate the quality standards and the safety level of the British railway as a whole.

With a cyber attack of a great extent, even train collisions can happen and this is certainly something that puts all the British citizens at risk, making them wonder as to whether or not the specific investment is worth it. The way in which trains have responded up to now is likely to change and this will lead to unprecedented casualties, damaging the credibility of the railway as a means of transportation. From City University, there have been complaints as to the possibility of such actions resulting in the lack of monitoring the trains.
From the Department of Transport in the UK, there has been the following comment on the recent concerns:
“We know that the risk [of a cyber-attack] will increase as we continue to roll out the digital technology across the network. We work closely with government, the security services, our partners and suppliers in the rail industry and external cyber security specialists to understand the threat to our systems and make sure we have the right controls in place. It is the smart malware [malicious software] that alters the way the train will respond. So, it will perhaps tell the system the train is slowing down when it is speeding up. Governments are not complacent, individual ministers know this is possible, and they are worried about it. Safeguards are going in, in secret, but it is always possible to get around them. We keep security arrangements under constant review to take account of the threat and any new challenges we face.”
It is worth stating that the same system planned to be installed in the United Kingdom will be expanded and it will stretch all over the European Union. The estimated year in which all the systems will be replaced with this upgrade is 2020; by this time, adequate improvements need to have taken place for the safety of all passengers.
Source:http://securityaffairs.co/
KINS Malware Toolkit Leaked Online
Version 2.0.0.0 of a toolkit for the banking Trojan known as KINS was leaked last month, researchers revealed on Sunday.
According to the MalwareMustDie research group, which learned of the leaked files on June 26, the package includes the KINS 2.0.0.0 builder and the source code for the control panel. The package has been widely distributed on the Web, giving cybercriminals the means to generate new malware and control their botnets.
Researchers have pointed out that the developers of the malware builder call the tool “KINS Builder.” However, the binaries generated by it actually appear to be versions of the banking malware called ZeusVM. The malware generated by the builder is completely different from previous KINS versions.
Experts say this shows that KINS developers have integrated ZeusVM technology into their creation.
One of the features borrowed by KINS from ZeusVM is the use of steganography, the practice of concealing a file or message within another file or message. In the case of KINS/ZeusVM, the malware’s configuration data is hidden in a .JPG image file.
MalwareMustDie researchers are providing the KINS toolkit package through private channels to other experts and security firms that want to analyze the threat.
In the meantime, the malware crusaders have teamed up with the French researcher known as Xylit0l and the Japanese researcher known as unixfreaxjp to prevent the toolkit from being distributed. They have managed to remove the package from several websites, but the files have been made available on too many sites.
Experts believe that the leak will lead to more botnets powered by KINS/ZeusVM 2.0.0.0.
MalwareMustDie also revealed that it has spotted ads on cybercrime forums for version 3 of KINS. According to researchers, the malware has been sold for $5,000.
MalwareMustDie has published videos, technical details, and code for the leaked KINS toolkit.
*Updated. The original version of the story incorrectly stated that the source code for both the builder and the control panel was made available. Only the source code for the control panel has been leaked.
Source:http://www.securityweek.com/
Surveillance software vendor Hacking Team hacked
Italian surveillance software slingers Hacking Team has allegedly been cracked by hackers, who exfiltrated some 400Gbs of data.
The plunder has been uploaded to BitTorrent in a monstrous listing of directories, allegedly including audio recordings, emails, and source code.
Hacking Team sells the Da Vinci malware surveillance software to law enforcement agencies claiming to only deal with ethical governments. It is marked as an Enemy of the Internet by activist outfit Reporters Without Borders.
The unknown hackers also hijacked Hacking Team’s Twitter account and, at the time of writing, are tweeting screenshots of emails stolen in the raid.
The trove also allegedly reveals all Hacking Team customers and when they purchased the software
The company is said to count Saudi Arabia, Oman, and Lebanon among its customers.
Chile allegedly bought the software last year for $US2.85 million, according to exploit activist Christopher Soghoian (@csoghoian) who is analysing the data.
Some of those may in coming days be scrambling to switch off the surveillance software due to source code being made public.
The claims are unverified at the time of writing. (This writer lives just outside of Australia’s tiny National Broadband Network and as a result has not yet downloaded the huge cache).
Hackers are tweeting the alleged contents of the stolen emails from Hacking Team CEO David Vincenzetti which appear to reveal dealings with oppressive governments.
The torrent listings also allegedly contain login credentials for the company’s support sites in Egypt, Mexico, and Turkey.
New Tinba variant delivered via HanJuan Exploit Kit in malvertising attack
Researchers with Malwarebytes have observed a new variant of Tinba banking malware being distributed via the HanJuan Exploit Kit as part of a malvertising attack that involves advertising and URL shortening service Adf.ly.
Jerome Segura, senior security researcher with Malwarebytes, told SCMagazine.com in a Thursday email correspondence that the majority of infections have been observed in the Netherlands, but he added that the campaign is still in its early stages and could expand.
The threat was made possible because the attackers were able to successfully submit a malicious advertisement to Adf.ly, which was then arbitrarily displayed to users who clicked on shortened Adf.ly links around the web.
“Adf.ly monetizes its service by displaying ads when people click on the shortened link,” Segura said. “Before the shortened link redirects to the actual URL, an ad is displayed for a few seconds. This is where the malvertising happened.”
Once the malvertisement was displayed, a redirection chain triggered without any user interaction, Segura explained. According to a Wednesday post, users were ultimately taken to a compromised Joomla website that pushed what is believed to be the HanJuan Exploit Kit.

Researchers observed the HanJuan Exploit Kit targeting two exploits in order to deliver the Tinba variant – an Adobe Flash Player vulnerability, CVE-2015-0359, and an Internet Explorer vulnerability, CVE-2014-1776, the post said.
The Tinba variant, which was initially identified by Malwarebytes as ‘Fobber,’ was observed going after sensitive information – including Google, Microsoft, Facebook and Twitter credentials – by hooking browsers and grabbing usernames and passwords before they were encrypted, the post said, adding the malware was not observed stealing banking credentials.
“This is an evolved version of Tinba v2, which was identified by security researchers at Fox-IT,” Segura said. “While the core of the program is more or less the same, the authors of this piece of banking malware have improved its encryption capabilities, making it harder for security researchers to properly identify and take down.”
To address these types of threats, Segura said that advertising networks must ensure they are delivering clean content, and end users must make certain their computers are fully patched and are protected with adequate security solutions.
Source:http://www.scmagazine.com/