How to intercept mobile communications (calls and messages) easily without hacking
Monitoring cell phones without their knowledge is growing rapidly in Latin America countries like Argentina, Mexico and Brazil after being very famous in US since 2008
The Stingray/ GSM interceptor/IMSI catcher is equipment that can gather data from hundreds of phones over targeted areas and they can also perform denial-of-service attacks on phones and intercept conversations. Though these products are not available legally but they can be bought through black markets or through deep web.
Law enforcement and the military use these devices to track cellphones. A stingray system involves an antenna, maps, and a signal device. The device mimics as a cellphone tower Base Transmitting Stations (BTS) and gets the phones in the area to connect to it. Then it collects International Mobile Subscriber Number (IMSI) and the Electronic Serial Number (ESM) numbers associated with the phone and can connect any phone.
There are two ways to use the devices, says Mike Stevens, a mobile ethical hacking training expert of International Institute of Cyber Security.
One way is to use antenna in a given area to collect International Mobile Subscriber Number (IMSI) and the Electronic Serial Number (ESN) numbers of mobile phones in that area and see who is in that given area.
Second way is to locate a mobile phone with IMEI, International Mobile Subscriber Number (IMSI) and the Electronic Serial Number (ESM) number like apple Find my phone application but in this case the phone can be traced even if the phone is formatted, as IMEI remain associated with the hardware not the software. Based on the signal strength of the device you can find the exact location of the mobile phone.
Also in some cases a DOS attack can be done on mobile phone but in terms of GSM signal not in term so of Data packets. When under DOS attacks the phone cannot receive or make any calls.
These devices can be used with software to eavesdrop on mobile phone conversations and spoof calls and SMS. These softwares are known as Over-The-Air special signal software like FISHHAWK, PORPOISE.
These devices are also knows as GSM INTERCEPTOR OR IMSI CATCHER. There are various devices like these in the market easily available. James Taylor mobile information security course expert, mentioned some of them like GOSSAMER, LONGSHIP, BLACKFIN, BLACKFIN II, HAWKSBILL, SPURDOG, FISHFINDER, KINGFISH, STINGRAY, STINGRAY II, GSM INTERROGATOR, CDMA INTERROGATOR, IDEN INTERROGATOR, UMTS INTERROGATOR, FISHHAWK, PORPOISE, FIREFISH, TARPON, AMBERJACK, HARPOON, MORAY, LANTERNEYE, RAYFISH, STONECRAB.
Some of the devices are easily available in market.

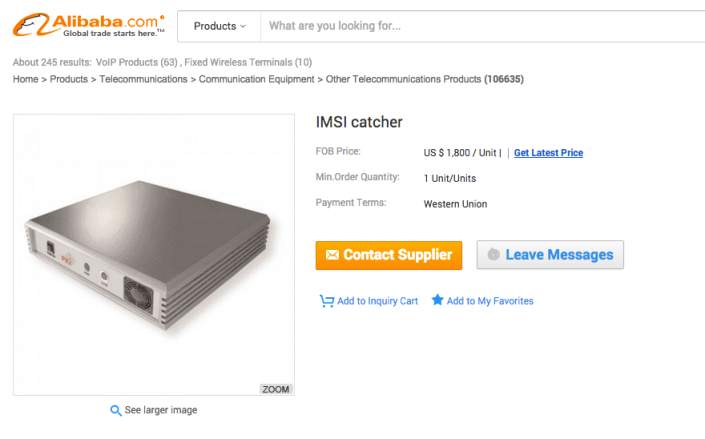

We will talk about few of them below:
Gossamer like Devices
The Gossamer is a small portable device that is similar to stingray and can gather data on mobile phones operating in a target area. The Gossamer device is much smaller than stingray, it can be used to perform a denial-of-service attack on phone users, blocking targeted people from making or receiving calls. As per analysts from the information security industry, the approximate cost of Gossamer type devices in black market is 10,000 to 20,000 USD depending upon the state of device and features of the device in counties like Mexico, Brazil and Argentina.
Triggerfish like devices
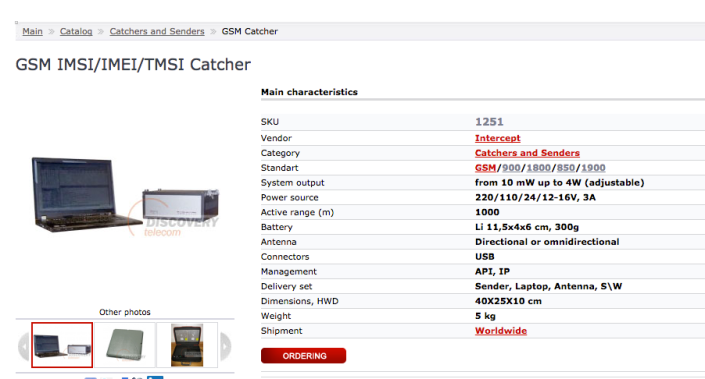
The Triggerfish is an eavesdropping device. With it anybody can intercept calls, messages in real time in the targeted area. It allows all the functions of stingray. Some advance Russian versions of Triggerfish can intercept calls, SMS of 10,0000 mobile phones in the targeted area of city.
Kingfish like Devices

The Kingfish is a device that allows anybody to track and analyze information from mobile phones over a targeted area. It is smaller stingray devices but it can give you the list of connections between different phones. This device can be controlled wirelessly to monitor communications.
Harpoon like Devices
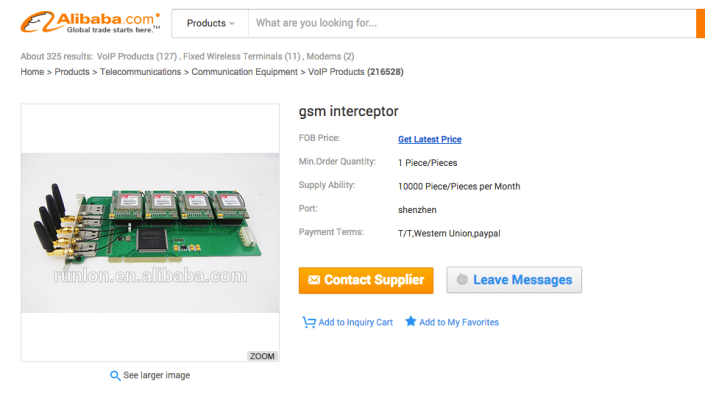
The Harpoon is an amplifier device that is used to boost the signal of a Stingray or Kingfish device, so that a big area can be monitored and more mobile phone can be tracked more safely from very far way. The cost of the harpoon like Russian amplifiers is around 15,000 USD in black market.
3G (UMTS) networks GSM interceptor

This device automatically scans and detects parameters of all 3G networks in the range. Intercept 3G communications and data. Detects all 3G phones and collect all their identities (IMSI, IMEI and TMSI). This device selectively blocks 3G communications of target’s phones. Also advance version of this device can take control of mobile devices completely to send and receive Spoof 3G related calls and data as per ethical hacking experts.
HOW TO CREATE YOUR GSM INTERCEPTOR / STINGRAY
You can create your own GSM interceptor / stingray like device as per professor who teaches this during mobile ethical hacking training .
WHAT WE NEED
BSC(base station controller) is the brain for BTS. It is the decision-making device and it decides switching among different BTS. Also it doses switching of calls. The interface between BSC and BTS is called GSM A-bis interface.
In our case we will use OpenBTS software to configure our software defined radio (SDR) platform which are basic radio set with can work as radio or with help of OpenBTS and Linux we can convert it into a OpenBTS. We will also use Asterisk Server, which help in call switching and is very easy to configure as BSC.
- OpenBTS is open source software
- Asterisk Server is also a open source
- Linux as we all know is also open source.
- Software defined radio (SDR) platform is a hardware which will cost you around 500- 1000 USD.
HOW IT WORKS
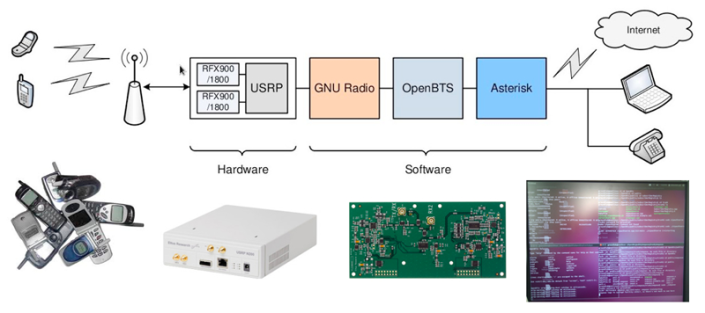
BTS verifies to which mobile device it’s connecting but the mobile device doesn’t verify the identity of mobile network BTS it is connecting. Because handsets always choose the strongest signal, so if there is a new BTS with stronger signal the mobile phone will connect to it always. In GSM the BTS decides to enable encryption or not so our new OpenBTS station will be not use encryption to we can listen to all the calls and sms. The IMSI catcher does have to not break GSM encryption; it just acts as a base station and tells the phone to disable GSM encryption.
In order to spoof a network we will need some information: the mobile country code, the mobile network code and the network name. All this data can be easily found on Internet and we can program our OpenBTS with these values and configure IUSACELL o any network. After configuring these settings in our BTS the mobile phones within the range will start connecting to our OpenBTS .
We will also configure Asterisk Server, which will act as a call switching software and also help us in listing to calls in real time or may be recording them. You can learn configuring your own mobile network during ethical hacking courses of iicybersecurity.
This article is for only educational purposes only. Below the video of GSM hacker Chris Paget, shows actually how the final setup will look like
You can download asterisk platform free from
http://www.asterisk.org/downloads
Learn more about OpenBTS and how to configure it
http://openbts.org/w/index.php/OpenBTS-UMTS
Source:http://www.iicybersecurity.com/intercept-mobile-communications.html



May 24, 2015 at 11:15 pm
[…] Fonte: Instituto Internacional de Seguridad Cibernética […]